Hundreds of LLM servers left exposed online – here’s what we know – TechRadar
Published on: 2025-09-02
Intelligence Report: Hundreds of LLM servers left exposed online – here’s what we know – TechRadar
1. BLUF (Bottom Line Up Front)
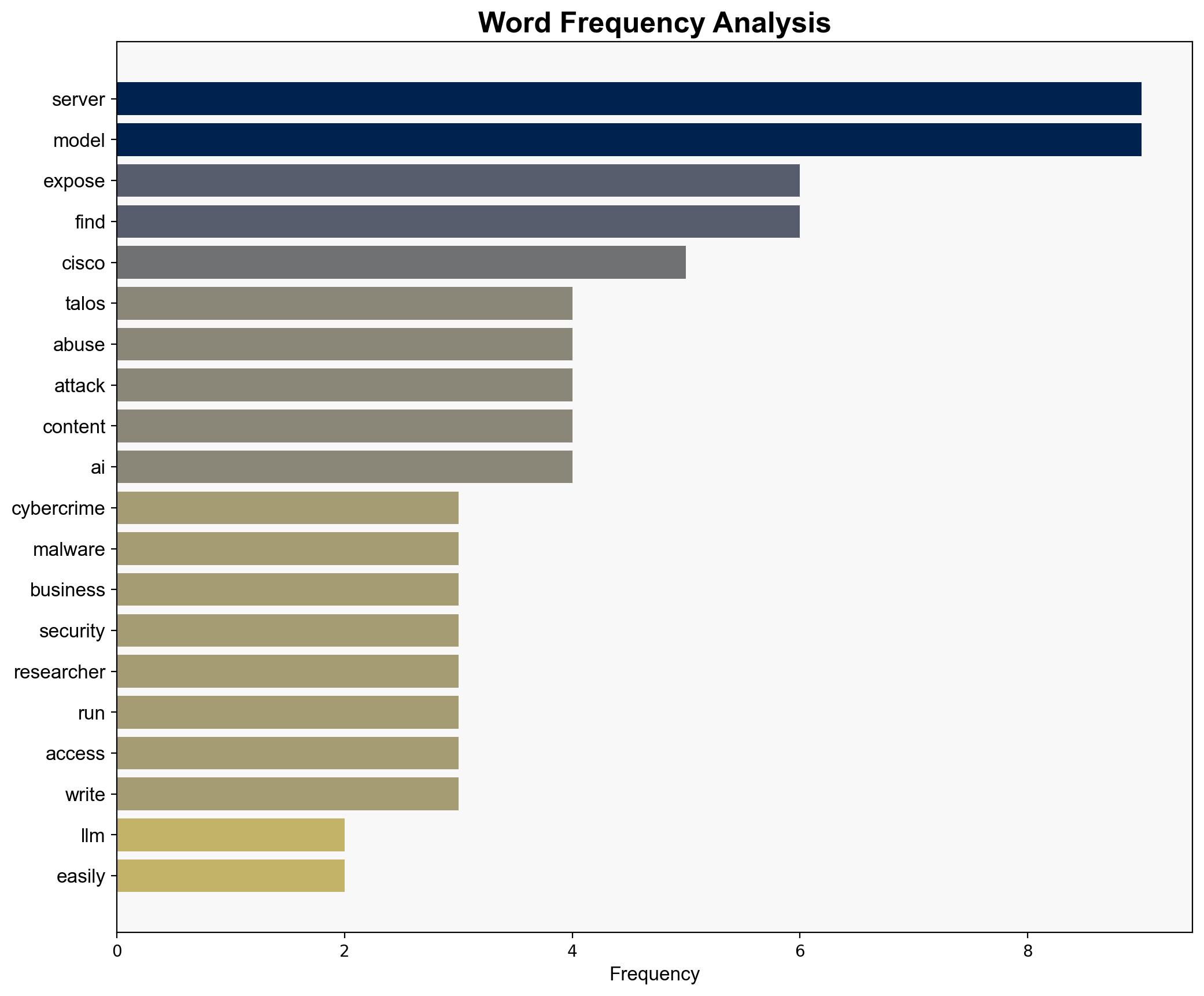
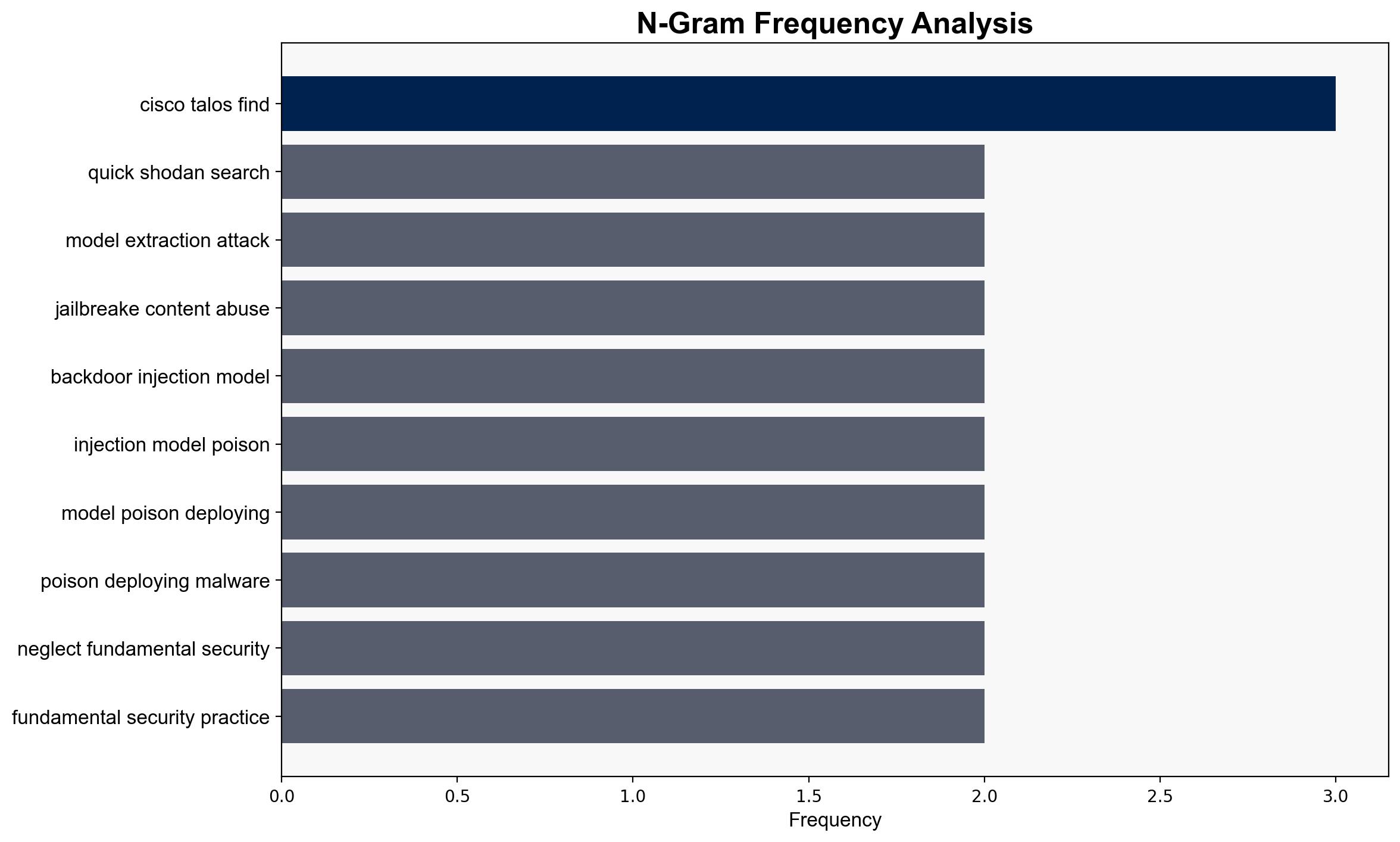
The exposure of hundreds of LLM servers presents a significant cybersecurity risk, potentially facilitating model extraction, content abuse, and malware deployment. The most supported hypothesis is that this exposure results from widespread neglect of security practices. Confidence level: High. Recommended action: Immediate implementation of robust security measures and awareness campaigns to mitigate risks.
2. Competing Hypotheses
Hypothesis 1: The exposure of LLM servers is primarily due to negligence in implementing basic security protocols by organizations and developers.
Hypothesis 2: The exposure is a deliberate act by malicious actors to create vulnerabilities for future exploitation.
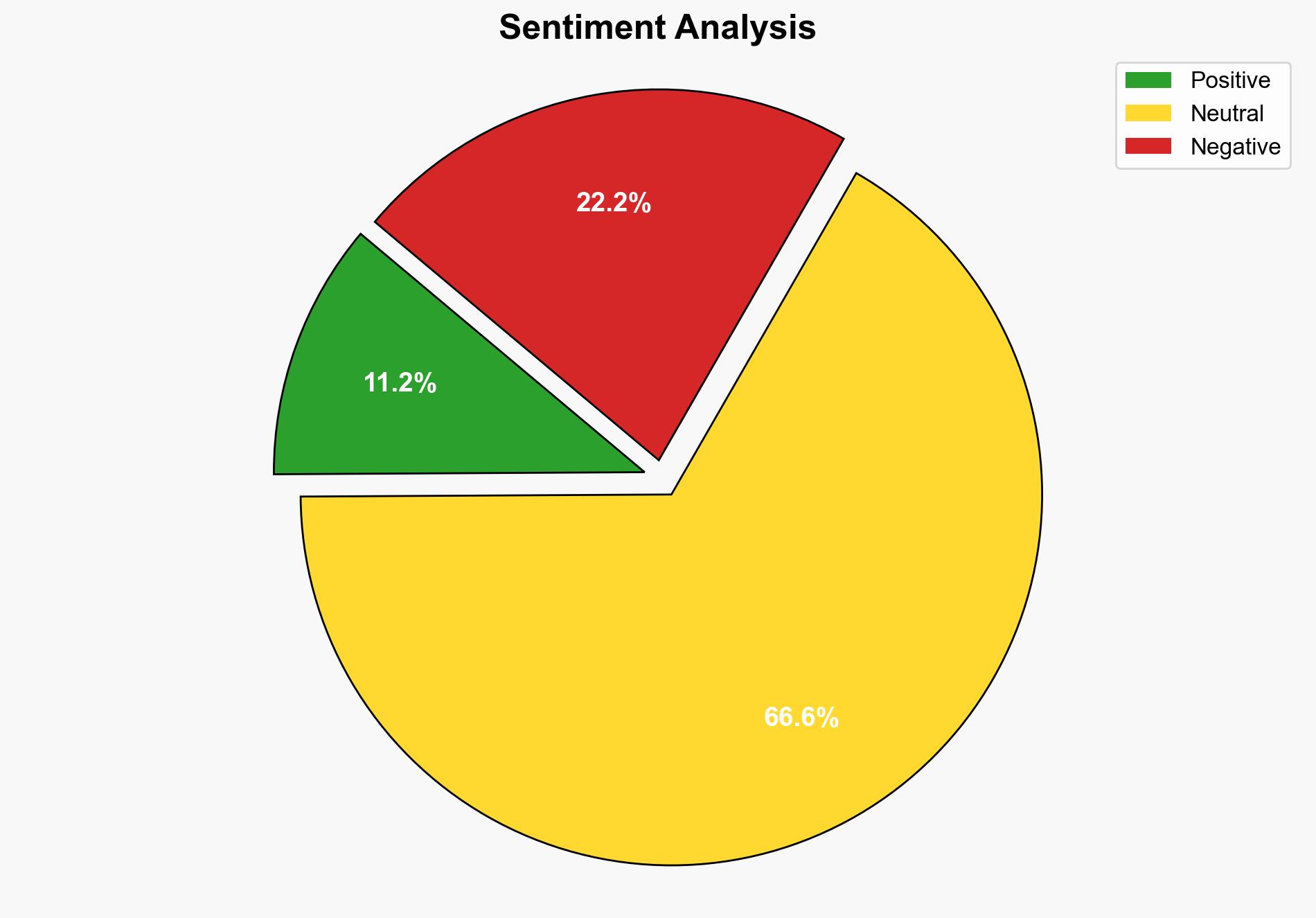
Using Analysis of Competing Hypotheses (ACH), Hypothesis 1 is better supported by the evidence, particularly the widespread nature of the exposure and the lack of immediate exploitation, suggesting oversight rather than intent.
3. Key Assumptions and Red Flags
Assumptions:
– Organizations prioritize functionality over security in AI deployments.
– There is a lack of awareness or understanding of security implications among developers.
Red Flags:
– The possibility of coordinated attacks if multiple servers are exploited simultaneously.
– The absence of immediate exploitation may indicate preparation for a larger, coordinated cyberattack.
4. Implications and Strategic Risks
The exposure could lead to significant economic losses and reputational damage if exploited. Cyber risks include data breaches, intellectual property theft, and the spread of misinformation. Geopolitically, this could escalate tensions if state actors are involved or blamed. The psychological impact includes eroding trust in AI systems.
5. Recommendations and Outlook
- Immediate audit and remediation of exposed servers to ensure compliance with security protocols.
- Develop and disseminate best practice guidelines for AI deployment security.
- Scenario-based projections:
- Best Case: Rapid response mitigates risks, and security awareness improves, preventing future exposures.
- Worst Case: Exploitation leads to widespread cyberattacks, causing economic and reputational damage.
- Most Likely: Incremental improvements in security practices reduce but do not eliminate risks.
6. Key Individuals and Entities
– Cisco Talos researchers (unnamed) identified the exposed servers.
– Ollama servers are specifically mentioned as being exposed.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus