Elastic response to blog EDR 0-Day Vulnerability – Elastic.co
Published on: 2025-08-18
Intelligence Report: Elastic response to blog EDR 0-Day Vulnerability – Elastic.co
1. BLUF (Bottom Line Up Front)
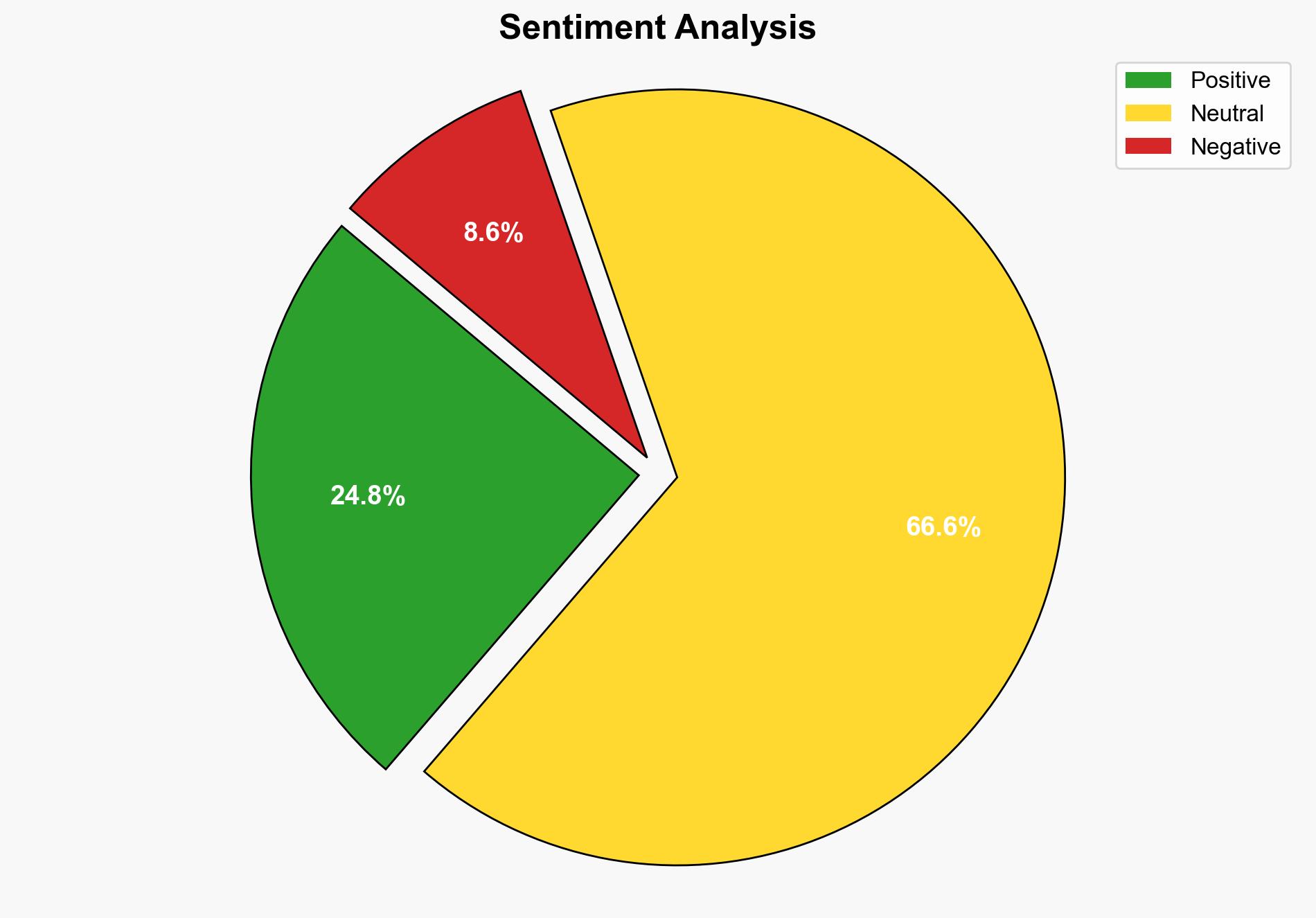
The most supported hypothesis is that the alleged vulnerability in Elastic’s EDR system is either non-existent or significantly exaggerated. This conclusion is based on the lack of evidence provided by the researcher and Elastic’s inability to reproduce the exploit. Confidence level: Moderate. Recommended action: Continue monitoring for further developments and encourage the researcher to engage in coordinated disclosure.
2. Competing Hypotheses
1. **Hypothesis A:** The alleged vulnerability is genuine and poses a significant risk, but Elastic’s current investigation methods are insufficient to detect it.
2. **Hypothesis B:** The alleged vulnerability is either non-existent or exaggerated, and the claims lack substantiated evidence.
Using ACH 2.0, Hypothesis B is better supported due to the absence of reproducible proof and Elastic’s comprehensive security measures that align with industry standards.
3. Key Assumptions and Red Flags
– **Assumptions:** Elastic’s security protocols are robust and capable of identifying genuine threats. The researcher’s refusal to provide proof is due to either a lack of evidence or a strategic decision to withhold information.
– **Red Flags:** The refusal to share a reproducible proof of concept raises questions about the credibility of the claims. The public disclosure without prior coordination suggests potential motives beyond security concerns.
4. Implications and Strategic Risks
If the vulnerability is genuine and remains undetected, it could lead to significant cybersecurity risks, including unauthorized access and data breaches. This could damage Elastic’s reputation and customer trust. Conversely, if the claims are unfounded, it highlights the challenges of managing public perception and the importance of coordinated disclosure practices.
5. Recommendations and Outlook
- Encourage the researcher to engage in coordinated disclosure to validate the claims.
- Enhance communication with the security community to prevent similar situations.
- Scenario Projections:
- Best Case: The claims are unfounded, and Elastic’s reputation is strengthened by transparent handling.
- Worst Case: A genuine vulnerability is confirmed, leading to significant security breaches.
- Most Likely: The claims are exaggerated, and no significant vulnerability is found.
6. Key Individuals and Entities
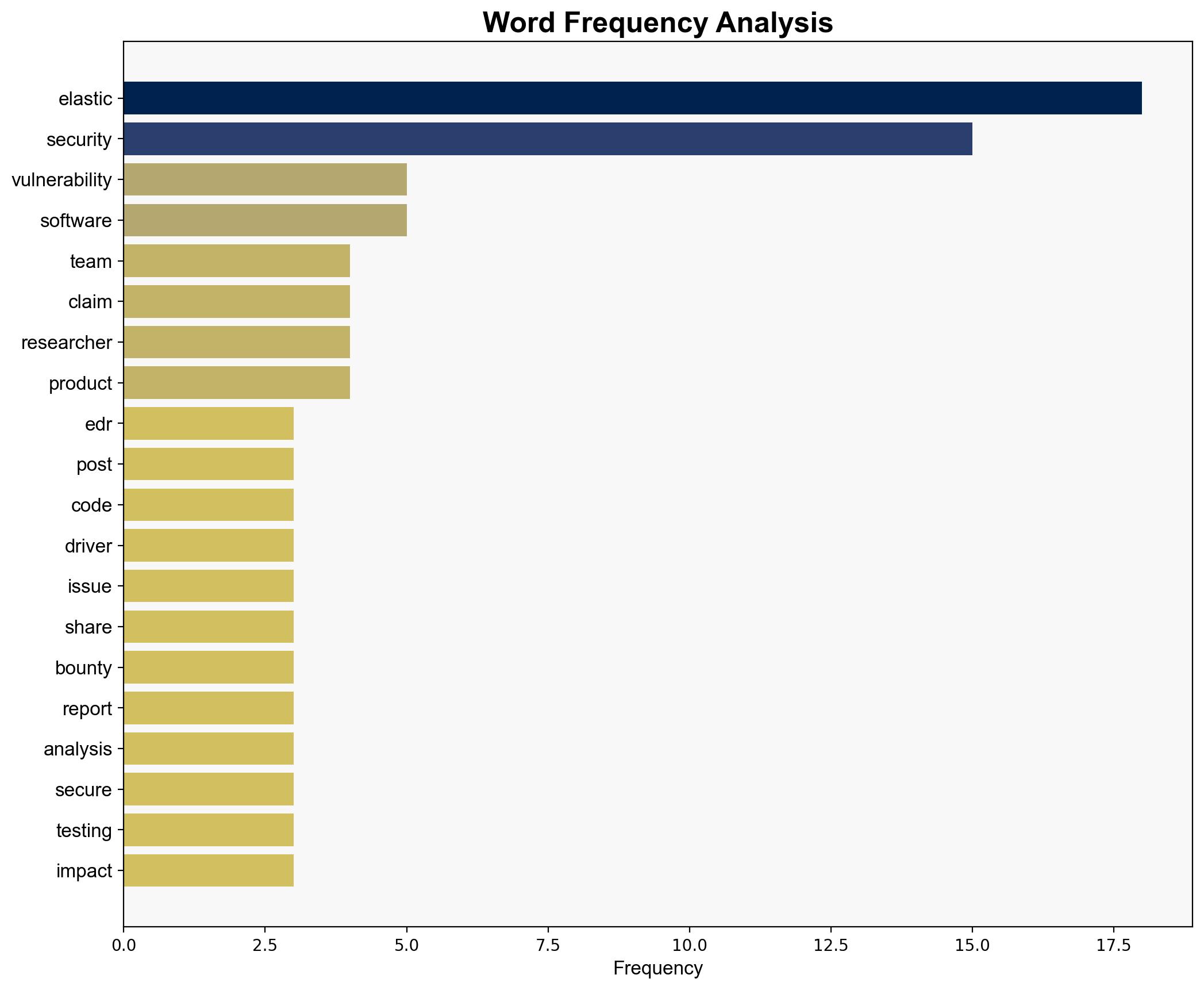
Elastic’s security engineering team, the unnamed researcher making the vulnerability claim.
7. Thematic Tags
cybersecurity, vulnerability management, coordinated disclosure, software security