SQL Server Threats – Sqlservercentral.com
Published on: 2025-08-07
Intelligence Report: SQL Server Threats – Sqlservercentral.com
1. BLUF (Bottom Line Up Front)
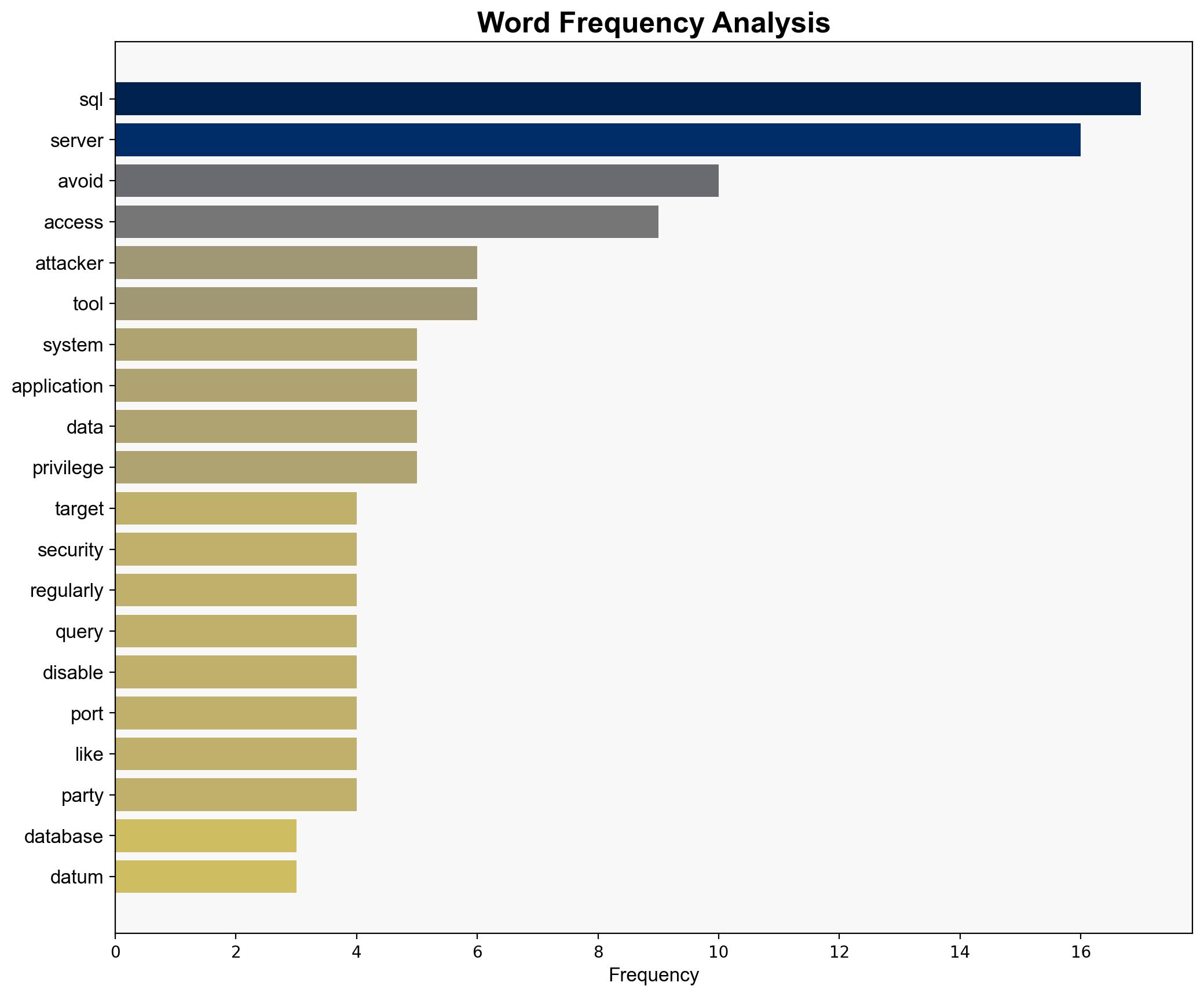
The most supported hypothesis is that SQL Server environments are increasingly vulnerable due to a combination of outdated software, weak access controls, and misconfigurations. This vulnerability is exacerbated by sophisticated cybercriminal tactics. Confidence level: High. Recommended action includes immediate implementation of robust security protocols, regular updates, and comprehensive monitoring systems.
2. Competing Hypotheses
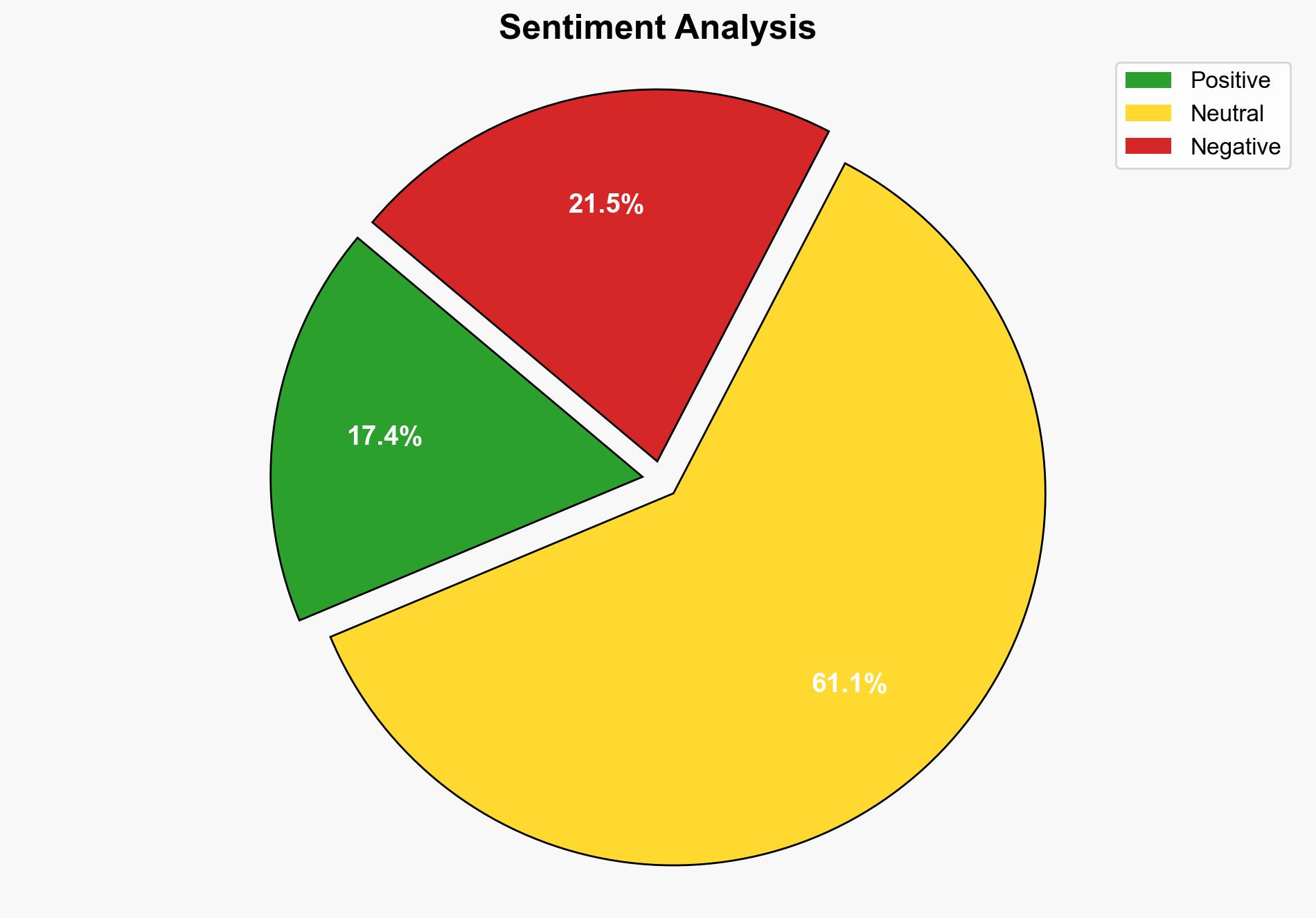
Hypothesis 1: SQL Server threats primarily arise from external cybercriminal activities exploiting known vulnerabilities and misconfigurations.
Hypothesis 2: The primary threat to SQL Server environments is internal, stemming from insider threats and inadequate internal security practices.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the prevalence of external attack vectors such as SQL injection, brute force attacks, and unpatched vulnerabilities highlighted in the source. Hypothesis 2, while plausible, is less supported due to the lack of specific insider threat examples in the source.
3. Key Assumptions and Red Flags
Assumptions:
– Organizations are not consistently applying patches and updates to SQL Server environments.
– External threat actors have the capability and intent to exploit SQL Server vulnerabilities.
Red Flags:
– Lack of specific data on insider threats could indicate a blind spot.
– Over-reliance on external threat data may obscure internal vulnerabilities.
4. Implications and Strategic Risks
The failure to address SQL Server vulnerabilities could lead to significant data breaches, financial losses, and reputational damage. There is a risk of cascading effects if compromised SQL Servers are used as entry points for broader network attacks. Geopolitically, state-sponsored actors could exploit these vulnerabilities for espionage or sabotage.
5. Recommendations and Outlook
- Implement a comprehensive patch management program to ensure all SQL Server instances are up-to-date.
- Adopt multi-factor authentication and strong password policies to mitigate unauthorized access.
- Conduct regular security audits and penetration testing to identify and rectify vulnerabilities.
- Scenario Projections:
- Best Case: Organizations implement robust security measures, significantly reducing SQL Server vulnerabilities.
- Worst Case: Continued neglect leads to widespread breaches, causing severe economic and reputational damage.
- Most Likely: Incremental improvements in security practices reduce but do not eliminate threats.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus is on organizations using SQL Server and potential threat actors.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus