New WinRAR Zero-Day Exploited by RomCom Hackers – Infosecurity Magazine
Published on: 2025-08-11
Intelligence Report: New WinRAR Zero-Day Exploited by RomCom Hackers – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
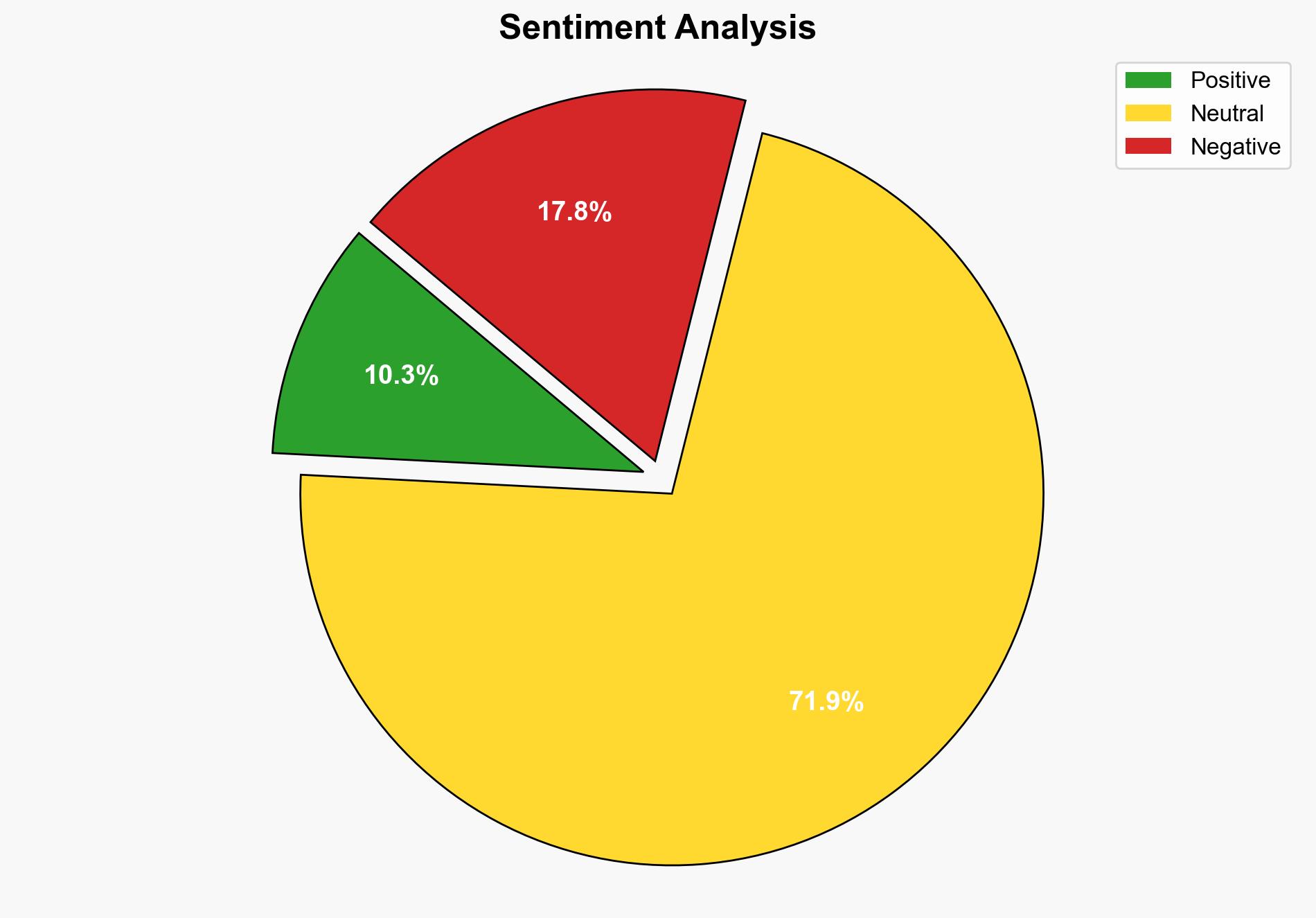
The RomCom cyber group is exploiting a zero-day vulnerability in WinRAR, potentially targeting sectors in Europe and Canada. The most supported hypothesis is that RomCom is leveraging this vulnerability for espionage and financial gain. Immediate patching of affected systems is recommended to mitigate risks. Confidence level: Moderate.
2. Competing Hypotheses
Hypothesis 1: RomCom is exploiting the WinRAR vulnerability primarily for espionage purposes, targeting sensitive sectors to gather intelligence.
Hypothesis 2: RomCom’s primary objective is financial gain, using the vulnerability to deploy ransomware or steal financial data from targeted organizations.
Using ACH 2.0, Hypothesis 1 is better supported due to the pattern of targeting sectors like defense and logistics, which align more with espionage activities. The use of spear-phishing and advanced techniques like anti-analysis also suggests a focus on intelligence gathering.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that RomCom has the capability to exploit the vulnerability effectively and that their targets are unaware of the specific threat.
Red Flags: The rapid exploitation following the vulnerability’s discovery suggests possible insider knowledge or advanced reconnaissance capabilities. The lack of detailed attribution to RomCom raises questions about potential misdirection.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant data breaches, impacting national security and economic stability in targeted regions. If RomCom’s activities are state-sponsored, this could escalate geopolitical tensions. The persistence of such vulnerabilities highlights the need for robust cybersecurity frameworks.
5. Recommendations and Outlook
- Immediate update and patching of WinRAR installations across all vulnerable systems.
- Enhanced monitoring for spear-phishing campaigns and unusual network activity.
- Scenario Projections:
- Best Case: Rapid patch deployment prevents further exploitation, minimizing impact.
- Worst Case: Widespread data breaches lead to significant financial and reputational damage.
- Most Likely: Continued targeted attacks with moderate impact, prompting increased cybersecurity measures.
6. Key Individuals and Entities
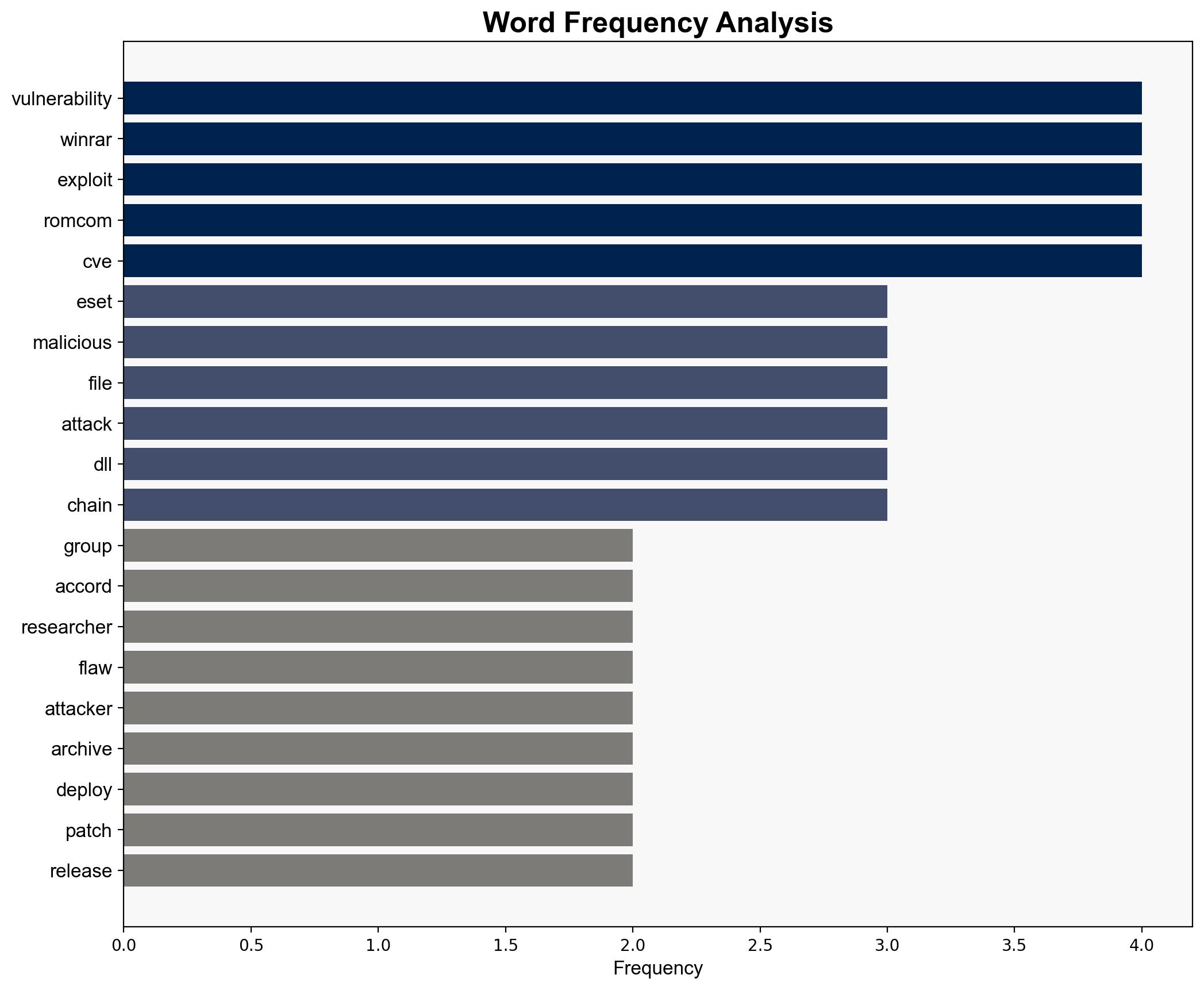
RomCom cyber group, ESET researchers.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus