Secure Your eLearning Software 10 Steps To Lock It Down Before Launch – Elearningindustry.com
Published on: 2025-08-07
Intelligence Report: Secure Your eLearning Software 10 Steps To Lock It Down Before Launch – Elearningindustry.com
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the outlined security measures are essential for mitigating cybersecurity risks associated with launching eLearning platforms. The confidence level in this assessment is moderate, given the comprehensive nature of the proposed steps. It is recommended to implement these measures to enhance security posture and protect sensitive data. Continuous monitoring and updates are crucial to adapt to evolving threats.
2. Competing Hypotheses
1. **Hypothesis A**: The security measures outlined are sufficient to protect an eLearning platform from most cyber threats, ensuring a secure launch.
2. **Hypothesis B**: Despite the comprehensive security measures, the platform remains vulnerable to sophisticated cyber threats due to potential implementation gaps or evolving threat landscapes.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported by the detailed steps provided, which cover a wide range of security aspects from authentication to data encryption and incident response planning. However, Hypothesis B cannot be entirely dismissed due to the dynamic nature of cybersecurity threats.
3. Key Assumptions and Red Flags
– **Assumptions**: The measures assume that all steps will be implemented correctly and consistently. It also assumes that the threat landscape remains static.
– **Red Flags**: The absence of specific threat intelligence or recent case studies raises concerns about the applicability of these measures to current threats. There is also a lack of discussion on insider threats and social engineering.
4. Implications and Strategic Risks
Failure to implement robust security measures could lead to data breaches, reputational damage, and financial losses. The increasing sophistication of cyber threats poses a risk of cascading failures if initial breaches are not contained. The economic impact could extend to loss of trust and reduced user engagement. Geopolitically, inadequate security could expose platforms to exploitation by state-sponsored actors.
5. Recommendations and Outlook
- Implement the outlined security measures with a focus on continuous monitoring and updates.
- Conduct regular security audits and penetration testing to identify and address vulnerabilities.
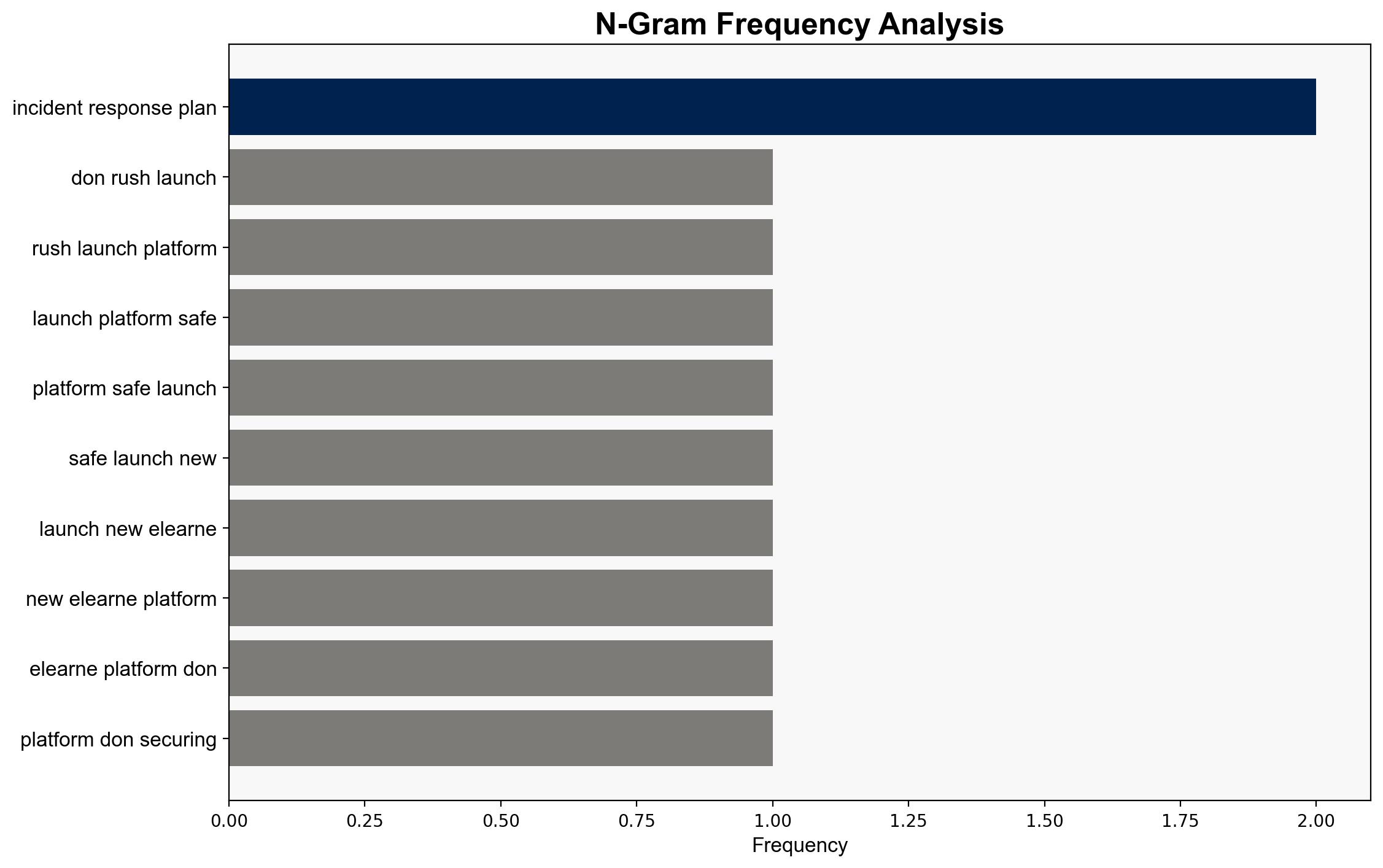
- Develop a robust incident response plan and conduct drills to ensure preparedness.
- Scenario Projections:
- Best Case: Successful implementation leads to a secure launch with minimal incidents.
- Worst Case: Security measures fail, resulting in a significant breach and data loss.
- Most Likely: Initial minor incidents occur, but are quickly contained due to proactive measures.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus is on entities involved in eLearning platform development and cybersecurity.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus