LockBit malware is back – and nastier than ever experts claim – TechRadar
Published on: 2025-09-29
Intelligence Report: LockBit malware is back – and nastier than ever experts claim – TechRadar
1. BLUF (Bottom Line Up Front)
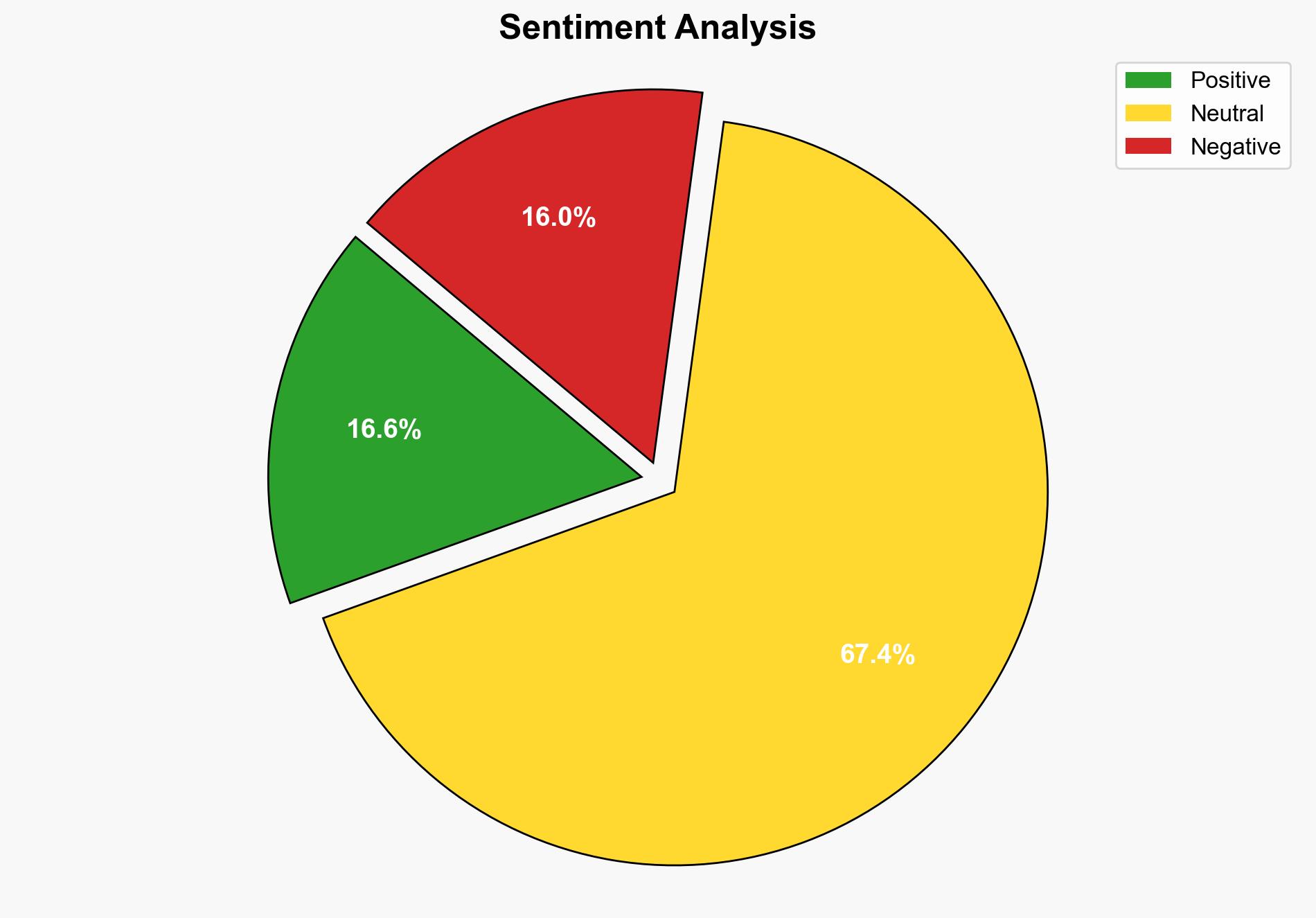
The resurgence of LockBit malware with enhanced capabilities poses a significant threat to cybersecurity across multiple platforms. The most supported hypothesis is that LockBit has evolved to exploit cross-platform vulnerabilities, increasing its threat level. Confidence in this assessment is high due to the technical improvements and active campaigns observed. Immediate action is recommended to bolster cross-platform cybersecurity defenses and enhance detection and response capabilities.
2. Competing Hypotheses
Hypothesis 1: LockBit has been significantly upgraded to target a broader range of systems, including Windows, Linux, and VMware ESXi, with advanced obfuscation techniques, indicating a strategic shift towards maximizing impact and evading detection.
Hypothesis 2: The observed enhancements in LockBit are primarily a response to law enforcement actions and previous exposure, aiming to rebuild its operational capabilities and reputation in the cybercriminal ecosystem.
Using Analysis of Competing Hypotheses (ACH), Hypothesis 1 is better supported due to the technical sophistication and cross-platform targeting observed, which aligns with a strategic offensive rather than a mere defensive adaptation.
3. Key Assumptions and Red Flags
Assumptions:
– LockBit’s enhancements are primarily driven by offensive strategic goals.
– The malware’s cross-platform capabilities are fully operational and effective.
Red Flags:
– Lack of direct evidence linking specific attacks to the new LockBit variant.
– Potential overestimation of LockBit’s capabilities based on limited technical analysis.
– The assumption that LockBit’s enhancements are solely for offensive purposes may overlook defensive motivations.
4. Implications and Strategic Risks
The enhanced LockBit malware increases the risk of widespread cyberattacks across various sectors, potentially leading to significant economic and operational disruptions. The cross-platform capabilities suggest a potential for cascading threats, where an attack on one system could compromise interconnected systems. Geopolitically, this may escalate tensions as states seek to attribute and respond to attacks. The psychological impact on organizations could lead to increased cybersecurity investments and policy changes.
5. Recommendations and Outlook
- Enhance cross-platform cybersecurity measures, focusing on detection and response capabilities for Windows, Linux, and VMware ESXi systems.
- Conduct regular threat assessments and simulations to prepare for potential LockBit attacks.
- Foster international collaboration to track and mitigate the spread of LockBit malware.
- Scenario Projections:
- Best Case: LockBit’s impact is minimized through effective international cooperation and rapid response measures.
- Worst Case: LockBit causes widespread disruption across critical infrastructure, leading to significant economic and geopolitical consequences.
- Most Likely: LockBit continues to pose a persistent threat, with periodic successful attacks prompting ongoing cybersecurity enhancements.
6. Key Individuals and Entities
No specific individuals are identified in the source text. Entities involved include LockBit, Trend Micro, and law enforcement agencies involved in Operation Crono.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus