State-Sponsored Hackers Behind Majority of Vulnerability Exploits – Infosecurity Magazine
Published on: 2025-08-29
Intelligence Report: State-Sponsored Hackers Behind Majority of Vulnerability Exploits – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
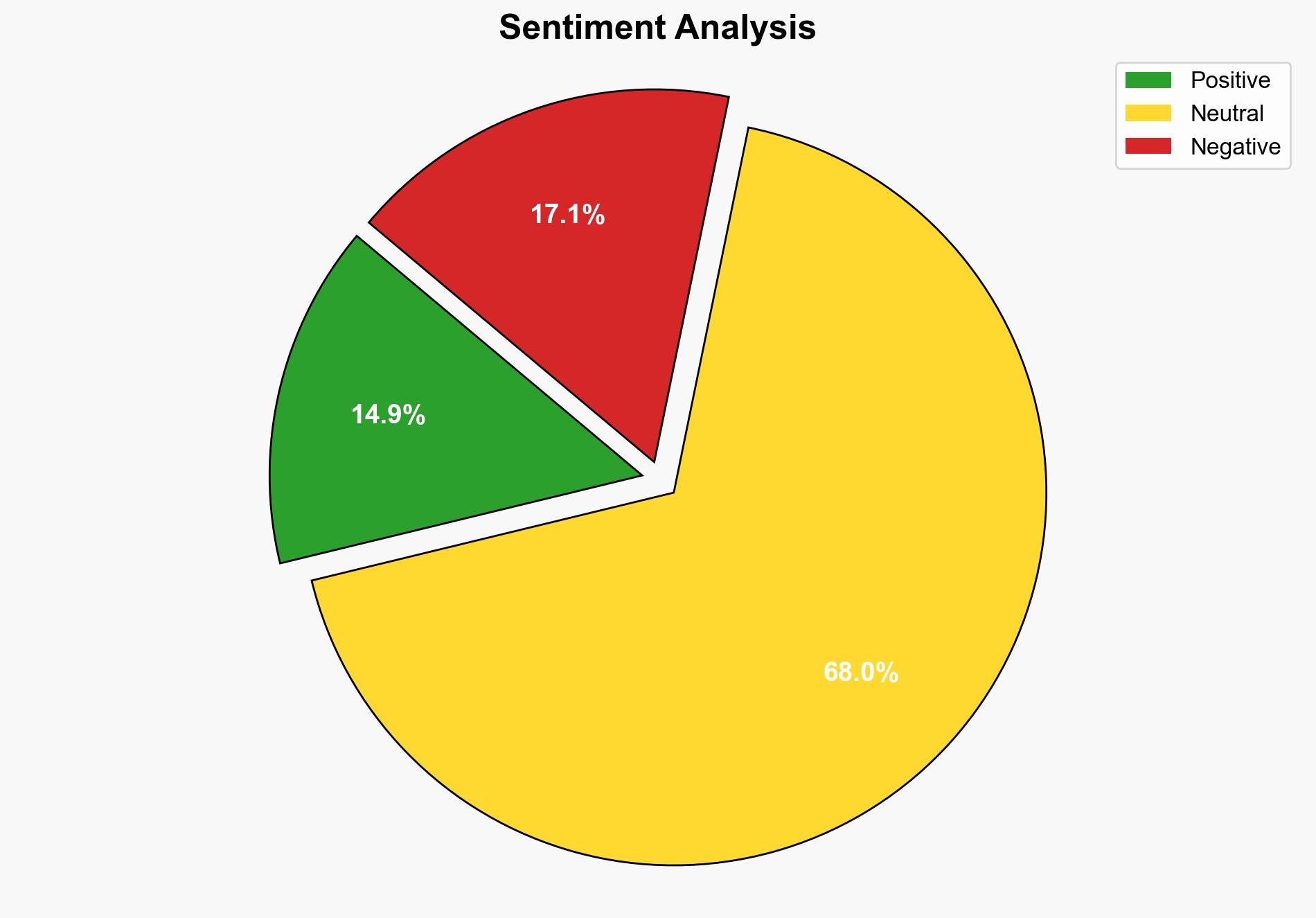
State-sponsored actors, particularly from China, are increasingly exploiting vulnerabilities for strategic geopolitical purposes, with a focus on edge infrastructure and enterprise solutions. The most supported hypothesis is that these activities are part of a coordinated effort to gain persistent access to high-value systems. Confidence level: High. Recommended action: Enhance cybersecurity measures focusing on edge security appliances and remote access tools, and increase international collaboration on cybersecurity intelligence sharing.
2. Competing Hypotheses
Hypothesis 1: State-sponsored actors, primarily from China, are systematically exploiting vulnerabilities to gain strategic advantages in espionage and surveillance.
Hypothesis 2: The high number of exploits attributed to state-sponsored actors is exaggerated, with financially motivated groups playing a more significant role than reported.
Using ACH 2.0, Hypothesis 1 is better supported due to consistent reporting of Chinese state-sponsored groups targeting specific high-value sectors and the rapid weaponization of disclosed vulnerabilities. Hypothesis 2 lacks substantial evidence and contradicts the observed focus on strategic geopolitical targets.
3. Key Assumptions and Red Flags
Assumptions: The attribution to state-sponsored actors is accurate and not influenced by misdirection or false flags. The reported preference for certain products by Chinese actors is based on reliable intelligence.
Red Flags: Potential bias in attributing attacks to state-sponsored actors without considering financial motives. Lack of detailed evidence on the involvement of other state actors besides China.
4. Implications and Strategic Risks
The persistent targeting of edge infrastructure and enterprise solutions by state-sponsored actors could lead to significant geopolitical tensions, particularly between China and Western nations. The risk of escalation is high if these activities are perceived as acts of cyber warfare. Economically, successful exploits could disrupt critical infrastructure, impacting global markets and supply chains.
5. Recommendations and Outlook
- Enhance cybersecurity protocols for edge infrastructure and remote access tools, prioritizing patch management and vulnerability assessments.
- Foster international cooperation to improve intelligence sharing and develop unified responses to state-sponsored cyber threats.
- Scenario Projections:
- Best Case: Increased global cooperation leads to effective deterrence and reduction in state-sponsored cyber activities.
- Worst Case: Escalation of cyber activities results in significant geopolitical conflicts and economic disruptions.
- Most Likely: Continued state-sponsored cyber activities with periodic disruptions and heightened international tensions.
6. Key Individuals and Entities
No specific individuals are named in the source text. The focus is on Chinese state-sponsored groups and their associated tactics.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus