SAP users patch now – worrying S4HANA vulnerability being exploited in the wild – TechRadar
Published on: 2025-09-08
Intelligence Report: SAP users patch now – worrying S4HANA vulnerability being exploited in the wild – TechRadar
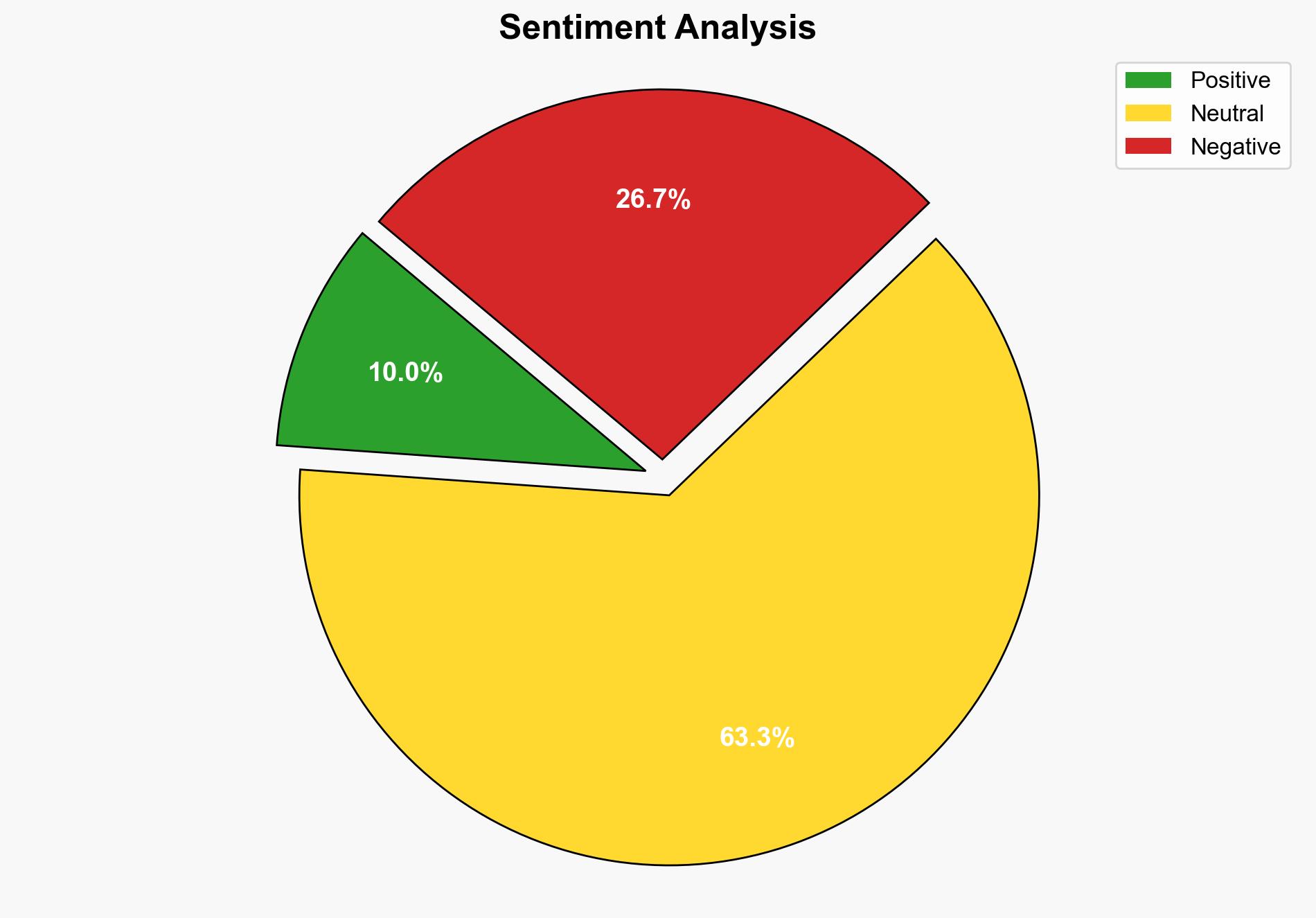
1. BLUF (Bottom Line Up Front)
The critical vulnerability in SAP’s S4HANA system poses a significant risk of system takeover and data compromise. The most supported hypothesis is that threat actors are actively exploiting this vulnerability due to the ease of reverse engineering the patch. Immediate patch deployment is recommended to mitigate risks. Confidence level: High.
2. Competing Hypotheses
Hypothesis 1: Threat actors are actively exploiting the SAP S4HANA vulnerability due to its critical nature and the ease of reverse engineering the patch. This is supported by the reported limited abuse in the wild and the vulnerability’s high severity score.
Hypothesis 2: The vulnerability, while critical, is not yet widely exploited due to limited awareness or technical barriers among potential attackers. The reports of limited abuse suggest that exploitation is not yet widespread.
3. Key Assumptions and Red Flags
– Assumption for Hypothesis 1: Threat actors have the capability and intent to exploit the vulnerability.
– Assumption for Hypothesis 2: Technical barriers or lack of awareness are significant enough to prevent widespread exploitation.
– Red Flags: The report does not specify the identity or intent of the threat actors, leading to uncertainty about the scale of the threat.
– Missing Data: Lack of detailed incident reports or confirmation of specific attacks exploiting this vulnerability.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant economic damage through data breaches, system downtime, and potential ransom demands. Cybersecurity threats could escalate if attackers leverage compromised systems for further attacks. Geopolitically, this could strain relations if state actors are involved or if critical infrastructure is targeted.
5. Recommendations and Outlook
- Immediate deployment of the SAP patch across all vulnerable systems.
- Conduct a thorough security audit to identify any signs of compromise.
- Enhance monitoring for unusual activity indicating exploitation attempts.
- Best Case Scenario: Rapid patch deployment prevents widespread exploitation.
- Worst Case Scenario: Delayed patching leads to significant data breaches and operational disruptions.
- Most Likely Scenario: Limited exploitation continues until patching is widespread.
6. Key Individuals and Entities
– SAP (as the entity responsible for the software and patch release)
– SecurityBridge (as the entity that discovered and reported the vulnerability)
7. Thematic Tags
national security threats, cybersecurity, enterprise risk management, data protection