Azure AD Credentials Exposed in Public App Settings File – Infosecurity Magazine
Published on: 2025-09-02
Intelligence Report: Azure AD Credentials Exposed in Public App Settings File – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
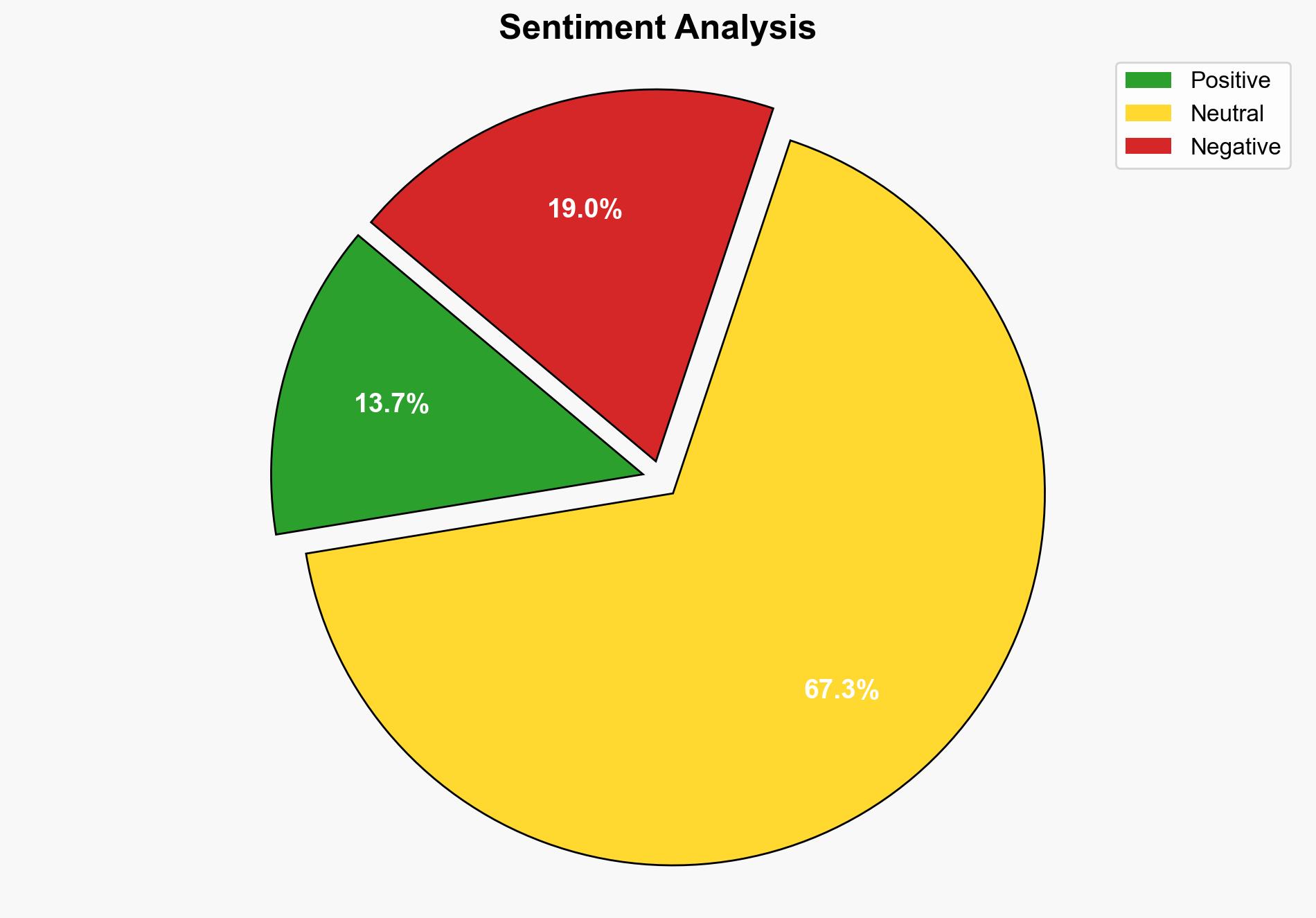
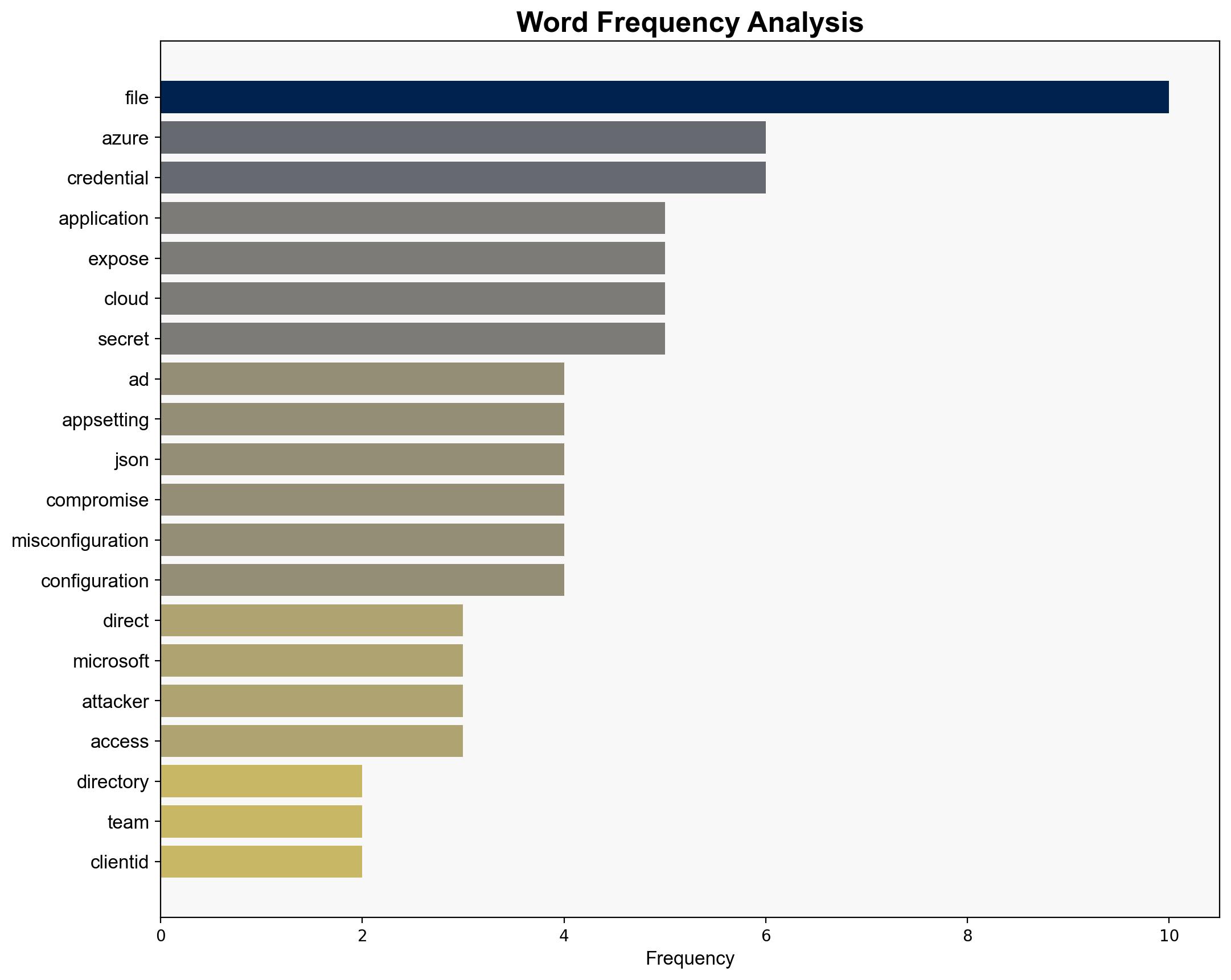
The exposure of Azure AD credentials in a publicly accessible app settings file presents a significant cybersecurity risk. The most supported hypothesis is that this vulnerability results from common cloud misconfiguration practices. Confidence level: High. Recommended action includes immediate credential rotation, implementation of secret management tools, and enhanced security protocols.
2. Competing Hypotheses
1. **Hypothesis 1**: The exposure is due to common cloud misconfiguration, where developers inadvertently leave sensitive credentials in publicly accessible files due to poor deployment practices and lack of security testing.
2. **Hypothesis 2**: The exposure is a deliberate act by an insider or a sophisticated adversary intending to exploit the vulnerability for unauthorized access to Microsoft resources.
Using ACH 2.0, Hypothesis 1 is better supported by the evidence, as the report highlights typical misconfiguration issues and the absence of secret management tools. Hypothesis 2 lacks direct evidence of malicious intent or insider involvement.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the exposure is accidental and not a result of deliberate sabotage. The reliance on typical misconfiguration patterns suggests a bias towards common explanations.
– **Red Flags**: Lack of evidence for insider threat or external adversary involvement. The assumption that all exposures are accidental could overlook potential targeted attacks.
– **Blind Spots**: The report does not consider the possibility of a coordinated attack exploiting multiple similar vulnerabilities across different organizations.
4. Implications and Strategic Risks
The exposure of Azure AD credentials can lead to unauthorized access to sensitive data, privilege escalation, and persistent threats within an organization’s cloud environment. This could result in data breaches, financial loss, and reputational damage. If exploited by a state-sponsored actor, it could also have geopolitical implications, especially if sensitive governmental or critical infrastructure data is accessed.
5. Recommendations and Outlook
- **Immediate Actions**: Rotate all exposed credentials and implement Azure Key Vault or similar secret management solutions. Conduct a comprehensive security audit to identify and rectify other potential misconfigurations.
- **Long-term Strategy**: Develop and enforce strict security policies for cloud deployments, including regular security testing and code reviews.
- **Scenario Projections**:
– **Best Case**: Rapid remediation prevents any unauthorized access, and improved security measures prevent future incidents.
– **Worst Case**: Exploitation of the vulnerability leads to significant data breaches and financial losses.
– **Most Likely**: Some unauthorized access occurs, but swift action mitigates major damage.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus is on the entities involved, such as Microsoft Azure and the organizations using its services.
7. Thematic Tags
national security threats, cybersecurity, cloud security, data breach, risk management