Windows KASLR Bypass CVE-2025-53136 – Crowdfense.com
Published on: 2025-09-11
Intelligence Report: Windows KASLR Bypass CVE-2025-53136 – Crowdfense.com
1. BLUF (Bottom Line Up Front)
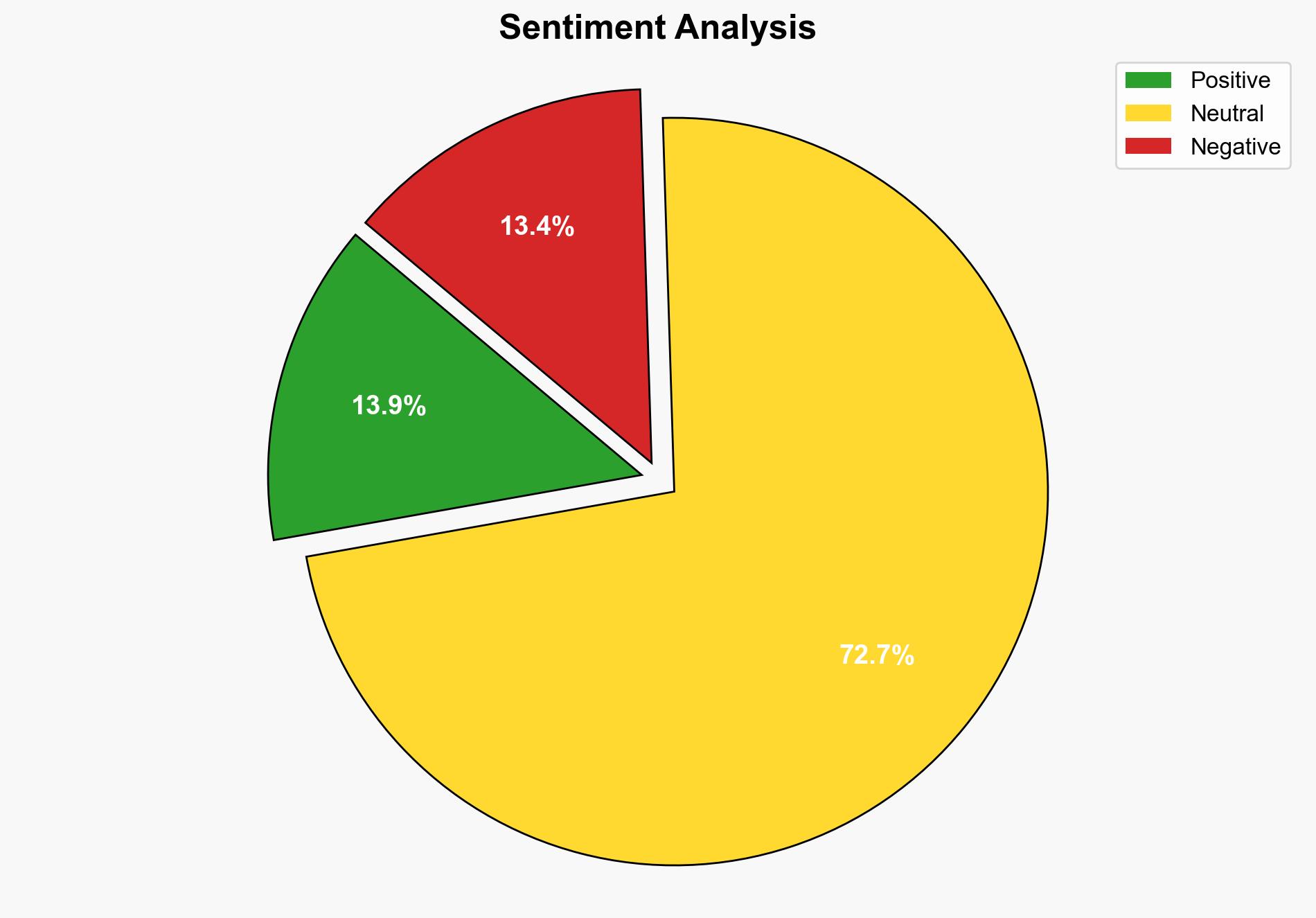
The analysis suggests that the vulnerability CVE-2025-53136 in Windows KASLR presents a significant security risk due to its potential for exploitation through a race condition. The most supported hypothesis is that the vulnerability, if not fully patched, could be exploited by adversaries to gain unauthorized access to sensitive information. Confidence in this assessment is moderate due to the complexity of the vulnerability and the potential for incomplete patching. It is recommended that Microsoft conduct a thorough review of the patch and consider additional security measures to mitigate this risk.
2. Competing Hypotheses
1. **Hypothesis A:** The vulnerability CVE-2025-53136 has been fully mitigated by Microsoft’s patch, effectively neutralizing the risk of exploitation.
2. **Hypothesis B:** The patch released by Microsoft does not fully address the vulnerability, leaving a residual risk that could be exploited by attackers.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis B is better supported due to the presence of a race condition that may not be completely resolved by the patch. The source indicates a potential gap in the patch, suggesting that the vulnerability might still be exploitable under certain conditions.
3. Key Assumptions and Red Flags
– **Assumptions:** It is assumed that the patch was intended to fully resolve the vulnerability. Another assumption is that the race condition is the primary mechanism of exploitation.
– **Red Flags:** The report mentions a “new bug” introduced by the patch, which could indicate incomplete testing or oversight. The mention of a “duplicate bug” raises concerns about the thoroughness of the vulnerability management process.
– **Blind Spots:** There is limited information on the specific conditions under which the race condition can be reliably exploited.
4. Implications and Strategic Risks
The persistence of this vulnerability could lead to significant cybersecurity threats, including unauthorized access to sensitive data and potential system compromise. If exploited, it could undermine trust in Microsoft’s security measures, impacting their reputation and user confidence. Additionally, it may encourage further research into similar vulnerabilities, potentially leading to a cascade of related exploits.
5. Recommendations and Outlook
- Microsoft should conduct a comprehensive review of the patch to ensure all aspects of the vulnerability are addressed.
- Implement additional security measures, such as enhanced monitoring and anomaly detection, to identify potential exploitation attempts.
- Scenario Projections:
- **Best Case:** The patch is revised, and the vulnerability is fully mitigated, restoring confidence in system security.
- **Worst Case:** The vulnerability is exploited in the wild, leading to significant data breaches and reputational damage.
- **Most Likely:** Partial mitigation is achieved, with ongoing monitoring required to prevent exploitation.
6. Key Individuals and Entities
The report does not specify individuals by name. The primary entity involved is Microsoft, responsible for addressing the vulnerability.
7. Thematic Tags
national security threats, cybersecurity, vulnerability management, software patching