Pakistan-linked APT36 abuses Linux desktop files to drop custom malware in new campaign – Securityaffairs.com
Published on: 2025-08-25
Intelligence Report: Pakistan-linked APT36 abuses Linux desktop files to drop custom malware in new campaign – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
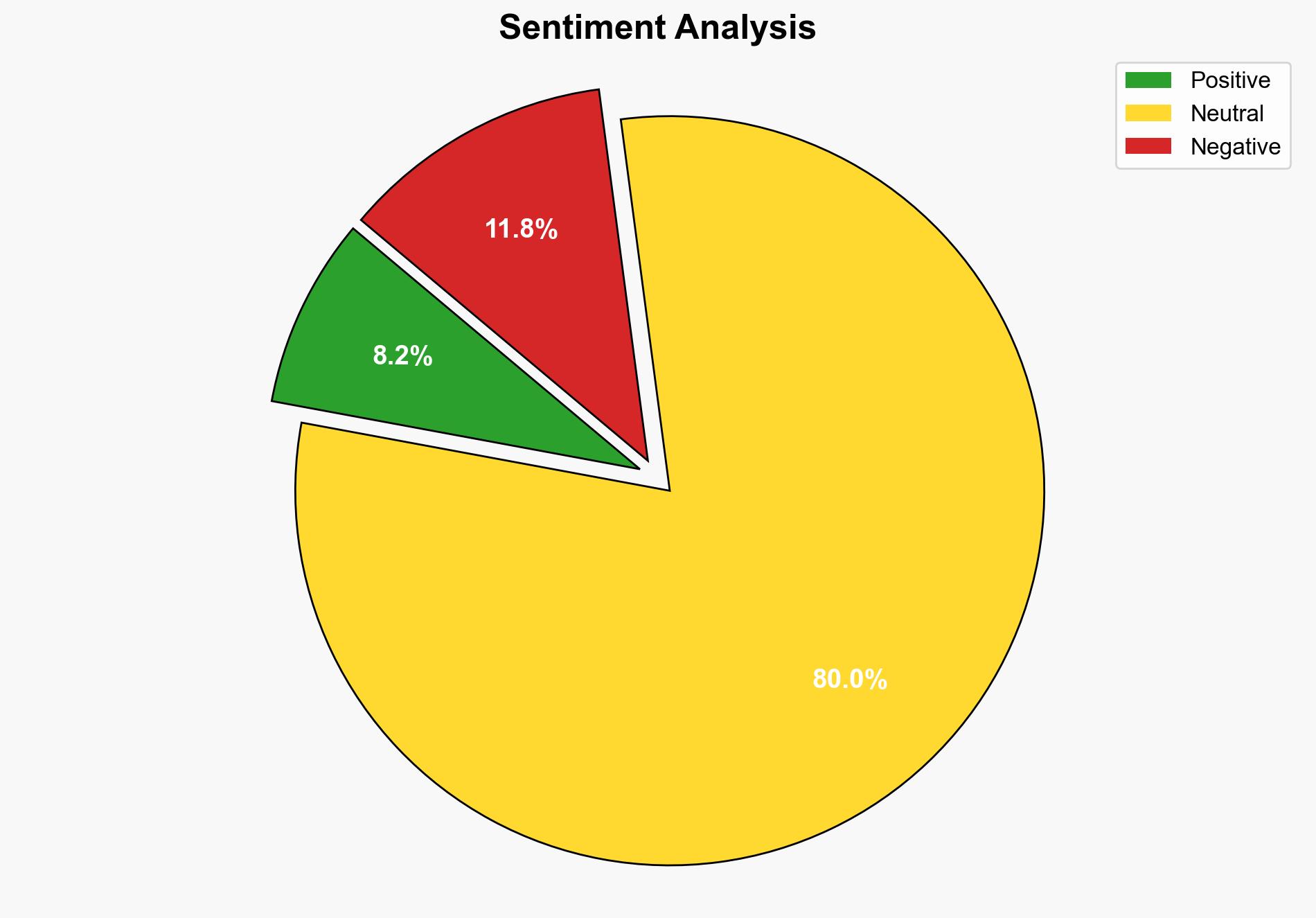
APT36, a Pakistan-linked threat actor, is deploying a new malware campaign targeting Indian government and defense entities using Linux desktop files. The most supported hypothesis is that this campaign aims to diversify attack vectors and enhance persistence. Confidence level is moderate due to the complexity and evolving nature of the threat. Recommended action includes strengthening cybersecurity measures across potential target sectors and enhancing cross-border intelligence sharing.
2. Competing Hypotheses
Hypothesis 1: APT36 is expanding its technical capabilities by incorporating Linux-based malware to diversify attack vectors and ensure persistence in targeted systems. This reflects a strategic shift to exploit less protected systems and increase the campaign’s stealth and effectiveness.
Hypothesis 2: The campaign is primarily a deception operation aimed at misdirecting attribution and creating geopolitical tension between India and Pakistan. The use of Linux-based malware is a red herring to obfuscate the true origin and intent of the attacks.
Using Bayesian Scenario Modeling, Hypothesis 1 is better supported due to the technical sophistication and historical patterns of APT36’s operations, which align with a strategic expansion rather than mere deception.
3. Key Assumptions and Red Flags
– **Assumptions:** It is assumed that APT36 has the technical capability to develop and deploy Linux-based malware effectively. Additionally, it is assumed that the primary target remains Indian government entities.
– **Red Flags:** The lack of direct attribution evidence and reliance on circumstantial data could lead to misinterpretation. The potential for false flag operations is a significant concern.
– **Blind Spots:** Limited visibility into the internal decision-making processes of APT36 and potential over-reliance on historical behavior patterns.
4. Implications and Strategic Risks
The campaign could escalate cyber tensions in the region, potentially leading to retaliatory measures by affected states. The diversification into Linux systems suggests a broader attack surface, increasing the risk of collateral damage to civilian infrastructure. Geopolitically, this could strain diplomatic relations and impact regional stability.
5. Recommendations and Outlook
- Enhance cybersecurity protocols, particularly focusing on Linux systems within government and defense sectors.
- Increase collaboration with international cybersecurity agencies to develop a comprehensive threat intelligence framework.
- Scenario Projections:
- Best Case: Enhanced defenses successfully mitigate the threat, and diplomatic channels reduce tensions.
- Worst Case: Escalation of cyberattacks leads to significant geopolitical conflict and economic disruption.
- Most Likely: Continued low-level cyber engagements with periodic escalations.
6. Key Individuals and Entities
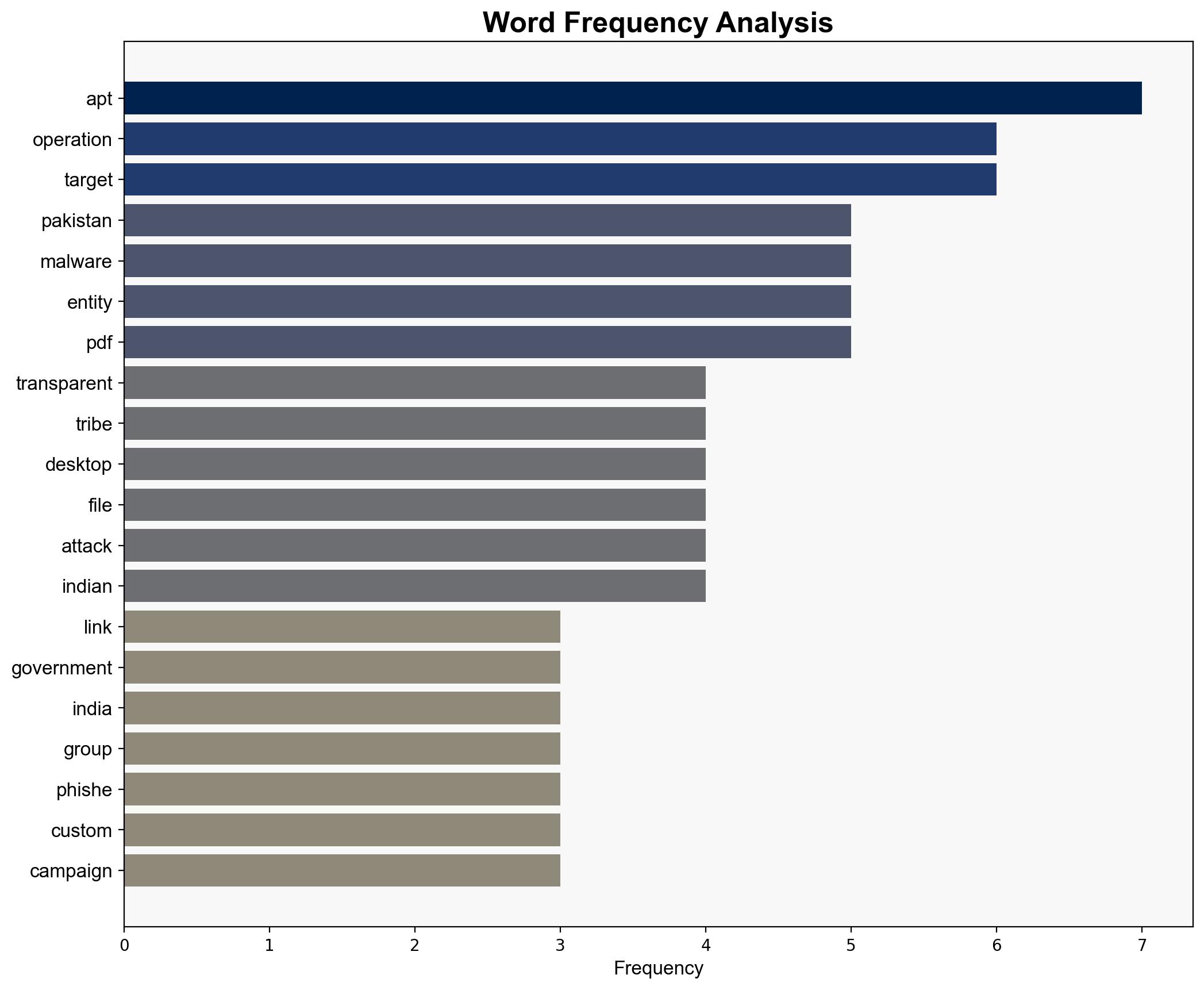
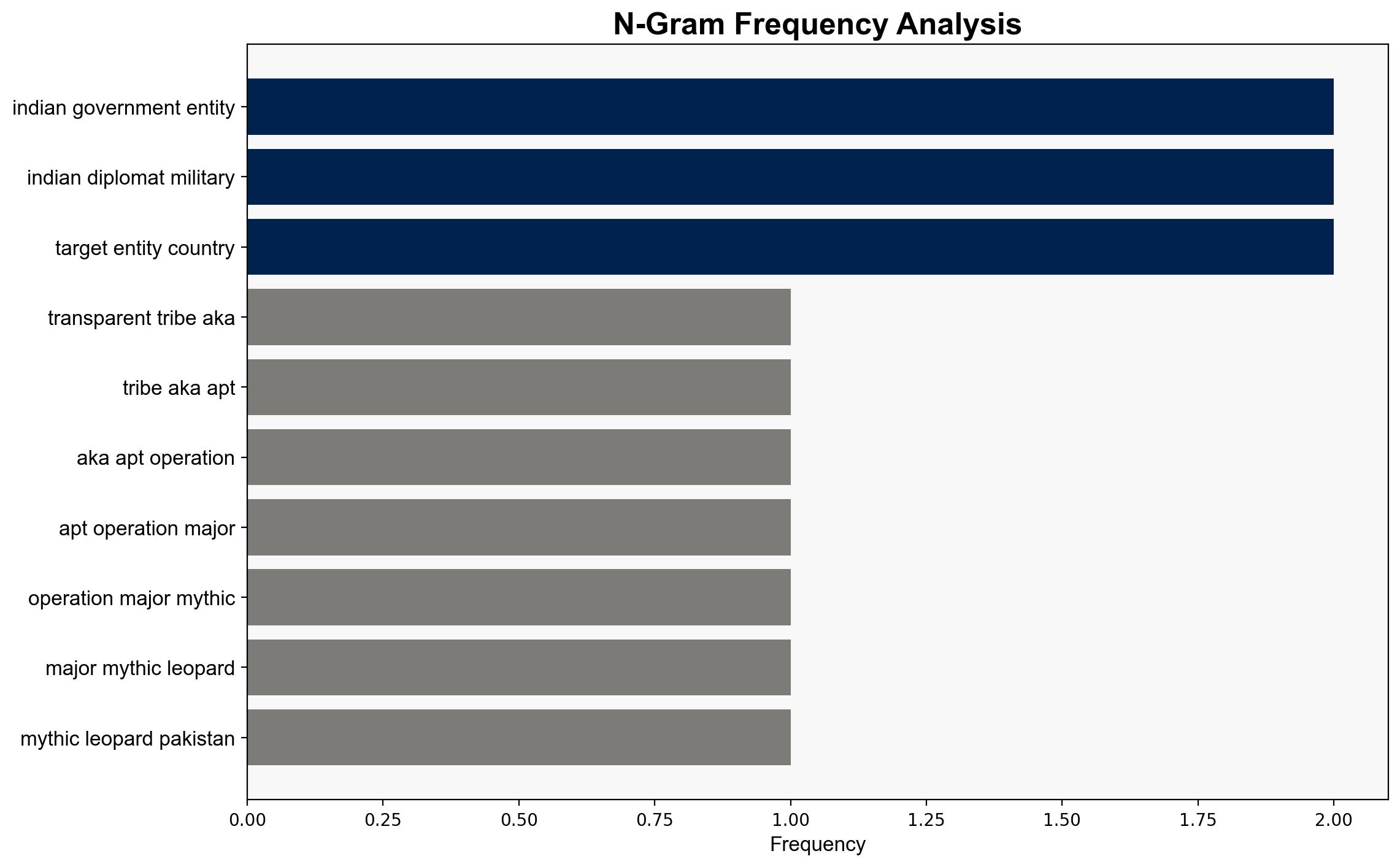
– APT36 (Transparent Tribe)
– Indian Government Entities
– Proofpoint Researchers
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus