WinRAR has a serious security flaw – worrying zero-day issue lets hackers plant malware so patch right away – TechRadar
Published on: 2025-08-11
Intelligence Report: WinRAR has a serious security flaw – worrying zero-day issue lets hackers plant malware so patch right away – TechRadar
1. BLUF (Bottom Line Up Front)
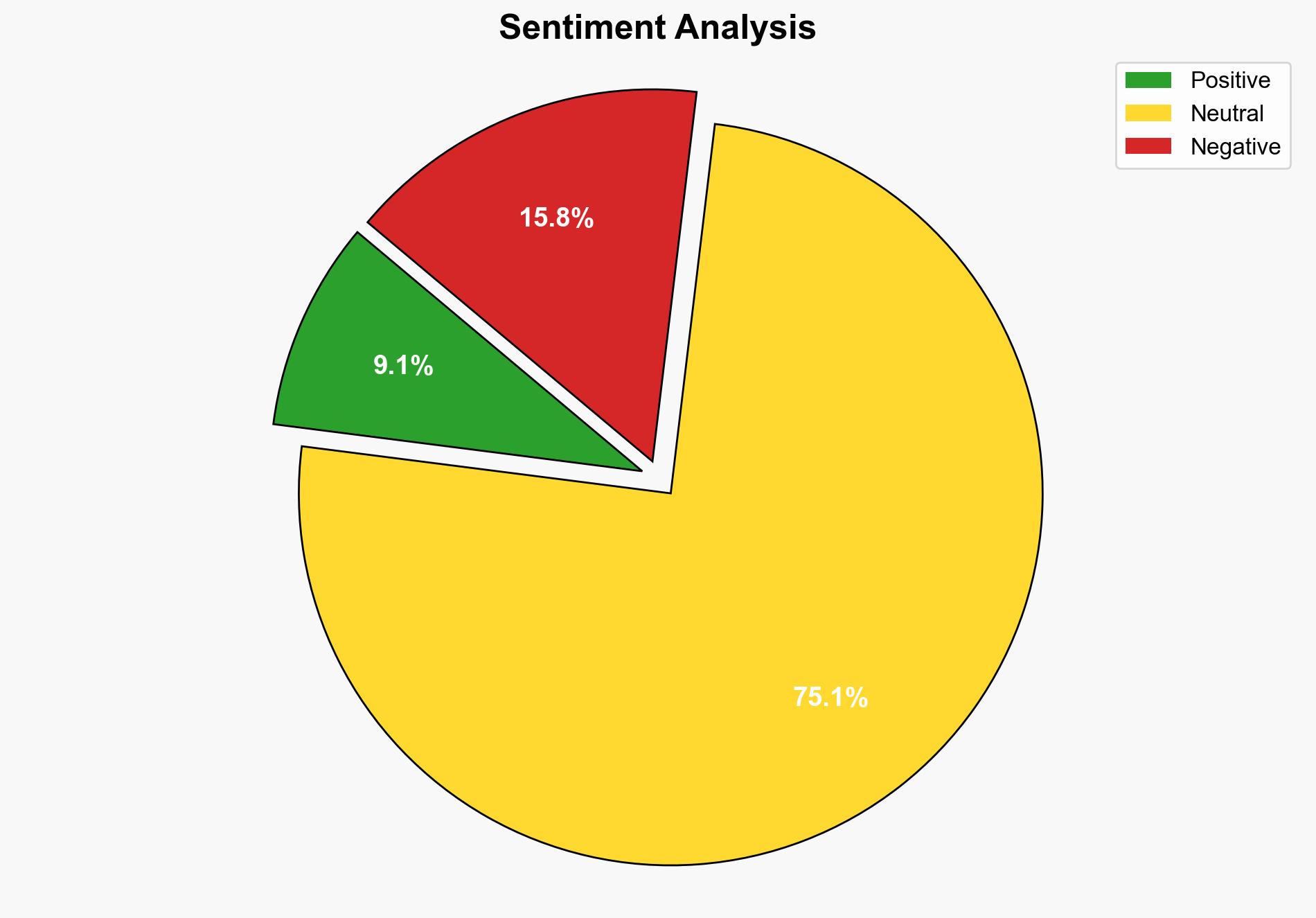
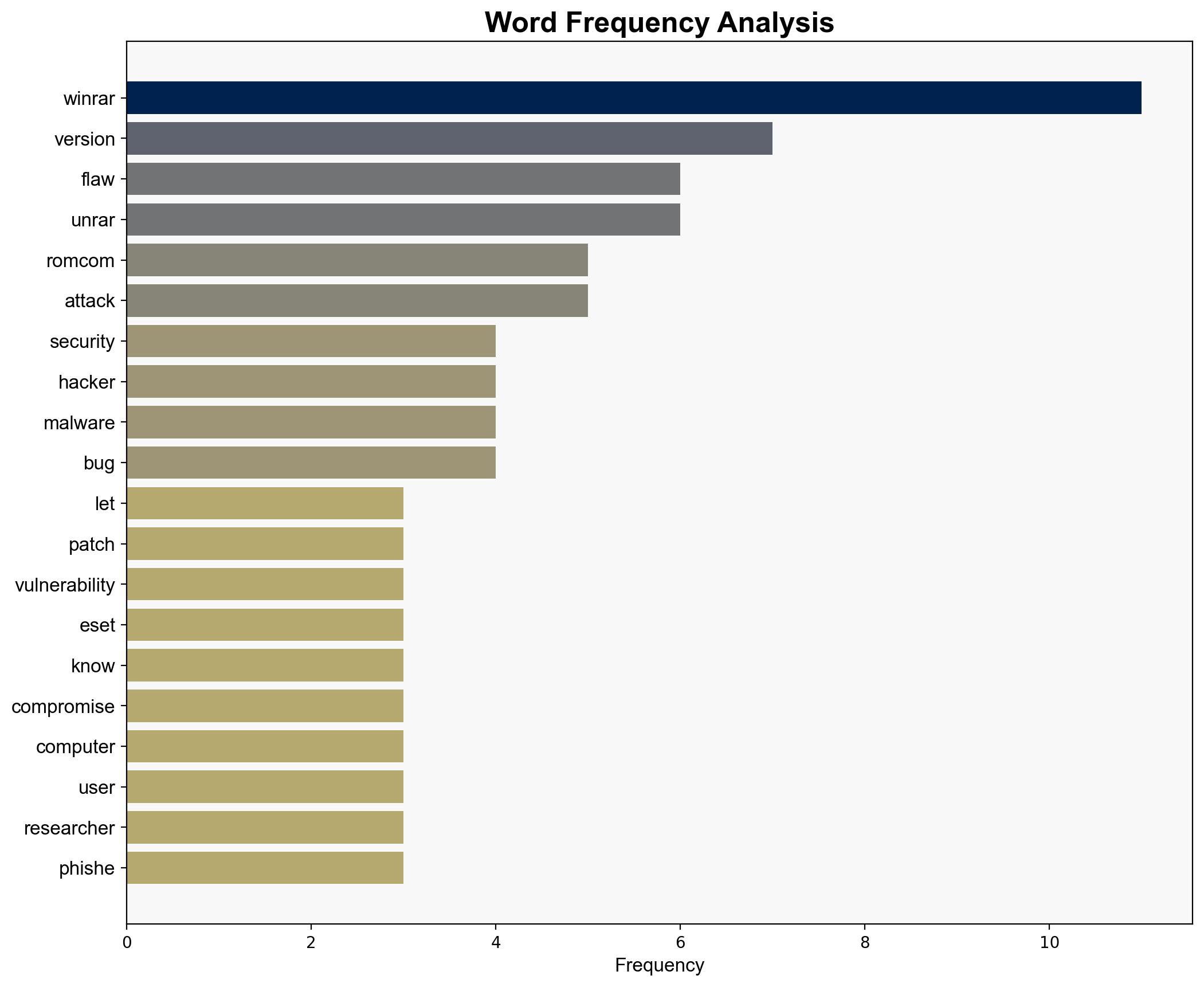
The most supported hypothesis is that the WinRAR zero-day vulnerability is being actively exploited by the RomCom group, a known Russian-speaking threat actor, to conduct espionage and financially motivated attacks. Confidence level is moderate due to the specificity of the threat actor and the nature of the vulnerability. Immediate patching of affected systems is recommended to mitigate risks.
2. Competing Hypotheses
1. **Hypothesis A**: The WinRAR vulnerability is primarily being exploited by the RomCom group to deploy malware for espionage and financial gain. This is supported by the pattern of spear-phishing attacks and the group’s known targets in Europe and North America.
2. **Hypothesis B**: The vulnerability is being exploited by multiple threat actors beyond RomCom, potentially including other state-sponsored groups or independent cybercriminals, given the high severity and widespread use of WinRAR.
Using Analysis of Competing Hypotheses (ACH), Hypothesis A is better supported due to specific mentions of RomCom’s involvement and historical patterns of their operations. However, the possibility of other actors exploiting the flaw cannot be dismissed.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the RomCom group is the primary actor exploiting this vulnerability based on current evidence. It is also assumed that users will not update their software promptly, leaving systems vulnerable.
– **Red Flags**: Lack of detailed evidence on other potential threat actors exploiting the vulnerability. The assumption that RomCom is the sole actor could lead to underestimating the threat landscape.
– **Blind Spots**: Potential for other vulnerabilities in WinRAR or similar software that have not yet been disclosed or discovered.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant data breaches, loss of sensitive information, and financial damage to targeted organizations. The geopolitical dimension involves potential state-sponsored cyber activities, increasing tensions between affected nations and the perceived origin of the threat actors. Economically, widespread exploitation could harm businesses reliant on WinRAR for data management.
5. Recommendations and Outlook
- **Immediate Action**: Urge all users to update WinRAR to the latest patched version to close the vulnerability.
- **Monitoring**: Increase monitoring for spear-phishing campaigns and unusual network activities, particularly in sectors known to be targeted by RomCom.
- **Scenario Projections**:
– **Best Case**: Rapid patch adoption mitigates the majority of potential attacks.
– **Worst Case**: Slow patch adoption leads to widespread exploitation and significant data breaches.
– **Most Likely**: A moderate level of exploitation continues until patch adoption reaches a critical mass.
6. Key Individuals and Entities
– RomCom group (Russian-speaking threat actor)
– ESET (security researchers who discovered the vulnerability)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus