Samsung Patches Zero-Day Exploited Against Android Users – Securityweek.com
Published on: 2025-09-15
Intelligence Report: Samsung Patches Zero-Day Exploited Against Android Users – Securityweek.com
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the zero-day vulnerability in Samsung devices was exploited by a commercial spyware vendor targeting specific users, including civil society individuals and government entities. Confidence in this hypothesis is moderate due to the involvement of sophisticated attack vectors and the timing of the exploit discovery. It is recommended that Samsung and other stakeholders enhance their threat intelligence sharing and patch management processes to mitigate future risks.
2. Competing Hypotheses
1. **Hypothesis A**: The zero-day vulnerability was exploited by a commercial spyware vendor targeting specific individuals, such as journalists and human rights defenders, using sophisticated attack methods.
2. **Hypothesis B**: The zero-day vulnerability was exploited by a state-sponsored actor aiming to gather intelligence on high-value targets through platforms like WhatsApp.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the involvement of a known commercial spyware vendor and the specific targeting of civil society individuals. The timing of the vulnerability report and the involvement of Meta’s WhatsApp security team further support this hypothesis. Hypothesis B lacks direct evidence linking state-sponsored actors to the exploit, making it less likely.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the exploitation was primarily driven by commercial motives rather than state interests. The involvement of WhatsApp and Amnesty International suggests a focus on civil society.
– **Red Flags**: The lack of detailed information on the exploit’s technical specifics and the absence of direct attribution to specific actors are significant gaps. The possibility of misinformation or disinformation campaigns cannot be ignored.
4. Implications and Strategic Risks
The exploitation of this vulnerability highlights the persistent threat posed by commercial spyware vendors. It underscores the need for robust cybersecurity measures and collaboration among tech companies. The potential for similar vulnerabilities to be exploited in the future poses a risk to national security, privacy, and the integrity of communication platforms. Geopolitically, this incident could strain relations between tech companies and governments, particularly if state-sponsored involvement is suspected.
5. Recommendations and Outlook
- Enhance collaboration between tech companies, government agencies, and civil society organizations to improve threat intelligence sharing.
- Implement rigorous patch management and vulnerability assessment protocols to prevent future exploits.
- Scenario Projections:
- Best Case: Improved security measures prevent further exploitation, and affected users are safeguarded.
- Worst Case: Additional vulnerabilities are discovered and exploited, leading to widespread data breaches and loss of trust in communication platforms.
- Most Likely: Continued vigilance and patching efforts mitigate immediate threats, but the risk of future exploits remains.
6. Key Individuals and Entities
– Meta’s WhatsApp security team
– Amnesty International’s Donncha Cearbhaill
– Samsung
7. Thematic Tags
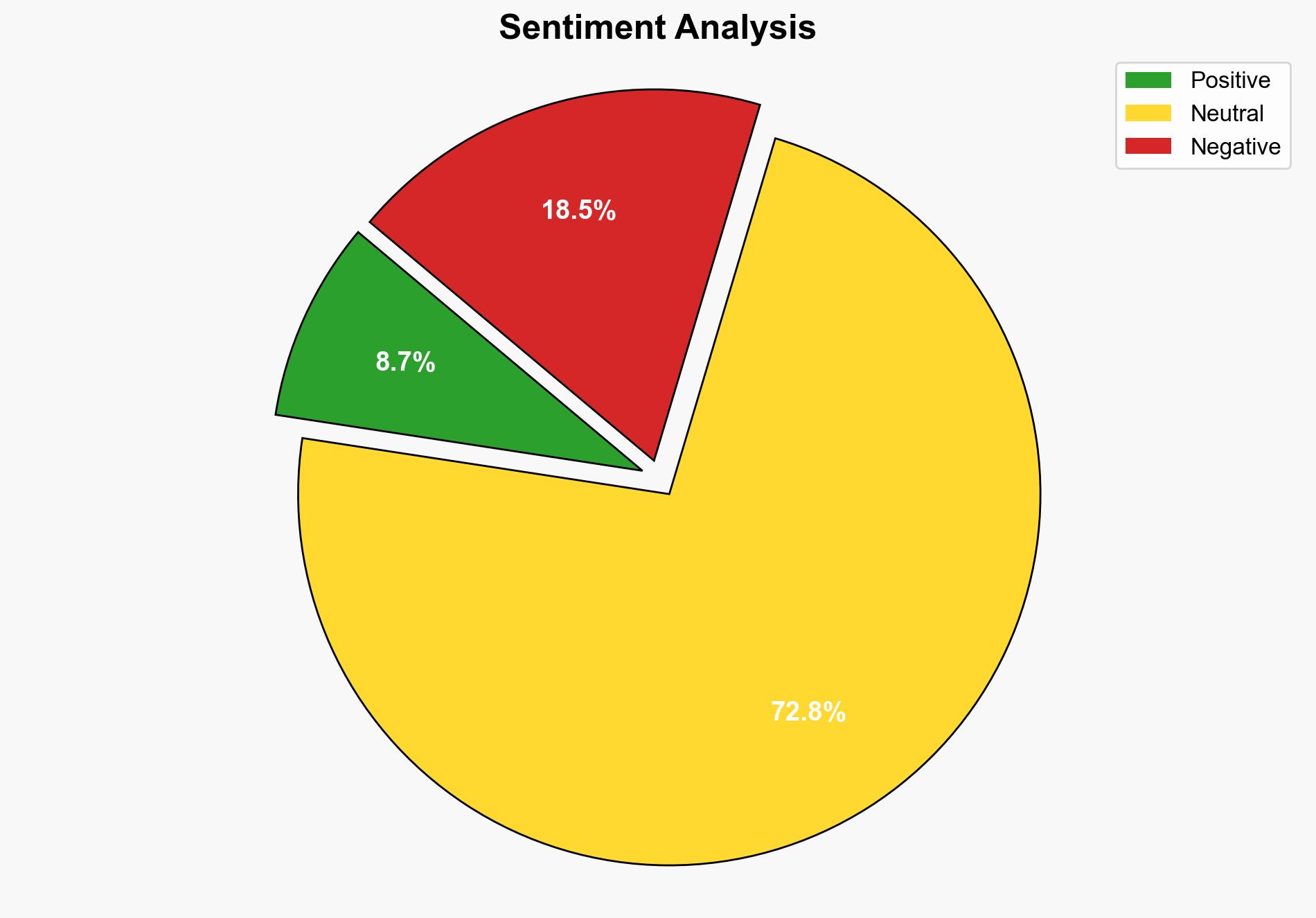
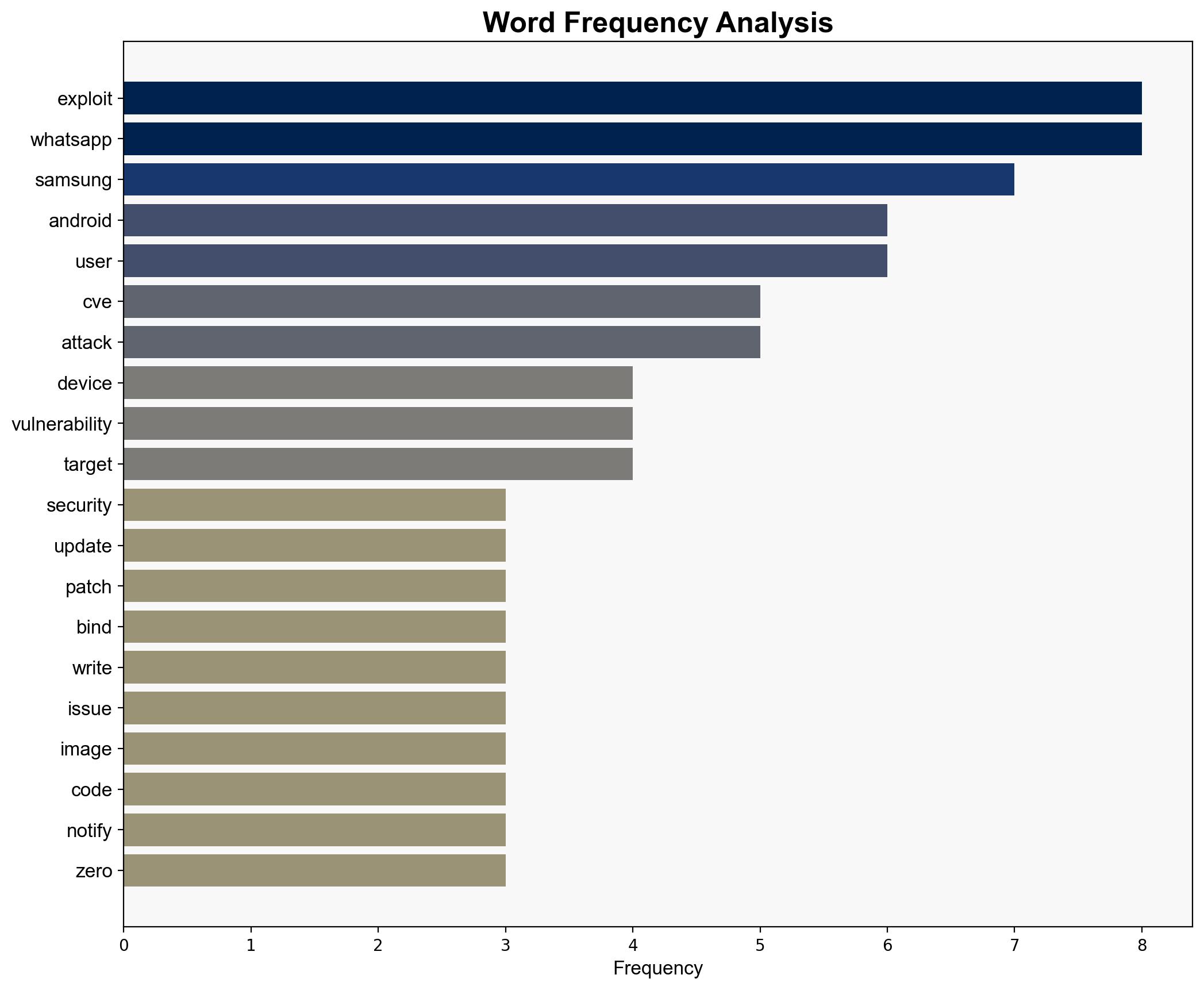
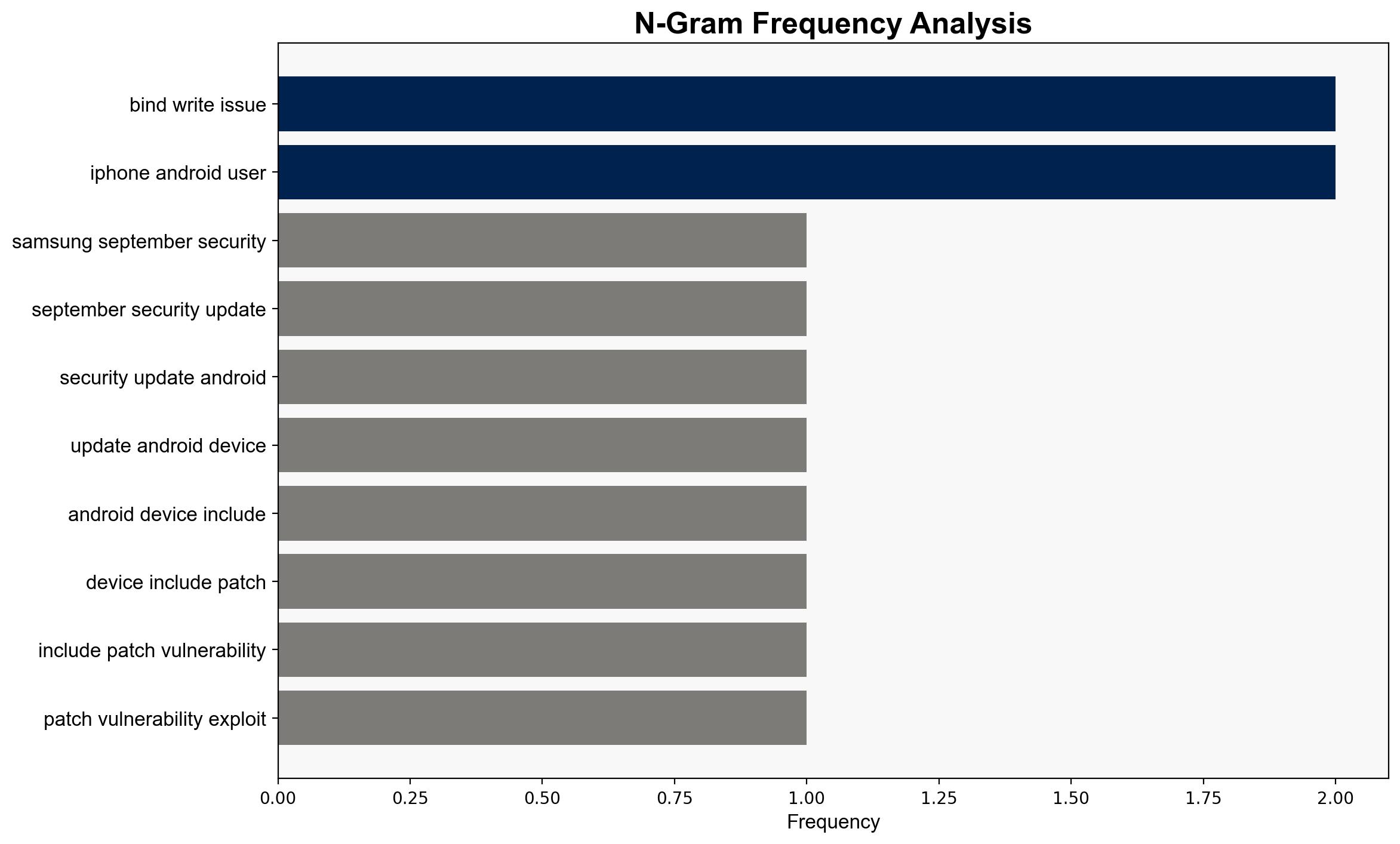
national security threats, cybersecurity, commercial spyware, civil society, vulnerability management