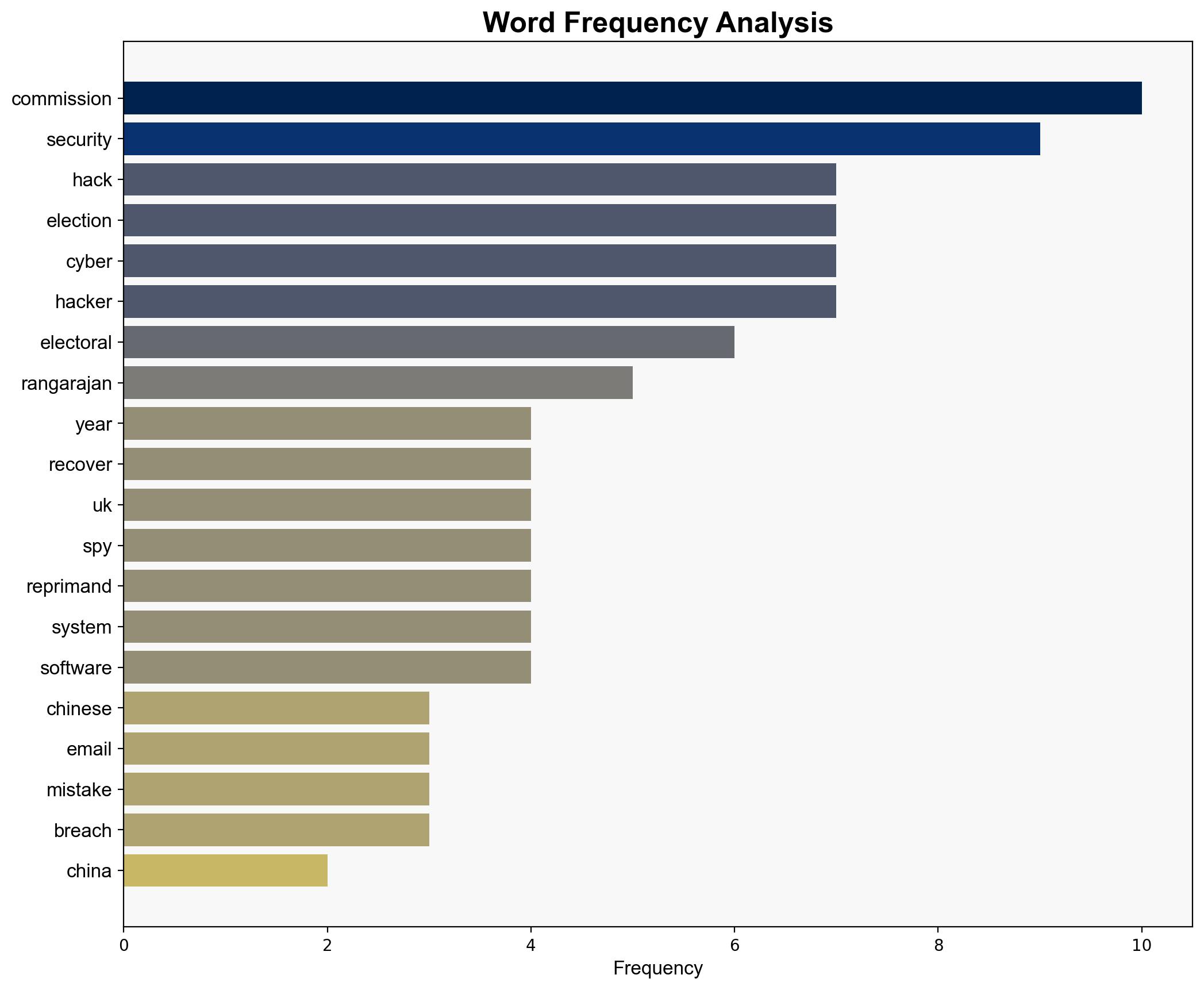
It’s taken three years to recover from China hack election watchdog says – BBC News
Published on: 2025-09-08
Intelligence Report: It’s taken three years to recover from China hack election watchdog says – BBC News
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the hack of the UK Electoral Commission was a sophisticated cyber espionage operation likely linked to Chinese state actors, exploiting systemic vulnerabilities over an extended period. Confidence level is moderate due to the lack of direct evidence linking the breach to Chinese entities. Recommended action includes enhancing cybersecurity protocols and conducting comprehensive audits to prevent future breaches.
2. Competing Hypotheses
1. **Hypothesis A**: The hack was a state-sponsored cyber espionage operation by Chinese actors aimed at gathering intelligence on the UK’s electoral system.
– **Supporting Evidence**: The breach exploited a known vulnerability in Microsoft Exchange, a tactic consistent with state-sponsored operations. The prolonged undetected access suggests a sophisticated actor.
2. **Hypothesis B**: The hack was conducted by independent cybercriminals or a non-state group seeking financial gain or to cause disruption.
– **Supporting Evidence**: The lack of direct attribution to China and the potential for financial or disruptive motives align with non-state actor behavior.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Hypothesis A assumes state-level resources and motivations align with the breach.
– Hypothesis B assumes the absence of state-level indicators implies non-state involvement.
– **Red Flags**:
– Lack of direct evidence linking the breach to Chinese state actors.
– Potential bias in attributing cyber incidents to state actors without conclusive evidence.
4. Implications and Strategic Risks
The breach highlights vulnerabilities in critical national infrastructure, posing risks to electoral integrity and public trust. If state-sponsored, it indicates a strategic interest in influencing or understanding democratic processes. This could escalate geopolitical tensions and lead to retaliatory measures. If non-state actors, it underscores the need for robust cybersecurity defenses against diverse threats.
5. Recommendations and Outlook
- Enhance cybersecurity measures, including regular audits and updates to systems like Microsoft Exchange.
- Develop a rapid response protocol for future breaches to minimize damage and recovery time.
- Scenario Projections:
- Best Case: Strengthened defenses deter future attacks, maintaining electoral integrity.
- Worst Case: Continued vulnerabilities lead to further breaches, undermining public confidence.
- Most Likely: Incremental improvements in cybersecurity reduce but do not eliminate risks.
6. Key Individuals and Entities
– Vijay Rangarajan: Chief Executive of the Electoral Commission, acknowledged the breach and its impact.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus