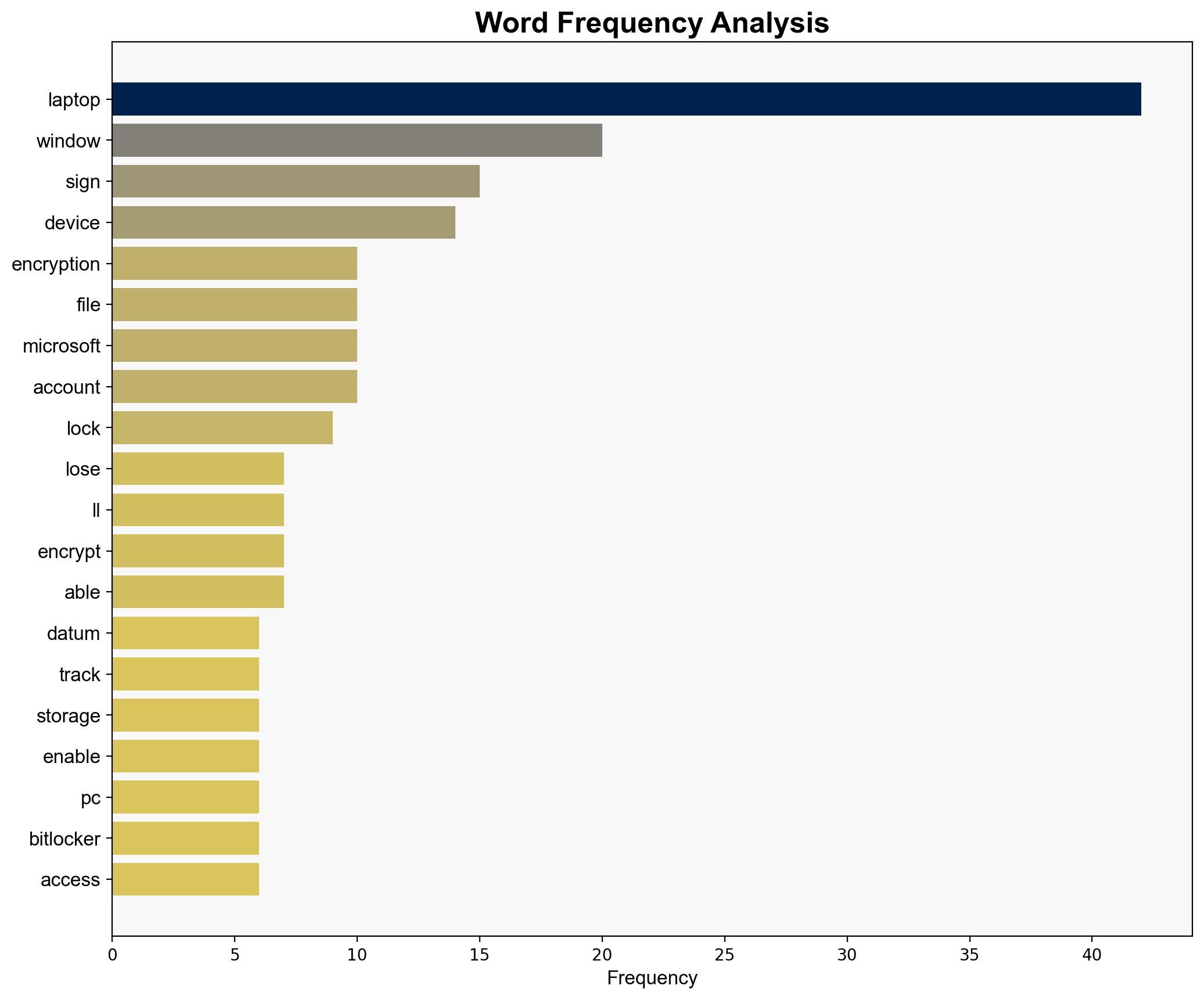
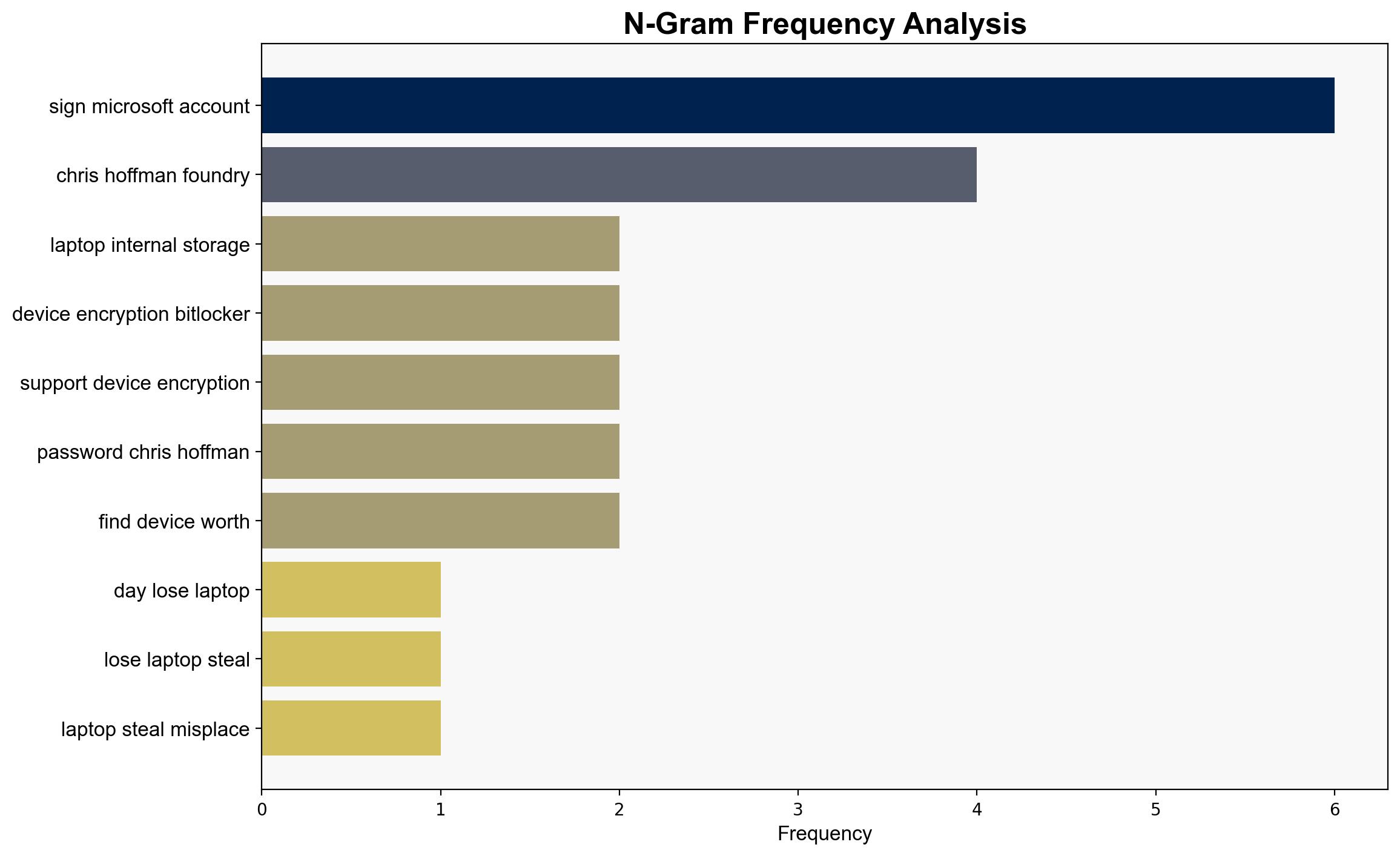
Dont wait until your laptop is stolen Change these 7 settings right now – PCWorld
Published on: 2025-09-11
Intelligence Report: Dont wait until your laptop is stolen Change these 7 settings right now – PCWorld
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that proactive security measures can significantly reduce the risk of data loss or theft from laptops. The recommendation is to implement encryption and tracking features immediately. Confidence level: High.
2. Competing Hypotheses
1. **Hypothesis 1**: Implementing proactive security settings on laptops, such as encryption and tracking, will effectively prevent unauthorized data access and facilitate recovery if the device is lost or stolen.
2. **Hypothesis 2**: Despite implementing security settings, the effectiveness of these measures is limited due to potential technical failures or user errors, leading to continued vulnerability to data breaches and theft.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Users will correctly implement and maintain security settings.
– Encryption and tracking technologies function as intended without technical failures.
– **Red Flags**:
– Over-reliance on technology without user education may lead to complacency.
– Potential gaps in security if users do not regularly update or verify settings.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: Failure to implement security measures could lead to significant data breaches, impacting personal and organizational data integrity.
– **Economic Risks**: Data loss or theft can result in financial losses due to recovery costs and potential legal liabilities.
– **Psychological Risks**: Users may experience increased anxiety and loss of trust in technology if security measures fail.
5. Recommendations and Outlook
- **Immediate Action**: Users should enable encryption and tracking features on their laptops to mitigate risks.
- **Education**: Conduct user training on maintaining and verifying security settings.
- **Scenario Projections**:
– **Best Case**: Users adopt security measures, significantly reducing data loss incidents.
– **Worst Case**: Security measures fail due to technical issues or user negligence, leading to widespread data breaches.
– **Most Likely**: A moderate reduction in data loss incidents as users gradually adopt and maintain security practices.
6. Key Individuals and Entities
– Chris Hoffman (mentioned as a source for insights on encryption and tracking technologies)
7. Thematic Tags
national security threats, cybersecurity, data protection, technology adoption