Automated network pentesting uncovers what traditional tests missed – Help Net Security
Published on: 2025-09-10
Intelligence Report: Automated network pentesting uncovers what traditional tests missed – Help Net Security
1. BLUF (Bottom Line Up Front)
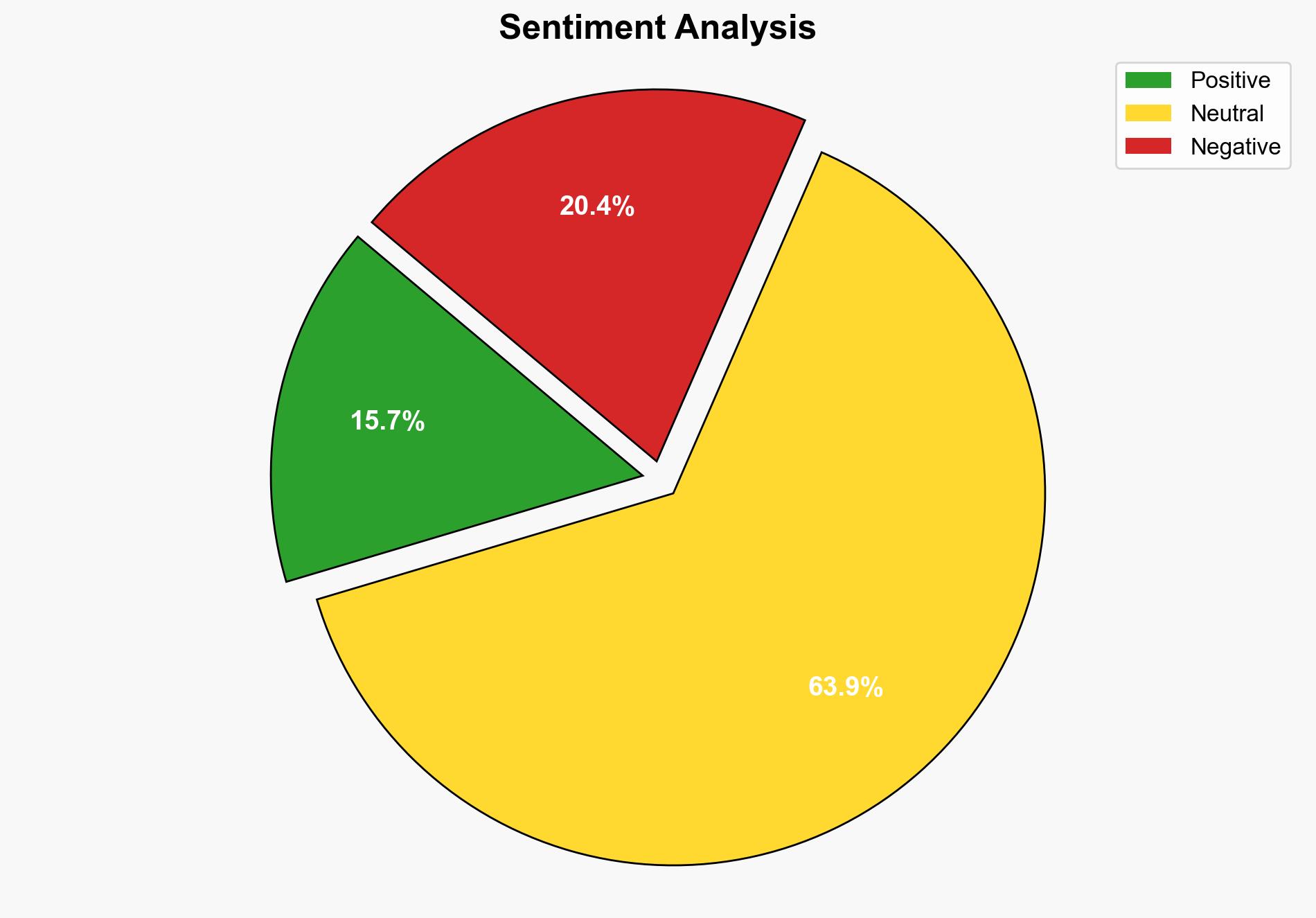
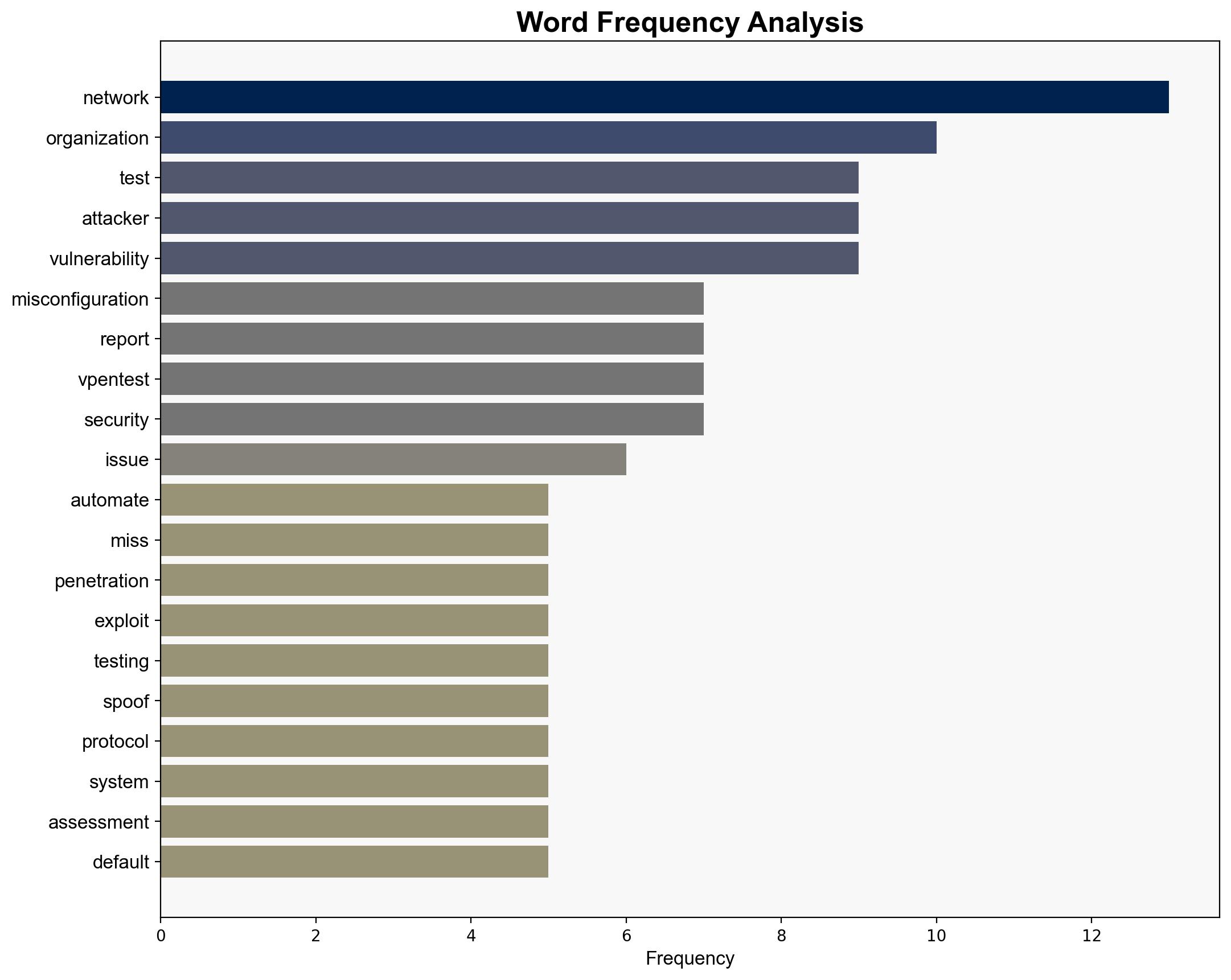
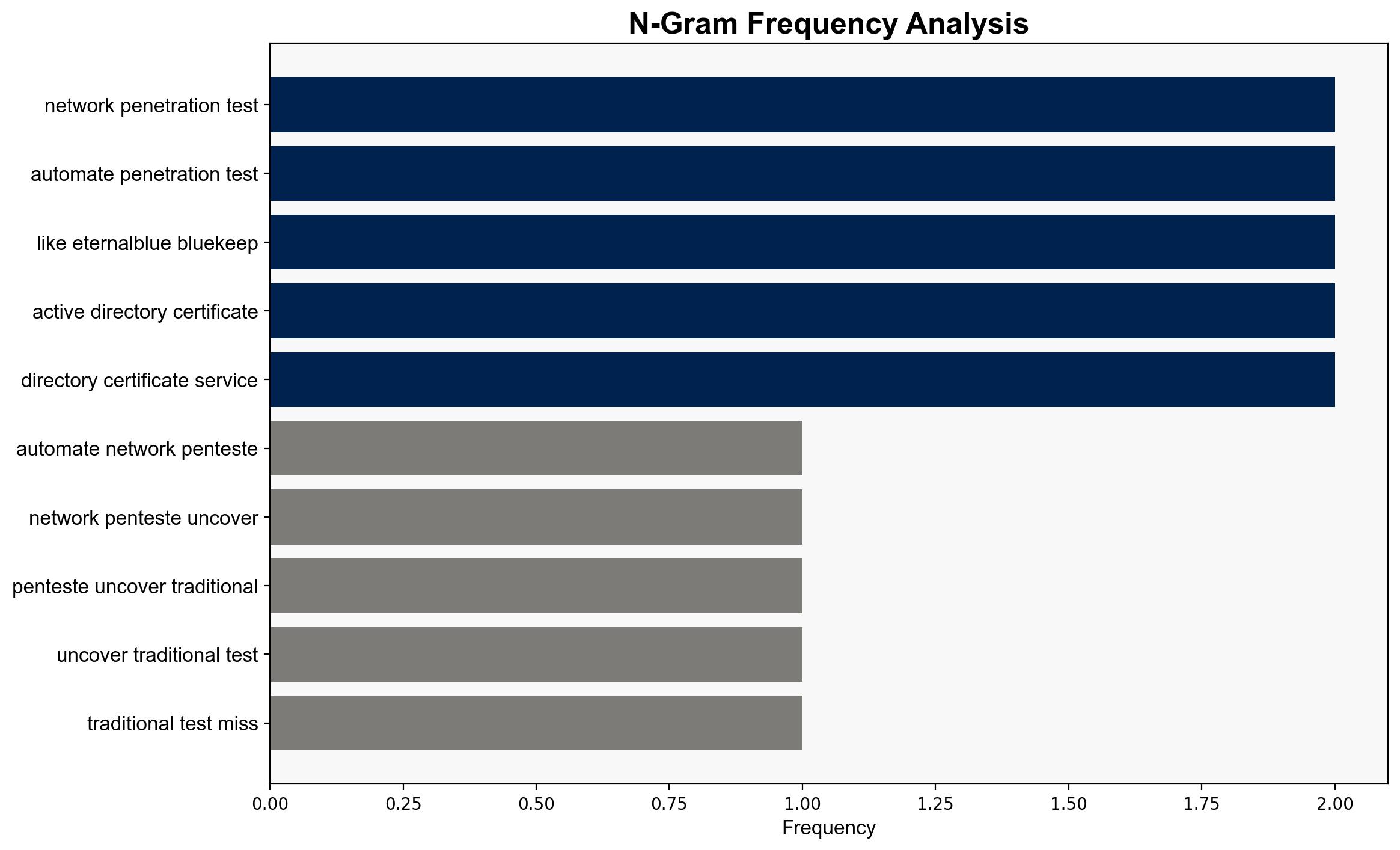
Automated network penetration testing, as demonstrated by Vonahi Security’s VPenTest platform, reveals vulnerabilities that traditional tests often miss, suggesting that continuous and automated testing is crucial for maintaining robust cybersecurity defenses. Confidence Level: High. Recommended Action: Organizations should integrate automated pentesting solutions into their cybersecurity strategies to ensure comprehensive vulnerability management and compliance with modern security frameworks.
2. Competing Hypotheses
Hypothesis 1: Automated pentesting platforms like VPenTest provide a more effective and comprehensive assessment of network vulnerabilities than traditional manual testing methods. This is due to their ability to simulate real-world attacker behavior and continuously test for vulnerabilities.
Hypothesis 2: The effectiveness of automated pentesting is overstated, and traditional methods remain essential due to their ability to provide context and nuanced insights that automated systems might overlook.
Using ACH 2.0, Hypothesis 1 is better supported as the report highlights specific vulnerabilities and misconfigurations that automated testing identified, which were missed by traditional methods. The continuous nature of automated testing also aligns with the dynamic nature of cyber threats.
3. Key Assumptions and Red Flags
Assumptions for Hypothesis 1 include the belief that automated systems can accurately simulate all potential attack vectors and that they are updated regularly to reflect the latest threats. A red flag is the potential over-reliance on automation, which may lead to complacency in manual oversight. For Hypothesis 2, the assumption is that human testers can consistently identify nuanced vulnerabilities, which may not always be the case given resource constraints.
4. Implications and Strategic Risks
The reliance on outdated systems and protocols presents a significant risk, as highlighted by the persistence of vulnerabilities like EternalBlue and BlueKeep. The economic implications include potential financial losses from breaches and non-compliance penalties. Cyber risks are heightened by the potential for attackers to exploit these overlooked vulnerabilities. Geopolitically, organizations failing to secure their networks may become targets for state-sponsored attacks.
5. Recommendations and Outlook
- Organizations should adopt a hybrid approach, integrating automated pentesting with periodic manual assessments to ensure comprehensive coverage.
- Invest in continuous training for cybersecurity teams to keep pace with evolving threats.
- Scenario Projections:
- Best Case: Organizations achieve full compliance and robust security posture through integrated testing strategies.
- Worst Case: Over-reliance on automation leads to significant breaches due to overlooked vulnerabilities.
- Most Likely: A gradual shift towards automated testing with improved security outcomes over time.
6. Key Individuals and Entities
Vonahi Security, VPenTest platform.
7. Thematic Tags
national security threats, cybersecurity, compliance, vulnerability management