Cisco fixes high-severity IOS XR flaws enabling image bypass and DoS – Securityaffairs.com
Published on: 2025-09-12
Intelligence Report: Cisco fixes high-severity IOS XR flaws enabling image bypass and DoS – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
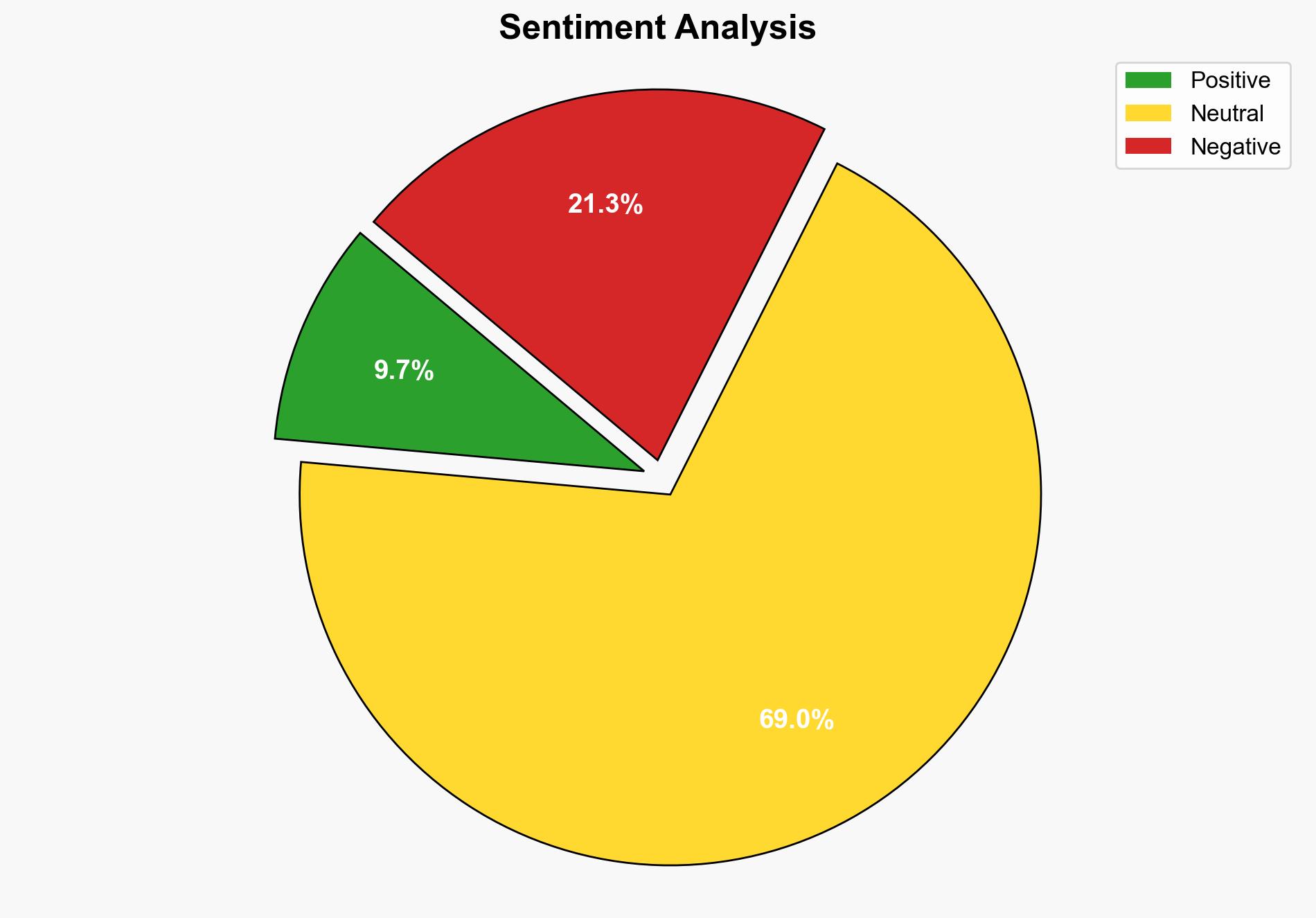
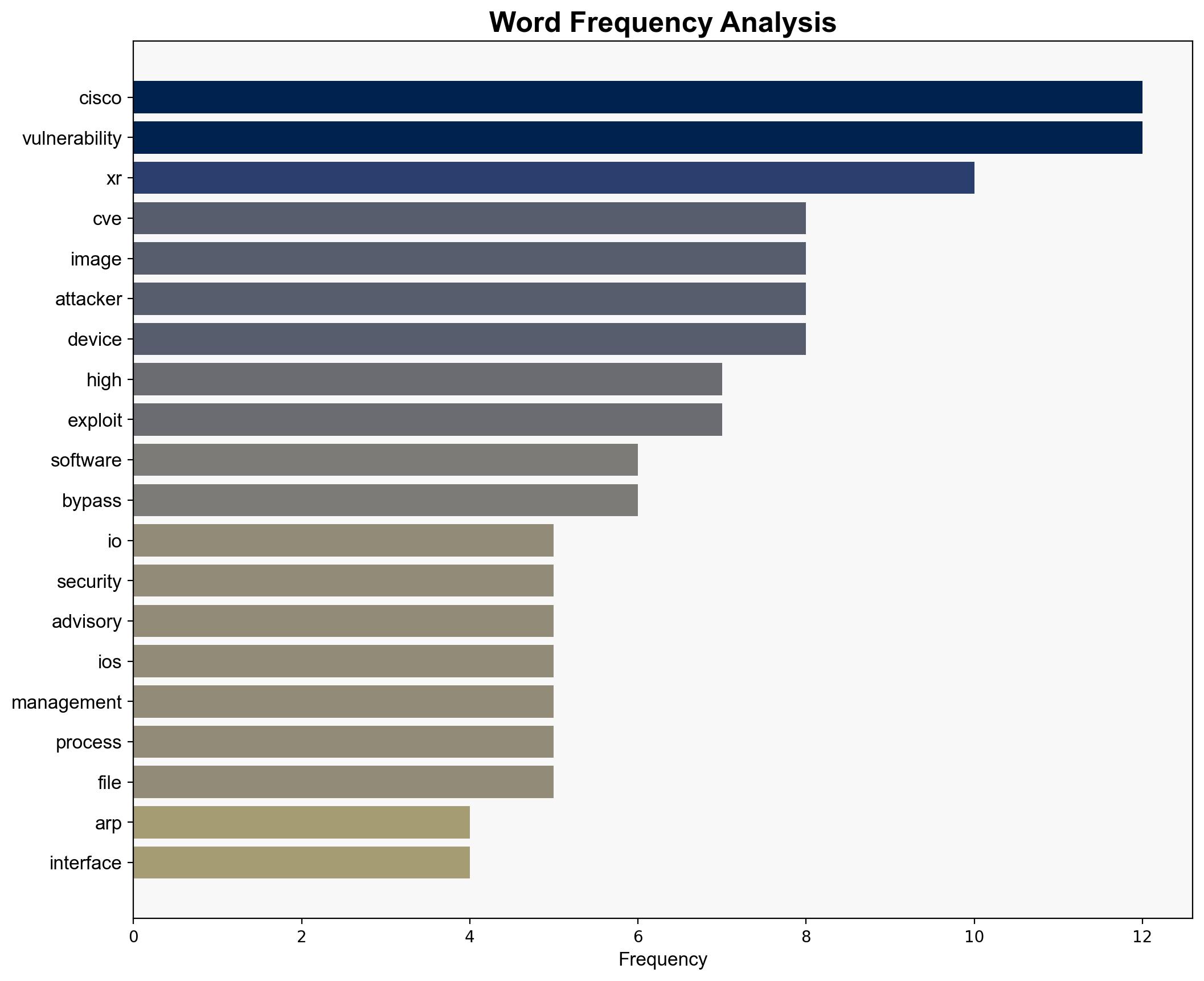
Cisco’s recent patching of high-severity vulnerabilities in its IOS XR software addresses critical security gaps that could be exploited for Denial of Service (DoS) attacks and unauthorized system access. The most supported hypothesis is that these vulnerabilities were not previously exploited in the wild but posed a significant risk if left unaddressed. Confidence level is moderate due to lack of direct evidence of exploitation. Recommended action is to ensure all systems are updated promptly and to enhance monitoring for any signs of attempted exploitation.
2. Competing Hypotheses
1. **Hypothesis A**: The vulnerabilities were discovered internally by Cisco or through responsible disclosure and have not been exploited in the wild. This hypothesis is supported by the timing of the advisory and the lack of reported incidents.
2. **Hypothesis B**: The vulnerabilities were being actively exploited by malicious actors, prompting an urgent response from Cisco. This hypothesis considers the high severity of the vulnerabilities and the potential for significant impact if exploited.
Using ACH 2.0, Hypothesis A is better supported by the available evidence, as there are no reports of active exploitation and the advisory follows a standard patch release cycle.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Cisco’s advisory accurately reflects the risk and that no active exploitation has occurred.
– **Red Flags**: Lack of specific details on how the vulnerabilities were discovered and the absence of third-party verification of non-exploitation.
– **Blind Spots**: Potential underreporting of exploitation attempts due to insufficient monitoring capabilities.
4. Implications and Strategic Risks
The vulnerabilities, if exploited, could lead to significant disruptions in networks relying on Cisco IOS XR, affecting critical infrastructure. The economic impact could be substantial if service providers experience outages. Geopolitically, exploitation by state actors could escalate tensions, especially if critical national infrastructure is targeted.
5. Recommendations and Outlook
- Ensure all affected systems are updated with the latest patches immediately.
- Enhance network monitoring to detect any unusual activity that may indicate exploitation attempts.
- Conduct a thorough review of network security protocols to prevent similar vulnerabilities.
- Scenario Projections:
- Best Case: No exploitation occurs, and systems remain secure post-update.
- Worst Case: Undetected exploitation leads to significant network outages and data breaches.
- Most Likely: Systems are updated without incident, but increased vigilance detects minor exploitation attempts.
6. Key Individuals and Entities
– Cisco Systems, Inc. (entity responsible for the software and advisory)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus