The Hidden Threat How Sensitive Information Leakage Puts Your Business at Risk – Imperva.com
Published on: 2025-09-12
Intelligence Report: The Hidden Threat How Sensitive Information Leakage Puts Your Business at Risk – Imperva.com
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that sensitive information leakage is a critical, yet often overlooked, threat to businesses due to inadequate visibility and outdated security practices. Confidence level: High. Recommended action: Implement comprehensive monitoring and automated remediation solutions, such as those offered by Imperva, to mitigate this risk.
2. Competing Hypotheses
1. **Hypothesis A**: Sensitive information leakage is primarily due to misconfigured applications and poor development practices, which are not adequately addressed by current security measures.
2. **Hypothesis B**: Sensitive information leakage is a minor issue that is overemphasized by security vendors to promote their products, and most businesses are adequately protected by existing compliance standards.
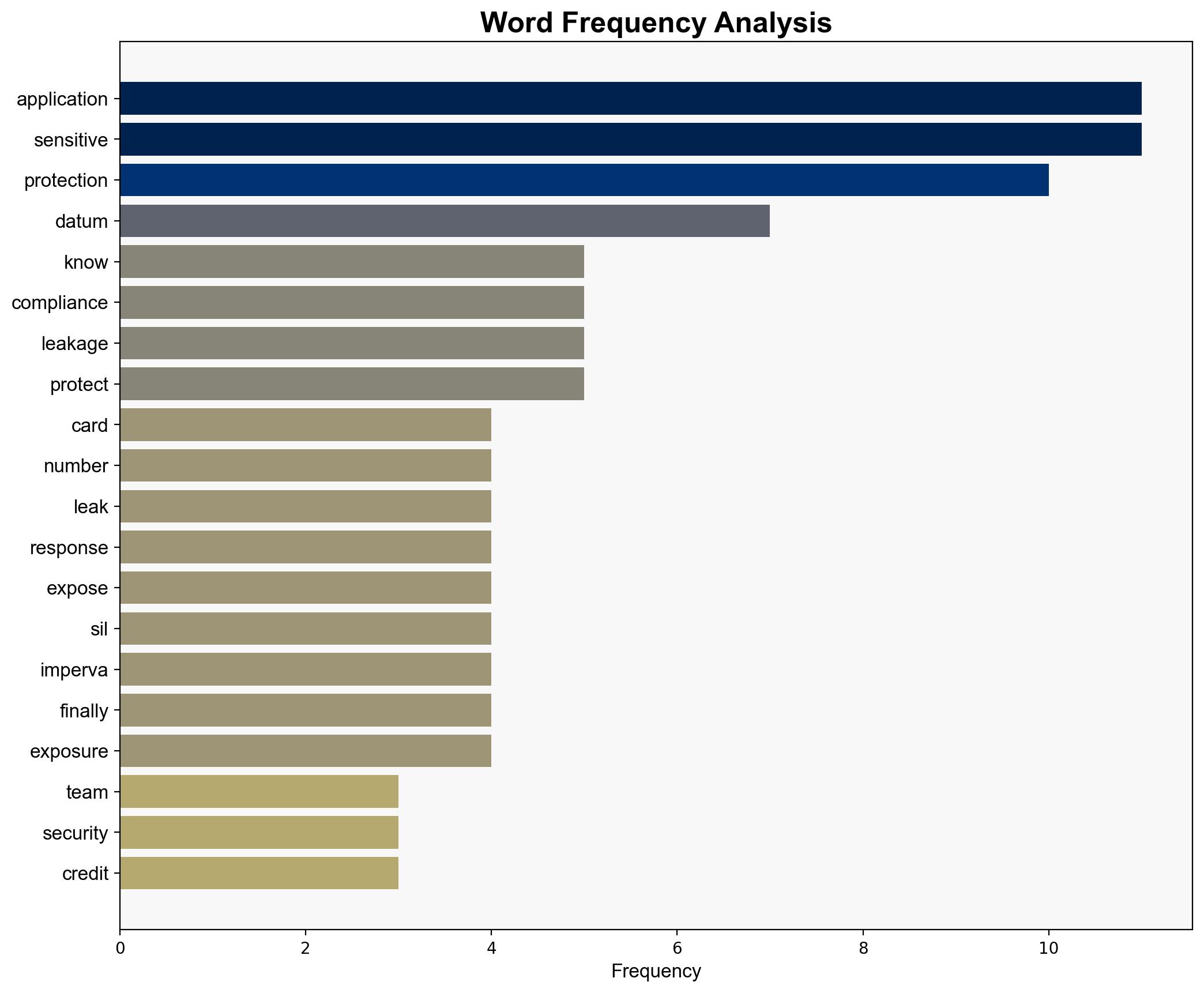
Using Analysis of Competing Hypotheses (ACH), Hypothesis A is better supported due to the detailed examples of leakage through API responses and debug logs, which are not typically covered by standard compliance checks.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that businesses lack visibility into their application traffic, leading to undetected data leaks. Another assumption is that existing compliance standards are insufficient for preventing such leaks.
– **Red Flags**: The potential bias in the source, as it is a vendor promoting its own solution, could lead to overstatement of the problem’s prevalence.
– **Blind Spots**: The report does not address the potential for internal threats or deliberate data exfiltration by insiders.
4. Implications and Strategic Risks
Sensitive information leakage can lead to significant financial penalties, reputational damage, and loss of customer trust. The economic impact could be severe, especially for businesses handling large volumes of sensitive data. Cyber risks include increased vulnerability to targeted attacks exploiting leaked information. Geopolitically, widespread data leaks could undermine trust in digital commerce platforms globally.
5. Recommendations and Outlook
- **Mitigation**: Deploy advanced monitoring tools that provide visibility into application traffic and automate the remediation of detected leaks.
- **Best Case Scenario**: Effective implementation of leakage protection leads to enhanced security posture and compliance, reducing risk of data breaches.
- **Worst Case Scenario**: Failure to address leakage results in a major data breach, leading to financial losses and reputational damage.
- **Most Likely Scenario**: Incremental improvements in security practices reduce leakage incidents, but ongoing vigilance is required to adapt to evolving threats.
6. Key Individuals and Entities
– Imperva (entity offering the solution)
7. Thematic Tags
cybersecurity, data protection, compliance, information leakage