US CISA adds WhatsApp and TP-link flaws to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
Published on: 2025-09-03
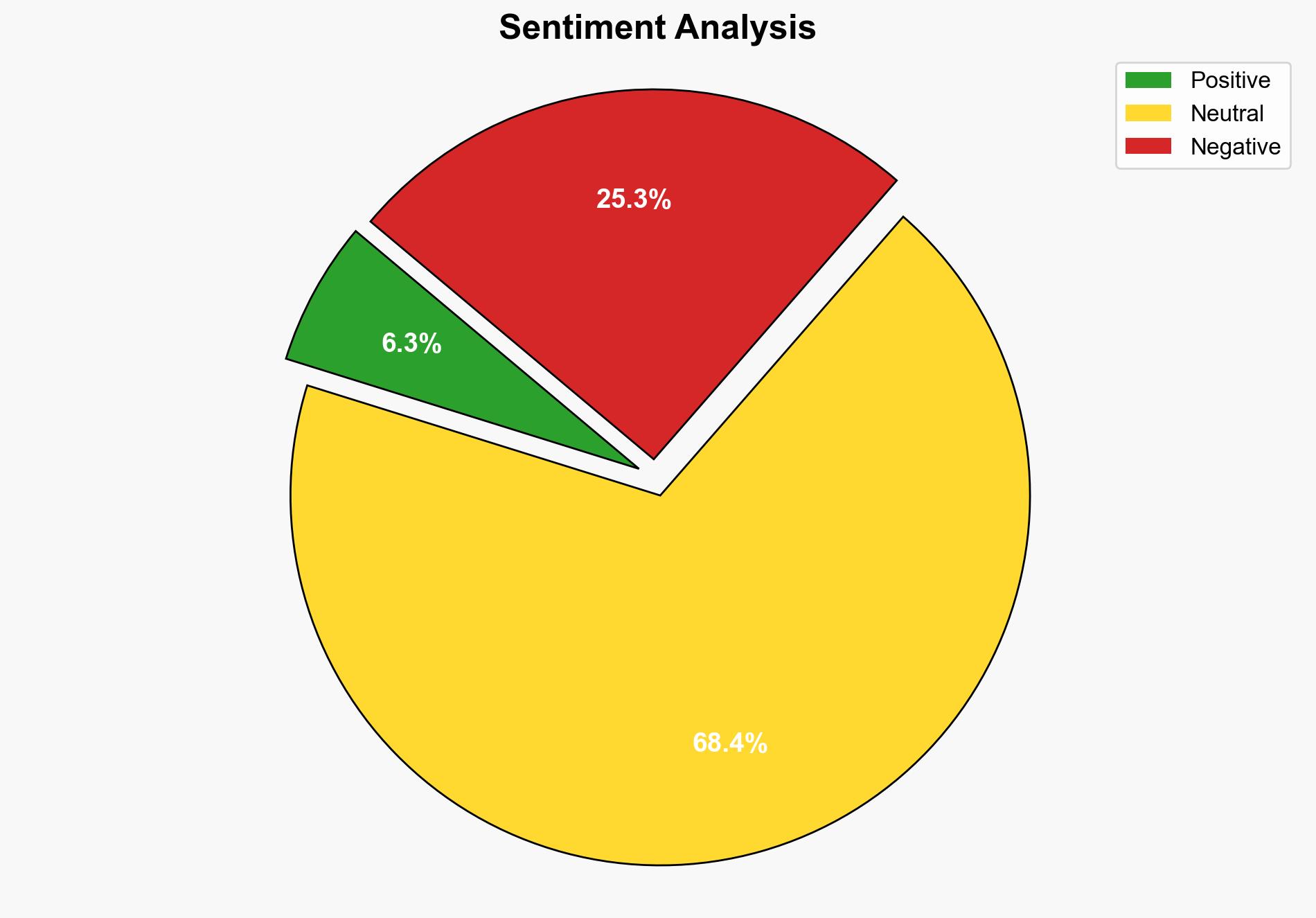
Intelligence Report: US CISA adds WhatsApp and TP-link flaws to its Known Exploited Vulnerabilities catalog – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
The addition of WhatsApp and TP-Link vulnerabilities to CISA’s Known Exploited Vulnerabilities catalog highlights significant cybersecurity threats that could be exploited by state-sponsored actors and cybercriminals. The most supported hypothesis is that these vulnerabilities are being actively targeted by sophisticated threat actors to gain unauthorized access to sensitive information. Confidence Level: High. Recommended action includes immediate patching of affected systems and heightened monitoring for unusual activities.
2. Competing Hypotheses
Hypothesis 1: State-sponsored groups are exploiting these vulnerabilities as part of a coordinated cyber-espionage campaign targeting high-value individuals and organizations.
Hypothesis 2: Cybercriminal groups are opportunistically exploiting these vulnerabilities for financial gain, targeting a broad range of users indiscriminately.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the sophistication required for zero-click exploits and the involvement of advanced spyware, which is typically associated with state actors.
3. Key Assumptions and Red Flags
Assumptions:
– State actors have the capability and intent to exploit these vulnerabilities.
– The vulnerabilities are critical enough to warrant immediate attention from CISA.
Red Flags:
– Lack of specific attribution to particular threat actors.
– Limited disclosure of technical details about the vulnerabilities and their exploitation.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to significant data breaches, impacting national security and economic stability. There is a risk of cascading effects if exploited vulnerabilities are used to gain deeper access into critical infrastructure networks. Geopolitically, this could escalate tensions if state-sponsored involvement is confirmed.
5. Recommendations and Outlook
- Immediate patching of affected systems and devices to mitigate risks.
- Enhanced monitoring and threat intelligence sharing among organizations to detect and respond to exploitation attempts.
- Best Case Scenario: Rapid patch deployment prevents significant exploitation, and threat actors are deterred by increased security measures.
- Worst Case Scenario: Widespread exploitation leads to major data breaches and geopolitical tensions.
- Most Likely Scenario: Continued attempts at exploitation with varying degrees of success, prompting ongoing vigilance and response efforts.
6. Key Individuals and Entities
– Donncha Cearbhaill
– Amnesty researchers
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus