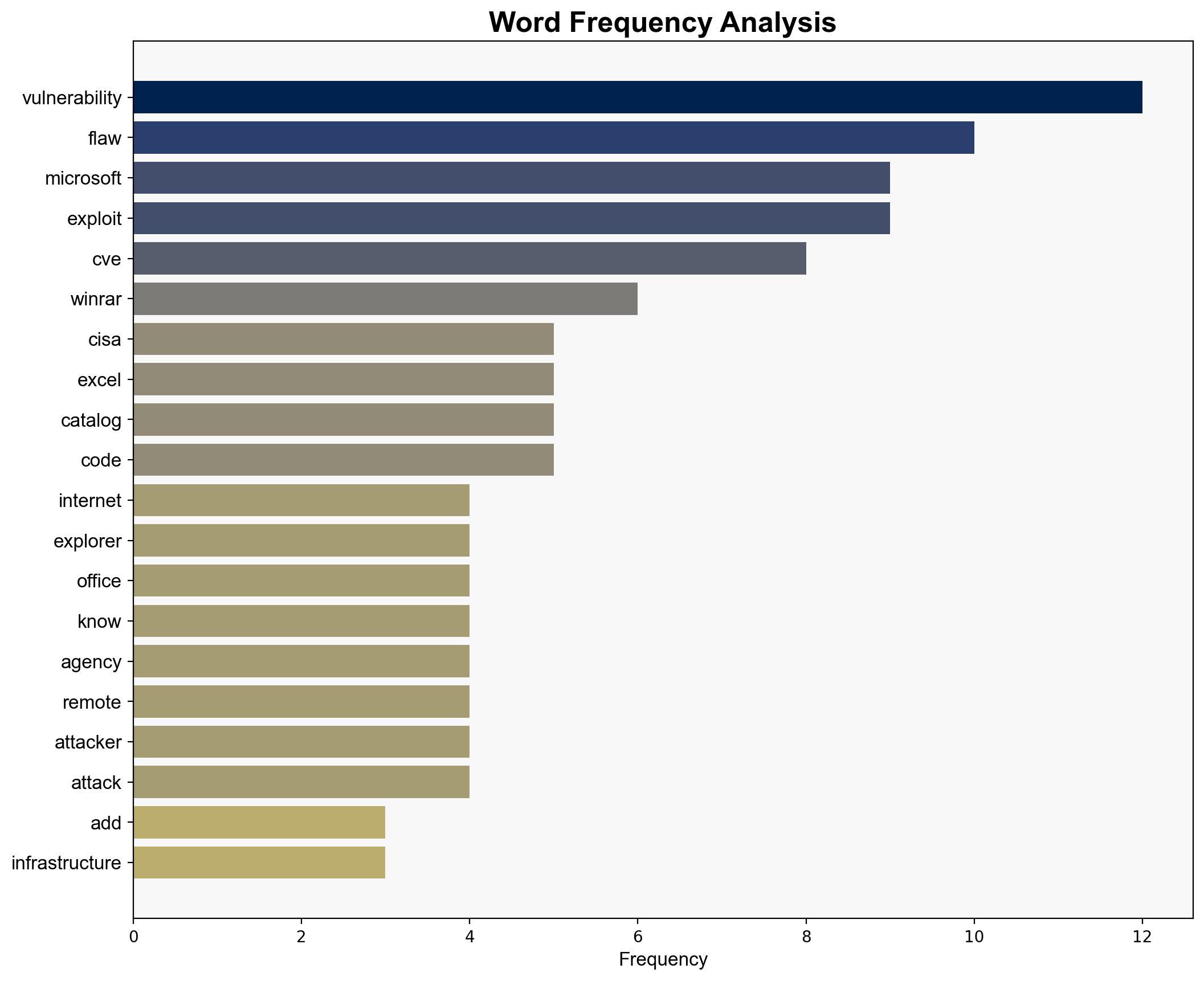
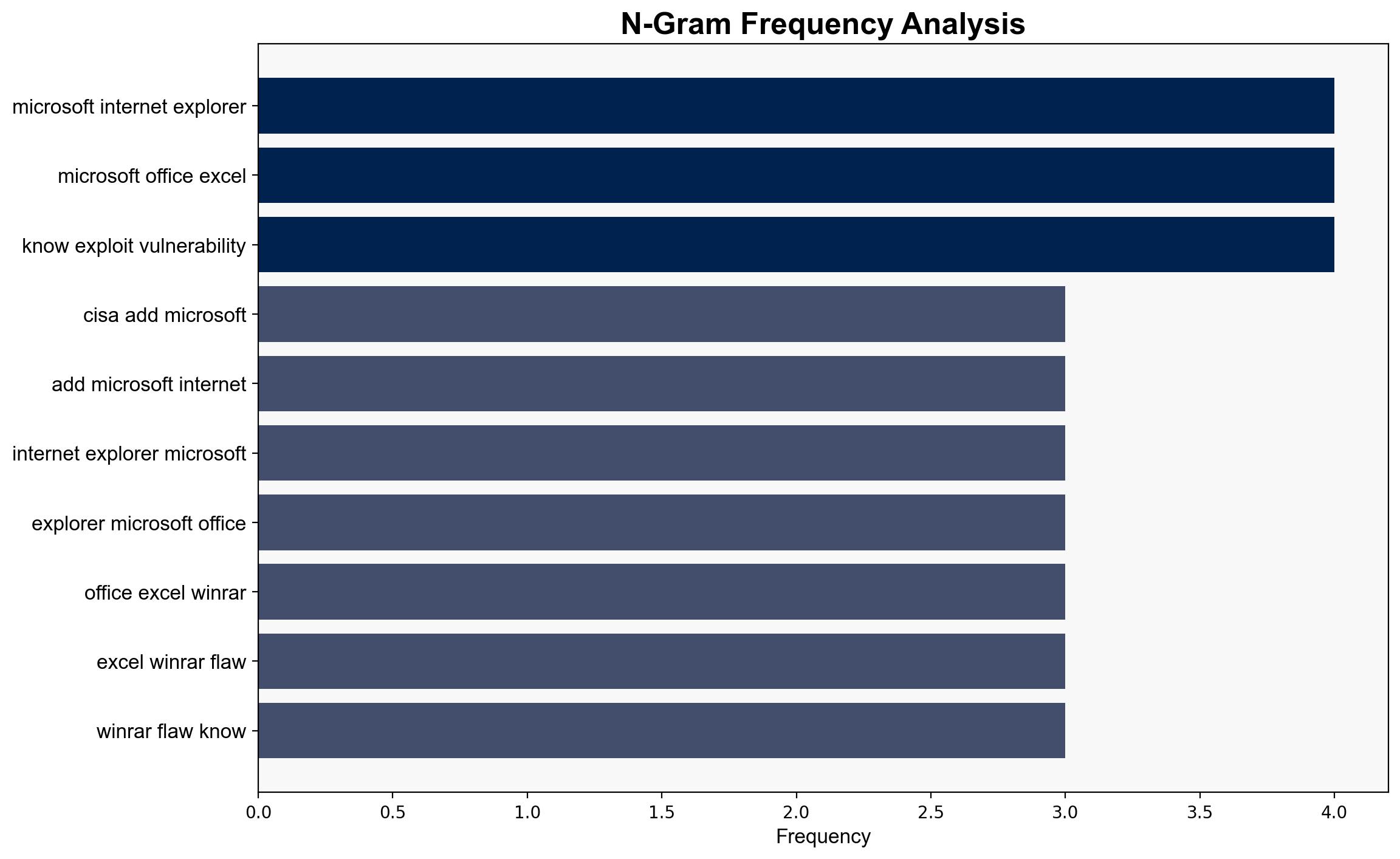
US CISA adds Microsoft Internet Explorer Microsoft Office Excel and WinRAR flaws to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
Published on: 2025-08-14
Intelligence Report: US CISA adds Microsoft Internet Explorer Microsoft Office Excel and WinRAR flaws to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
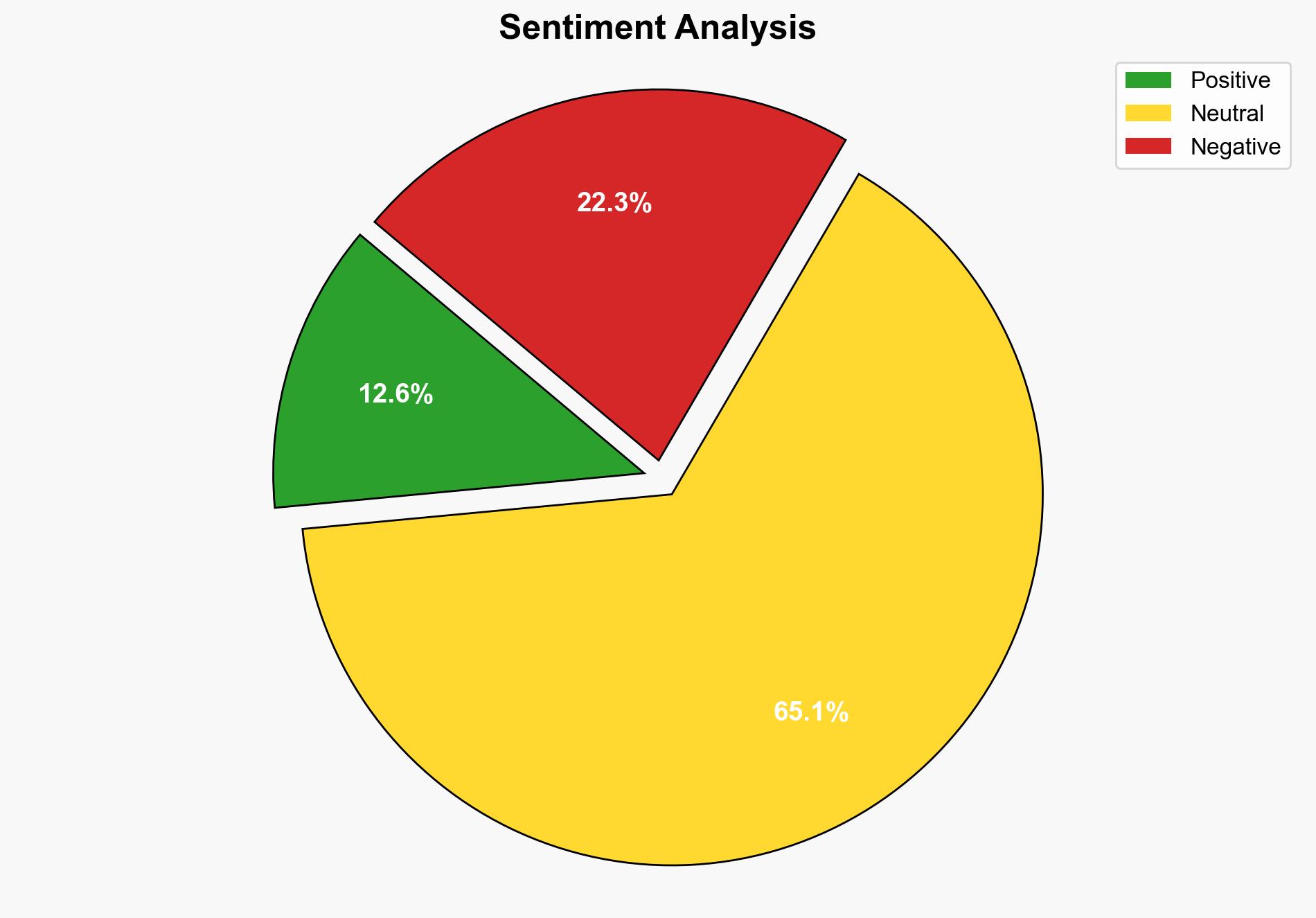
The addition of vulnerabilities in Microsoft Internet Explorer, Microsoft Office Excel, and WinRAR to the CISA Known Exploited Vulnerabilities catalog highlights significant cybersecurity risks. The most supported hypothesis suggests that these vulnerabilities are being actively exploited by threat actors to conduct targeted attacks, potentially impacting both federal and private sectors. Confidence level: High. Recommended action: Immediate patching and enhanced monitoring of network activities.
2. Competing Hypotheses
Hypothesis 1: The vulnerabilities are being actively exploited by sophisticated threat actors targeting specific entities for espionage or financial gain. This is supported by reports of zero-day exploits and spear-phishing attacks delivering malware like RomCom.
Hypothesis 2: The vulnerabilities are primarily being exploited opportunistically by a wide range of cybercriminals, with no specific targeting, aiming to maximize the spread of malware for broader financial gains.
Using ACH 2.0, Hypothesis 1 is better supported due to the specificity of the attacks mentioned (e.g., spear-phishing and targeted malware delivery), indicating a strategic intent rather than random exploitation.
3. Key Assumptions and Red Flags
Assumptions:
– The vulnerabilities are known and have been publicly disclosed, increasing the likelihood of exploitation.
– Threat actors have the capability to exploit these vulnerabilities effectively.
Red Flags:
– Lack of detailed attribution to specific threat actors, which could indicate either a lack of intelligence or deliberate obfuscation by the attackers.
– Potential underreporting of affected entities, leading to an incomplete threat landscape.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities poses risks to national security, economic stability, and public trust in digital infrastructure. Potential escalation includes increased cyber espionage activities, disruption of critical services, and financial losses. The geopolitical dimension involves potential attribution to state-sponsored actors, which could heighten tensions between nations.
5. Recommendations and Outlook
- Immediate patching of affected systems and enhanced monitoring for signs of exploitation.
- Conduct awareness campaigns to educate users on recognizing phishing attempts.
- Scenario-based projections:
- Best Case: Rapid patch deployment and user education mitigate the majority of threats.
- Worst Case: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most Likely: Continued targeted attacks with periodic successful breaches, primarily affecting unpatched systems.
6. Key Individuals and Entities
– Anton Cherepanov, Peter Koinr, Peter Strek (Researchers at ESET)
– FireEye (Security firm uncovering exploitation operations)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus