Hirsch Velocity 39 turns security into business value – Help Net Security
Published on: 2025-09-05
Intelligence Report: Hirsch Velocity 39 turns security into business value – Help Net Security
1. BLUF (Bottom Line Up Front)
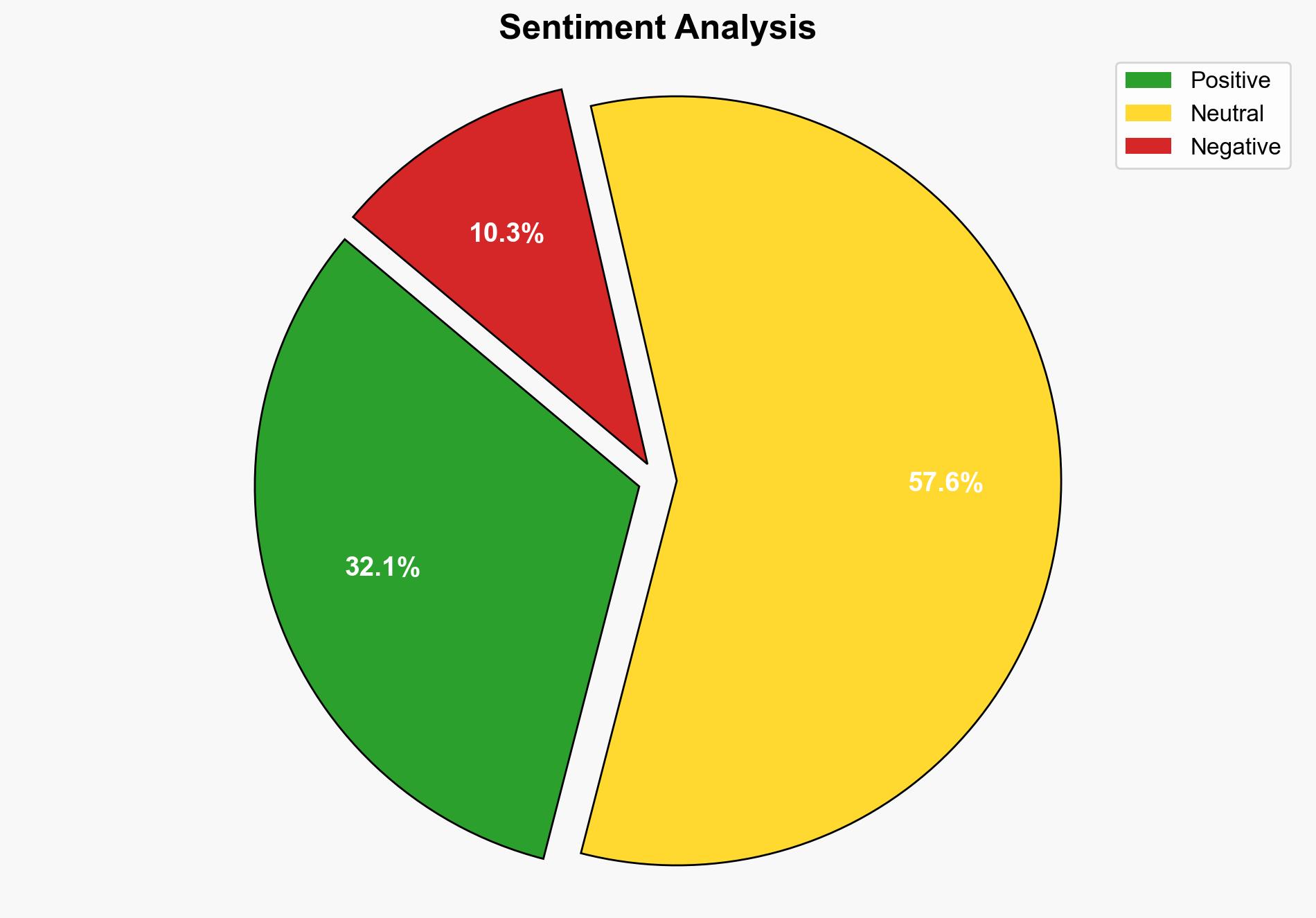
The most supported hypothesis is that Hirsch Velocity 39 is strategically positioned to transform security management into a business value proposition by enhancing operational efficiency and compliance. This analysis is supported by structured analytic techniques, including Cross-Impact Simulation. Confidence level: Moderate. Recommended action: Monitor adoption rates and feedback from key industry players to validate the platform’s effectiveness and market penetration.
2. Competing Hypotheses
Hypothesis 1: Hirsch Velocity 39 effectively integrates security management with business operations, leading to increased operational efficiency and compliance, thus turning security into a business value driver.
Hypothesis 2: Hirsch Velocity 39’s claims of transforming security into business value are overstated, with potential challenges in integration and user adoption limiting its effectiveness.
3. Key Assumptions and Red Flags
Assumptions:
– The platform’s integration capabilities are seamless and compatible with existing systems.
– Organizations prioritize security as a business enabler rather than a cost center.
Red Flags:
– Lack of independent validation of the platform’s effectiveness.
– Potential over-reliance on marketing language without substantive evidence.
4. Implications and Strategic Risks
The successful adoption of Hirsch Velocity 39 could set a precedent for security platforms as business enablers, influencing market trends and competitive dynamics. However, failure to deliver on its promises could result in reputational damage and financial losses. Cybersecurity threats remain a persistent risk, necessitating continuous innovation and adaptation.
5. Recommendations and Outlook
- Monitor industry adoption and gather feedback from early adopters to assess the platform’s impact.
- Engage with cybersecurity experts to independently evaluate the platform’s security claims.
- Scenario Projections:
- Best Case: Widespread adoption leading to enhanced security and operational efficiency across industries.
- Worst Case: Integration challenges and security breaches undermine confidence in the platform.
- Most Likely: Gradual adoption with mixed results, prompting iterative improvements.
6. Key Individuals and Entities
– Scott Elliott
– Mark Allen
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus