WhatsApp Issues Emergency Update for Zero-Click Exploit Targeting iOS and macOS Devices – Internet
Published on: 2025-08-30
Intelligence Report: WhatsApp Issues Emergency Update for Zero-Click Exploit Targeting iOS and macOS Devices – Internet
1. BLUF (Bottom Line Up Front)
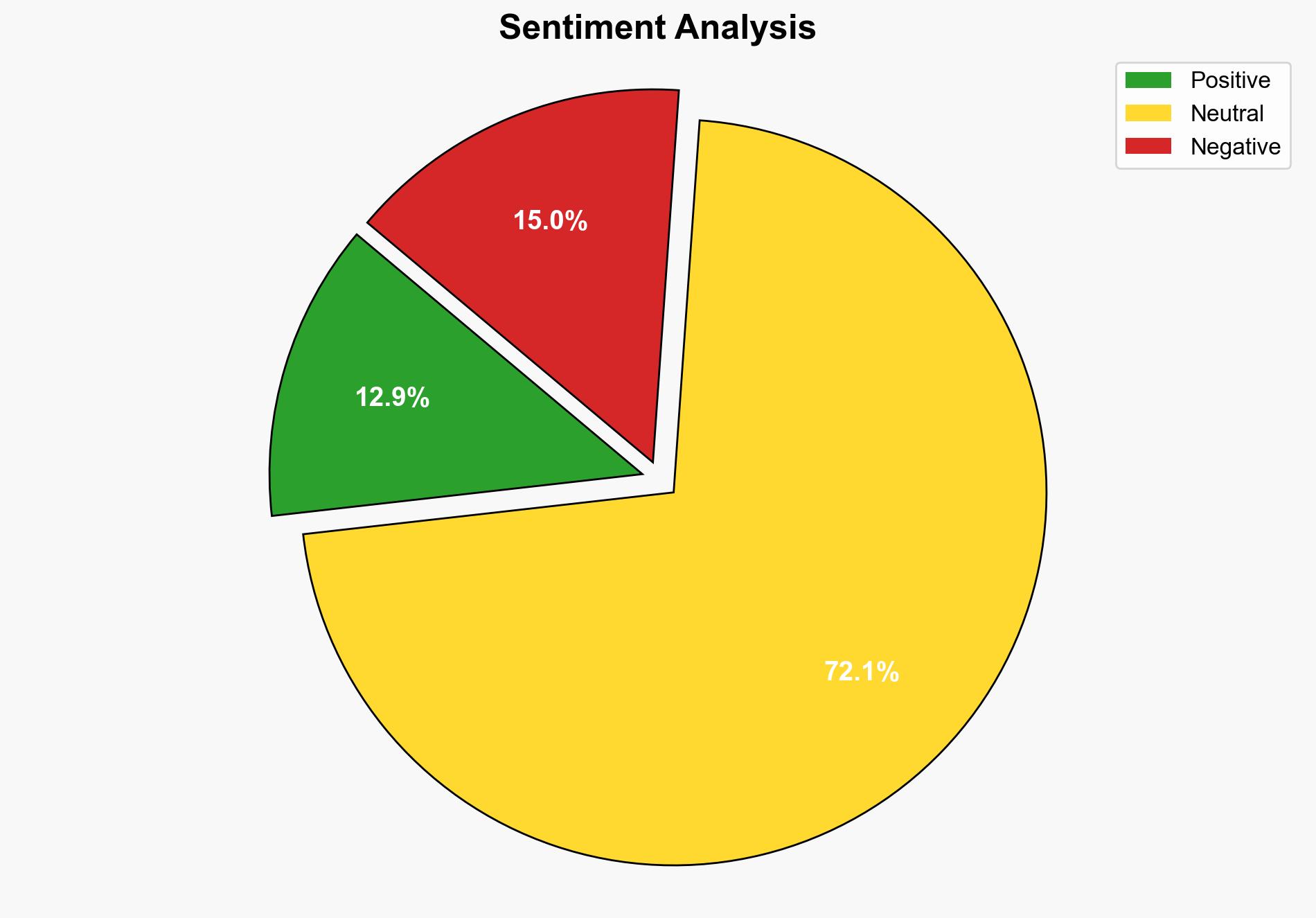
The recent zero-click exploit targeting WhatsApp on iOS and macOS devices represents a significant cybersecurity threat, particularly to high-risk individuals such as journalists and human rights defenders. The most supported hypothesis suggests this is part of a sophisticated, targeted campaign by a state-sponsored actor. Confidence level: Moderate. Immediate action is recommended to update devices and applications, alongside increased monitoring for potential exploitation attempts.
2. Competing Hypotheses
1. **State-Sponsored Campaign Hypothesis**: The zero-click exploit is part of a coordinated effort by a state-sponsored actor targeting specific individuals for espionage purposes. This is supported by the sophistication of the attack and the targeting of civil society individuals.
2. **Cybercriminal Exploitation Hypothesis**: The exploit is being used by cybercriminals for financial gain, leveraging the vulnerability to access sensitive data from high-value targets. This hypothesis considers the potential for monetization of stolen data.
Using ACH 2.0, the state-sponsored campaign hypothesis is better supported due to the complexity of the exploit and the profile of the targets, which aligns with typical state-level interests rather than purely financial motives.
3. Key Assumptions and Red Flags
– **Assumptions**: The analysis assumes that the exploit’s sophistication inherently points to state-level actors. It also assumes that the targets are primarily high-risk individuals.
– **Red Flags**: Lack of specific attribution to a known spyware vendor or nation-state actor. The unspecified number of targeted individuals creates uncertainty about the scale of the campaign.
– **Blind Spots**: Potential underestimation of cybercriminal capabilities and motivations.
4. Implications and Strategic Risks
The exploit poses a significant risk to personal privacy and national security, particularly if sensitive information is compromised. It could lead to increased geopolitical tensions if a state actor is confirmed. The attack may prompt stricter cybersecurity regulations and increased scrutiny of tech companies’ security measures.
5. Recommendations and Outlook
- Immediate update of all affected devices and applications to the latest versions.
- Enhanced monitoring and threat intelligence sharing among cybersecurity entities.
- Scenario Projections:
- Best Case: Rapid patch adoption and no further exploitation.
- Worst Case: Widespread exploitation leading to significant data breaches and geopolitical fallout.
- Most Likely: Continued targeted attacks with gradual mitigation as patches are applied.
6. Key Individuals and Entities
Donncha Cearbhaill, Amnesty International Security Lab.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus