ICEBlock handled my vulnerability report in the worst possible way – Micahflee.com
Published on: 2025-09-08
Intelligence Report: ICEBlock handled my vulnerability report in the worst possible way – Micahflee.com
1. BLUF (Bottom Line Up Front)
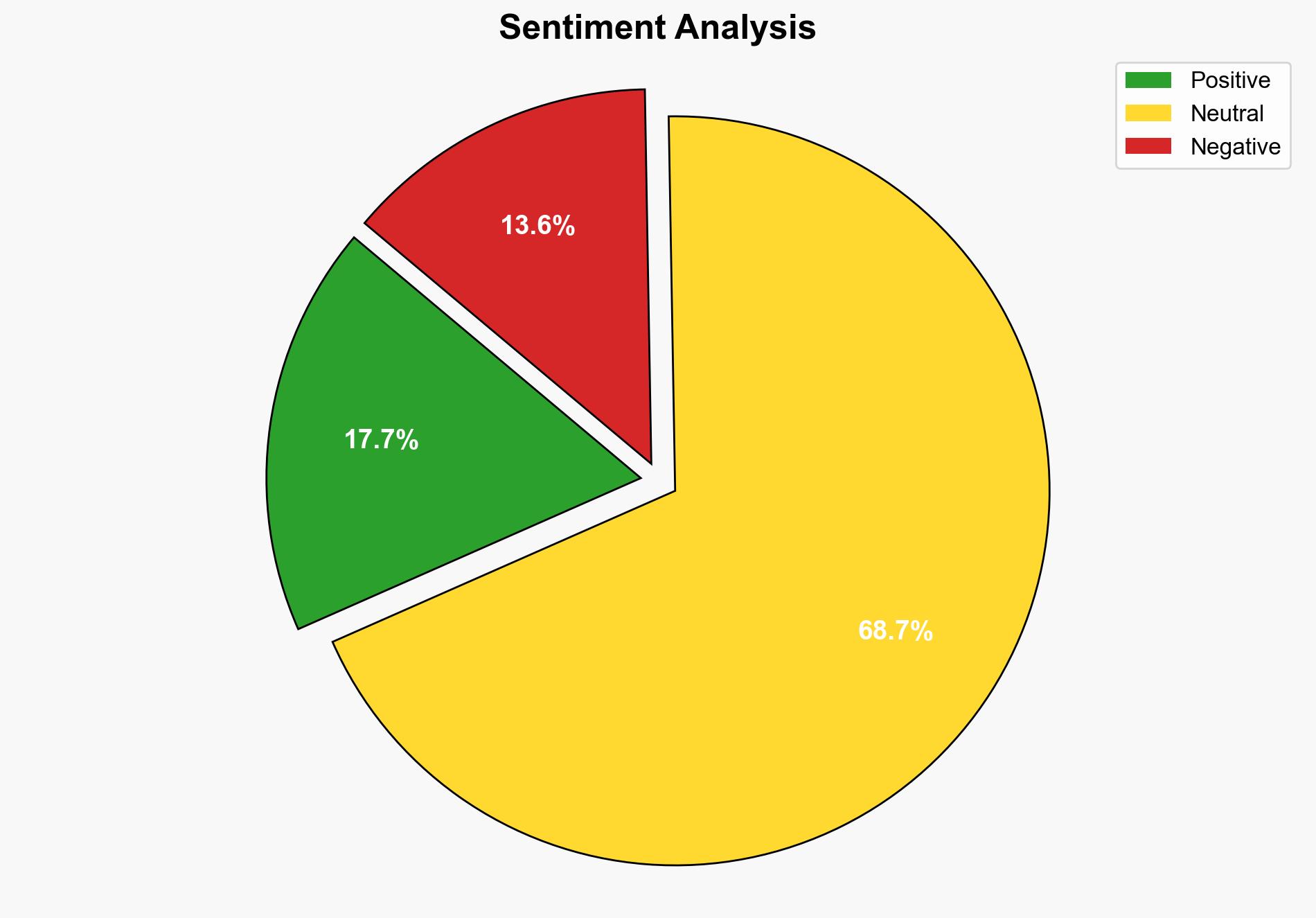
The most supported hypothesis suggests that ICEBlock’s response to the vulnerability report was inadequate due to negligence or lack of expertise in cybersecurity. This poses a moderate risk to user data security. It is recommended that ICEBlock immediately address the identified vulnerabilities and improve their cybersecurity protocols. Confidence level: Moderate.
2. Competing Hypotheses
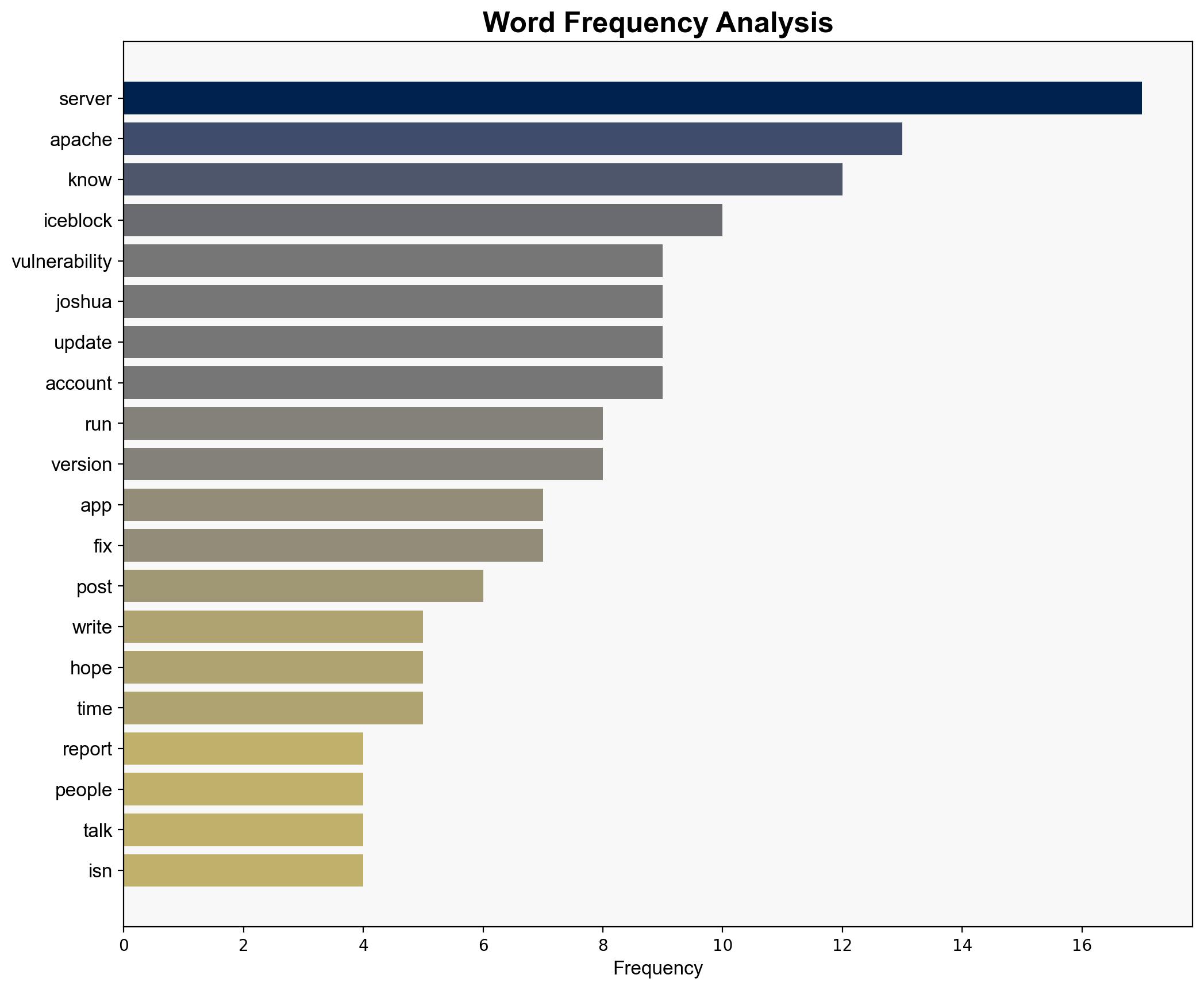
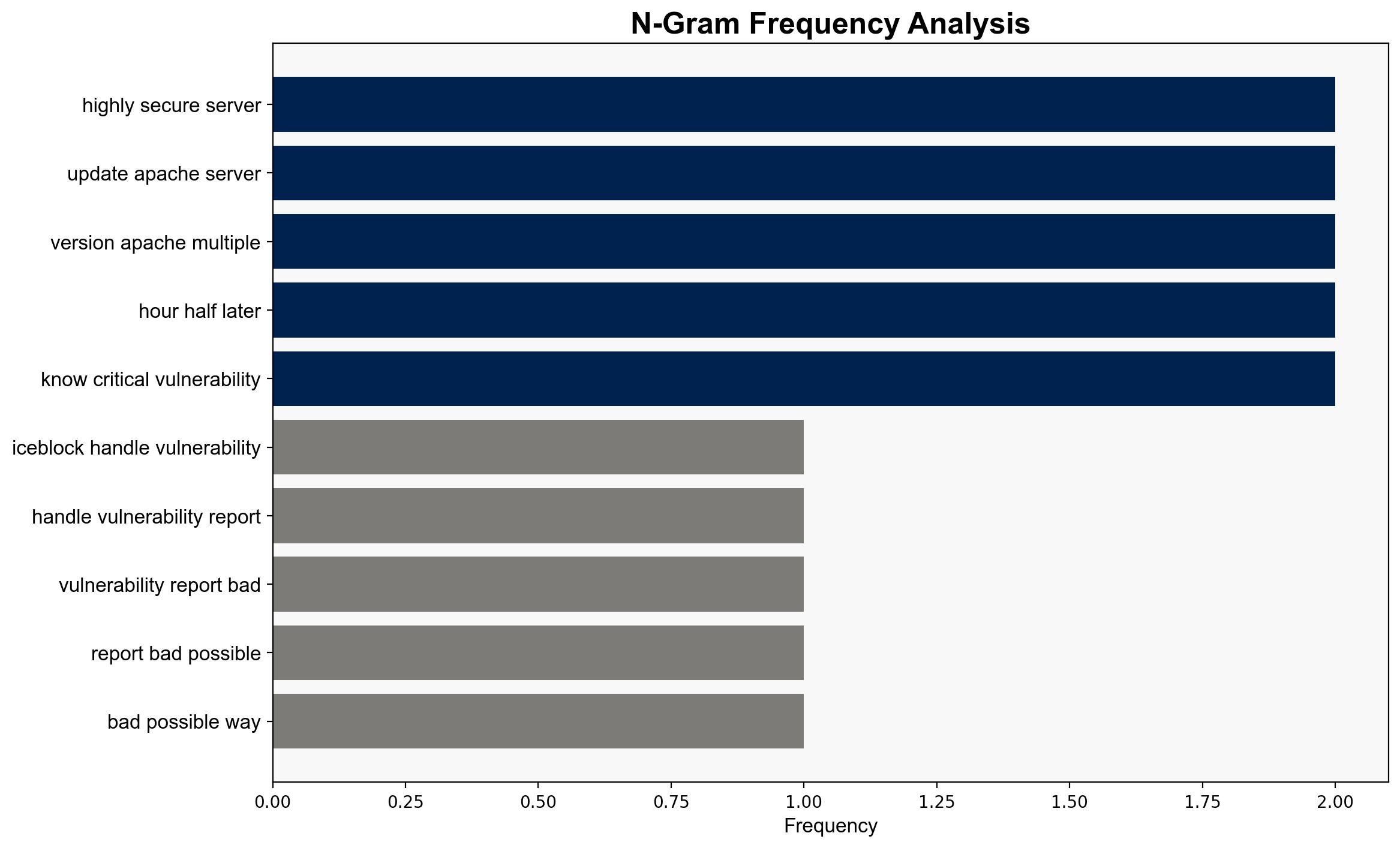
1. **Negligence or Lack of Expertise**: ICEBlock’s failure to address the reported vulnerabilities in a timely manner is due to negligence or a lack of cybersecurity expertise. This is supported by the delayed response to the report and the continued presence of vulnerabilities.
2. **Intentional Disregard**: ICEBlock intentionally disregarded the vulnerability report, possibly due to prioritizing other business objectives over cybersecurity. This hypothesis is less supported due to the eventual update of the server, albeit delayed.
3. Key Assumptions and Red Flags
– **Assumptions**: Both hypotheses assume that the vulnerabilities were known and could be easily fixed. It is also assumed that ICEBlock has the resources to address these issues.
– **Red Flags**: The lack of communication from ICEBlock and the blocking of the reporter’s account suggest potential avoidance behavior. The delay in updating the server raises questions about internal processes and priorities.
– **Blind Spots**: The internal decision-making process of ICEBlock is not transparent, making it difficult to ascertain the true cause of the delay.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: Continued vulnerabilities could lead to data breaches, compromising user data and potentially leading to legal and reputational damage.
– **Economic Risks**: A breach could result in financial losses due to legal liabilities and loss of user trust.
– **Geopolitical Risks**: If the app is used for sensitive reporting, compromised data could have broader implications for users’ safety and privacy.
5. Recommendations and Outlook
- ICEBlock should conduct a comprehensive cybersecurity audit and implement regular updates and monitoring to prevent future vulnerabilities.
- Improve communication protocols with security researchers to ensure timely and effective responses to vulnerability reports.
- Scenario Projections:
- Best Case: ICEBlock addresses the vulnerabilities promptly, restoring user trust and securing data.
- Worst Case: A data breach occurs, leading to significant financial and reputational damage.
- Most Likely: ICEBlock takes corrective actions but may face temporary reputational challenges.
6. Key Individuals and Entities
– Joshua Aaron
– Micah Lee (reporter)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus