XenArmor Android Password Recovery Pro 2025 – Giveawayoftheday.com
Published on: 2025-09-15
Intelligence Report: XenArmor Android Password Recovery Pro 2025 – Giveawayoftheday.com
1. BLUF (Bottom Line Up Front)
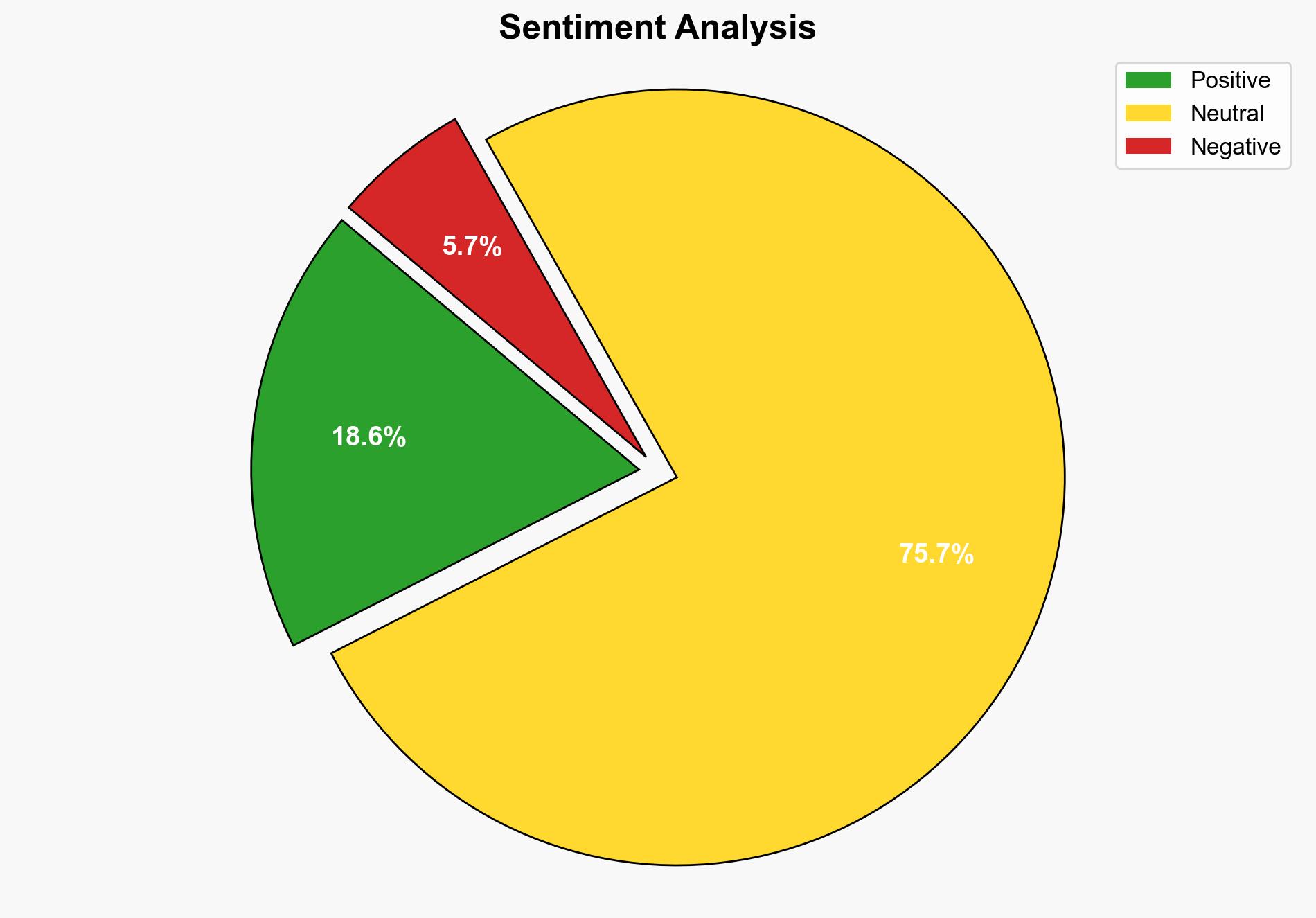
The analysis suggests that XenArmor Android Password Recovery Pro 2025 poses potential cybersecurity risks due to its capability to extract sensitive data from Android devices. The most supported hypothesis is that the software could be exploited by malicious actors for unauthorized data access. Confidence Level: Moderate. Recommended action is to monitor the distribution and usage of this software and assess its impact on device security.
2. Competing Hypotheses
Hypothesis 1: XenArmor Android Password Recovery Pro 2025 is primarily intended for legitimate use by law enforcement and forensic investigators to recover passwords and data from Android devices for legal purposes.
Hypothesis 2: The software could be misused by cybercriminals to gain unauthorized access to sensitive information on Android devices, posing a significant cybersecurity threat.
3. Key Assumptions and Red Flags
Assumptions:
– Hypothesis 1 assumes that the software is used exclusively by authorized personnel with proper oversight.
– Hypothesis 2 assumes that the software’s capabilities are accessible to individuals with malicious intent.
Red Flags:
– The software’s ability to extract data from both rooted and non-rooted devices raises concerns about potential misuse.
– Lack of clear restrictions or controls on who can access and use the software.
4. Implications and Strategic Risks
The software’s distribution as a free giveaway increases the risk of it falling into the hands of unauthorized users. This could lead to widespread unauthorized data access, compromising personal and organizational security. The potential for misuse could escalate into larger cybersecurity incidents, affecting trust in digital security measures and leading to economic and reputational damage.
5. Recommendations and Outlook
- Monitor the distribution channels and user demographics of the software to identify potential misuse patterns.
- Engage with software developers to implement stricter access controls and user verification processes.
- Best Case Scenario: The software is used responsibly by authorized entities, enhancing forensic capabilities.
- Worst Case Scenario: Widespread misuse leads to significant data breaches and loss of trust in digital security.
- Most Likely Scenario: Mixed usage with some instances of misuse, prompting regulatory scrutiny and potential legal action.
6. Key Individuals and Entities
– XenArmor (Developer)
– Giveawayoftheday.com (Distribution Platform)
– Potential users include law enforcement, forensic investigators, and cybercriminals.
7. Thematic Tags
national security threats, cybersecurity, data privacy, software misuse