Chinese Tech Firms Linked to Salt Typhoon Espionage Campaigns – Infosecurity Magazine
Published on: 2025-08-28
Intelligence Report: Chinese Tech Firms Linked to Salt Typhoon Espionage Campaigns – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
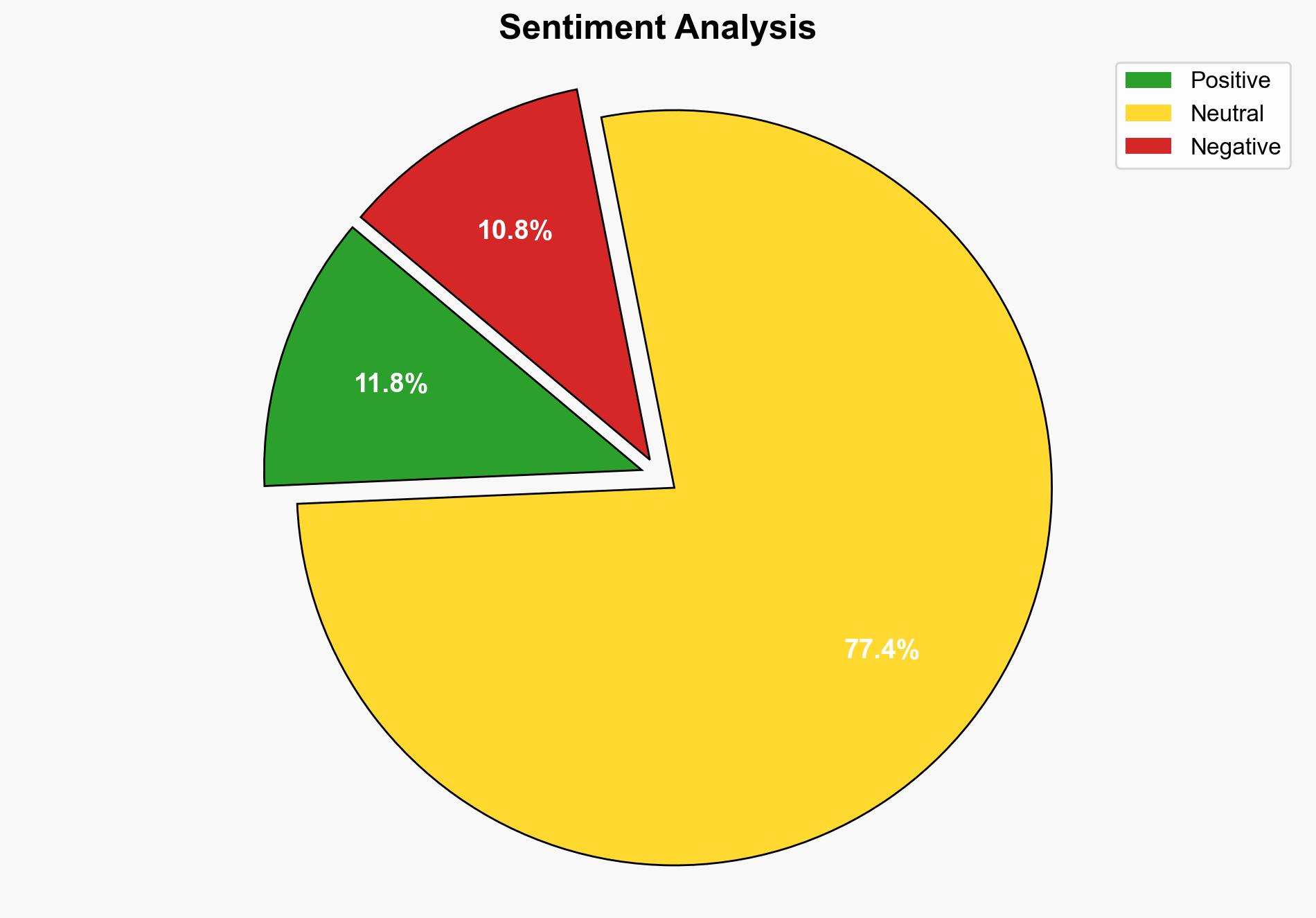
The report suggests a high likelihood that Chinese tech firms are supporting the Salt Typhoon espionage campaigns, potentially enhancing China’s global intelligence capabilities. The most supported hypothesis is that these firms are knowingly aiding state-sponsored cyber activities. The recommended action is to increase international collaboration on cybersecurity measures and to enhance defensive protocols against known vulnerabilities. Confidence Level: High.
2. Competing Hypotheses
1. **Hypothesis A**: Chinese tech firms are knowingly collaborating with state-sponsored groups like Salt Typhoon to enhance China’s cyber espionage capabilities.
2. **Hypothesis B**: Chinese tech firms are being exploited by Salt Typhoon without their knowledge, due to vulnerabilities in their systems or lack of stringent cybersecurity measures.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the alignment of the firms’ activities with state interests and the sophistication of the operations, which suggests a level of complicity or at least tacit approval.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the named tech firms have the capability and intent to support espionage activities. Another assumption is that the vulnerabilities are being exploited systematically rather than opportunistically.
– **Red Flags**: Lack of direct evidence linking the firms to state directives. The possibility of misattribution due to obfuscation tactics used by Salt Typhoon.
– **Blind Spots**: Limited insight into the internal policies of the Chinese tech firms and their potential motivations beyond state directives.
4. Implications and Strategic Risks
The involvement of commercial tech firms in espionage activities could lead to increased geopolitical tensions and economic sanctions. There is a risk of escalation in cyber conflicts, potentially affecting global telecommunications infrastructure. The psychological impact includes eroding trust in Chinese technology products and services.
5. Recommendations and Outlook
- Enhance international cybersecurity cooperation to address vulnerabilities and share intelligence on threat actors.
- Encourage organizations to adopt robust cybersecurity measures, including regular patching and multi-factor authentication.
- Scenario Projections:
- Best Case: Strengthened global cybersecurity frameworks reduce the impact of espionage activities.
- Worst Case: Escalation of cyber conflicts leads to widespread disruptions in global communications.
- Most Likely: Continued cyber espionage activities with periodic disruptions and increased geopolitical tensions.
6. Key Individuals and Entities
– Sichuan Juxinhe Network Technology
– Beijing Huanyu Tianqiong Technology
– Sichuan Zhixin Ruijie Network Technology
– Richard Horne (mentioned for context)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus