Two Zero-Days Among Patch Tuesday CVEs This Month – Infosecurity Magazine
Published on: 2025-09-10
Intelligence Report: Two Zero-Days Among Patch Tuesday CVEs This Month – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
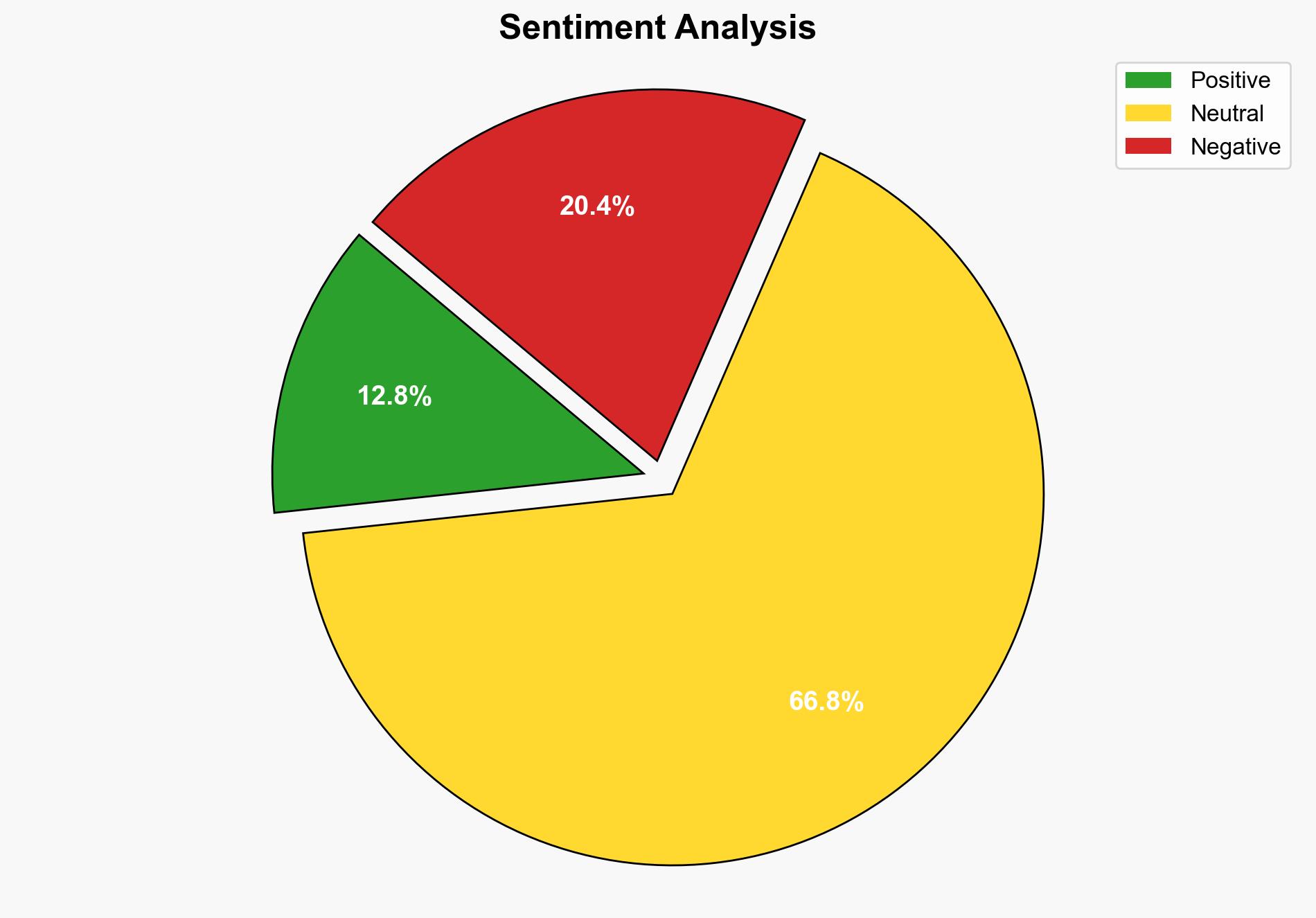
The most supported hypothesis is that the zero-day vulnerabilities disclosed in Microsoft’s Patch Tuesday updates pose significant risks to critical infrastructure due to potential exploitation by threat actors. The confidence level in this assessment is moderate, given the technical nature of the vulnerabilities and the potential for rapid exploitation. Recommended action includes immediate patch implementation and enhanced monitoring of network activities for signs of exploitation.
2. Competing Hypotheses
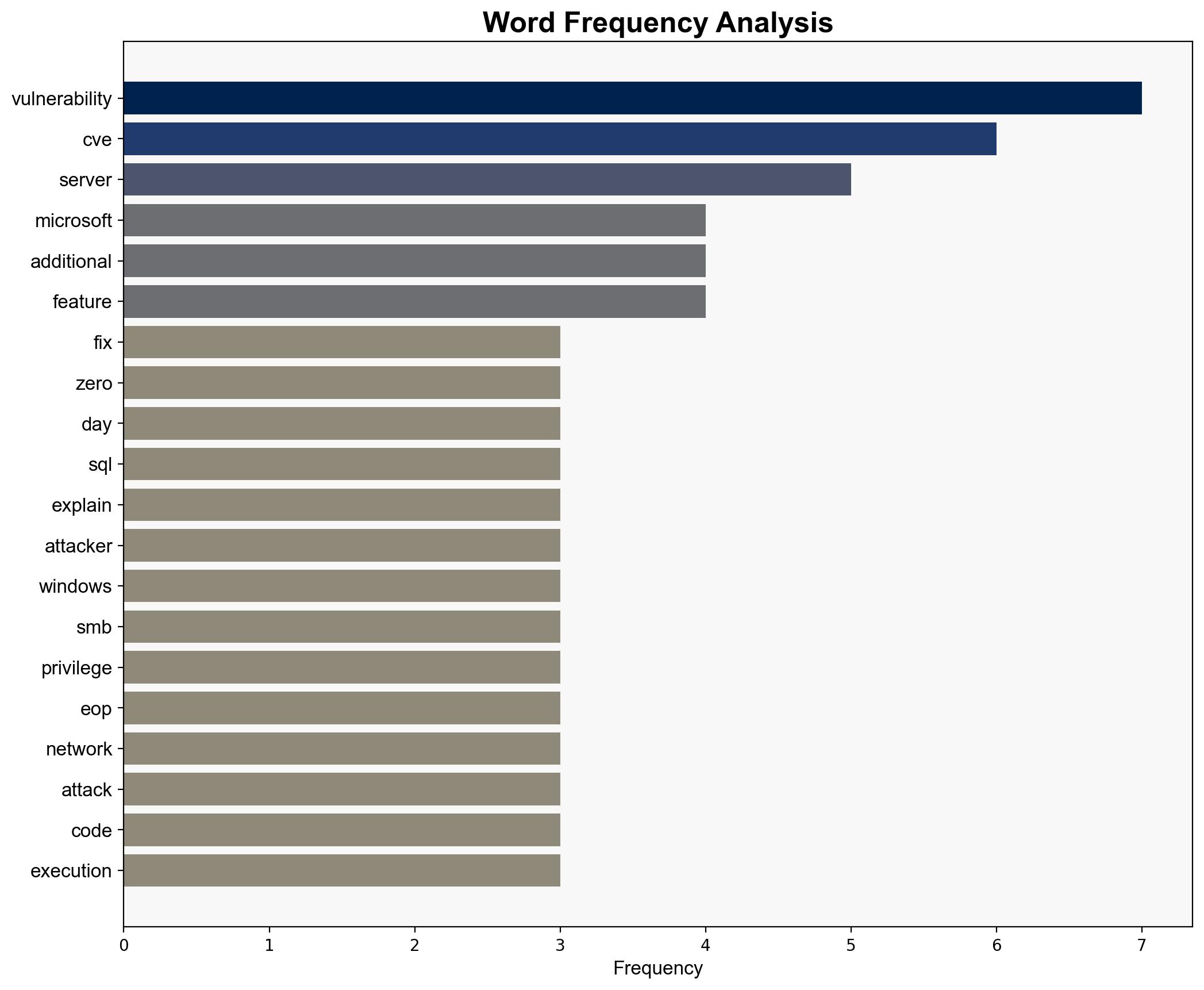
Hypothesis 1: The zero-day vulnerabilities, particularly the SQL Server and SMB elevation of privilege (EOP) issues, are likely to be exploited by threat actors targeting critical infrastructure, leading to significant disruptions.
Hypothesis 2: The vulnerabilities, while critical, will not be widely exploited due to existing mitigations and the complexity of executing successful attacks, resulting in limited impact.
Using ACH 2.0, Hypothesis 1 is better supported due to the nature of the vulnerabilities allowing remote code execution and privilege escalation, which are attractive to threat actors. The potential for these vulnerabilities to be used in targeted attacks against high-value targets like hospitals and airports increases their strategic importance.
3. Key Assumptions and Red Flags
– Assumption: Organizations will promptly apply patches and enable recommended security features.
– Red Flag: The assumption that existing mitigations are sufficient may overlook sophisticated threat actors’ capabilities.
– Blind Spot: Potential underestimation of the time required for organizations to fully implement patches and security features.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to significant disruptions in critical infrastructure, with cascading effects on economic stability and public safety. The geopolitical dimension includes potential attribution challenges and retaliatory actions if state-sponsored actors are involved. Cybersecurity threats could escalate if threat actors develop automated tools to exploit these vulnerabilities.
5. Recommendations and Outlook
- Immediate application of patches and enabling of security features such as SMB server signing.
- Enhanced network monitoring for unusual activities indicative of exploitation attempts.
- Scenario-based projections:
- Best Case: Rapid patch deployment prevents significant exploitation.
- Worst Case: Delayed patching leads to widespread disruption of critical services.
- Most Likely: Targeted attacks occur, but widespread impact is mitigated by timely patching and monitoring.
6. Key Individuals and Entities
– Adam Barnett
– Kev Breen
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus