Taiwan Air Force officer gets 7 years for leaking documents to China – Globalsecurity.org
Published on: 2025-08-23
Intelligence Report: Taiwan Air Force officer gets 7 years for leaking documents to China – Globalsecurity.org
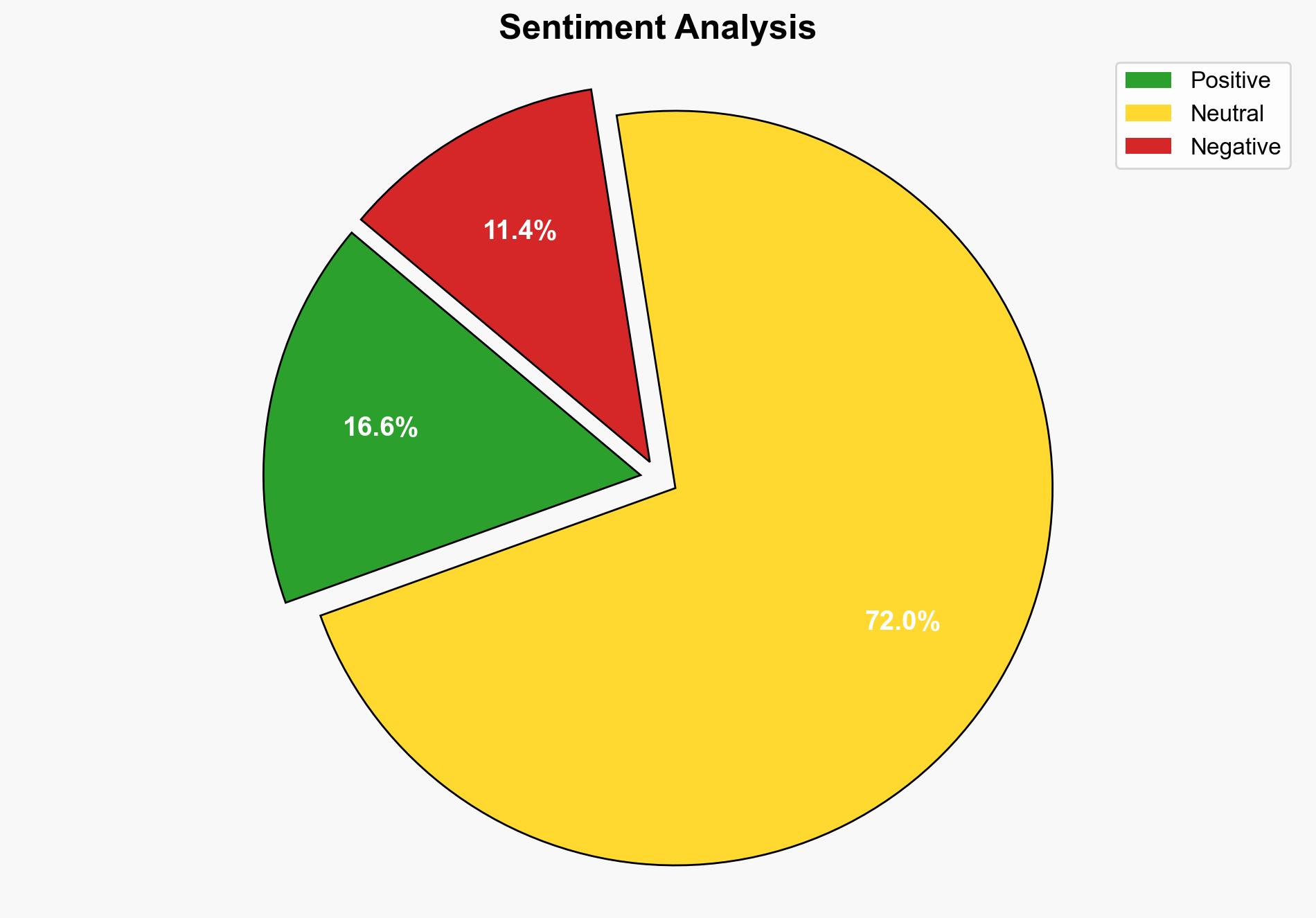
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the leak was part of a broader Chinese intelligence strategy to exploit vulnerabilities within Taiwan’s military for strategic advantage. Confidence Level: High. Recommended action includes enhancing counterintelligence measures and increasing monitoring of military personnel with access to sensitive information.
2. Competing Hypotheses
1. **Hypothesis A**: The leak was an isolated incident driven by personal financial gain, with no broader strategic implications.
2. **Hypothesis B**: The leak was part of a systematic Chinese intelligence operation targeting Taiwanese military personnel to gather strategic military intelligence.
Using ACH 2.0, Hypothesis B is better supported due to the involvement of a retired major, the systematic nature of the recruitment, and the strategic value of the leaked documents.
3. Key Assumptions and Red Flags
– **Assumptions**: Hypothesis A assumes that financial incentives alone motivated the officer, ignoring potential ideological or coercive factors. Hypothesis B assumes a coordinated Chinese effort, which requires evidence of broader patterns.
– **Red Flags**: The limited payment received by Hsu suggests possible deception or incomplete reporting. The role of the retired major indicates potential systemic issues in managing retired personnel.
– **Blind Spots**: Lack of information on how widespread such recruitment efforts are and the full extent of the compromised information.
4. Implications and Strategic Risks
– **Patterns**: This incident may indicate a broader Chinese strategy to infiltrate Taiwan’s military, posing significant national security threats.
– **Cascading Threats**: Potential for compromised operational security and strategic planning, leading to increased military vulnerability.
– **Escalation Scenarios**: If unchecked, such intelligence breaches could lead to heightened tensions and military confrontations.
– **Economic and Cyber Dimensions**: Potential for increased cyber espionage and economic pressure tactics from China.
5. Recommendations and Outlook
- Enhance counterintelligence training and vetting processes for military personnel.
- Implement stricter controls and monitoring of retired military personnel with access to sensitive information.
- Increase collaboration with international allies to share intelligence on Chinese espionage tactics.
- Scenario Projections:
- Best: Strengthened counterintelligence measures prevent future breaches.
- Worst: Continued leaks lead to significant military and strategic disadvantages.
- Most Likely: Incremental improvements in security, with occasional breaches still occurring.
6. Key Individuals and Entities
– Hsu Chan-cheng: Convicted officer.
– Shih Chun-cheng: Retired major involved in recruitment.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus