Too many Cisco ASA firewalls still unsecure despite zero-day attack alerts – Help Net Security
Published on: 2025-10-01
Intelligence Report: Too many Cisco ASA firewalls still unsecure despite zero-day attack alerts – Help Net Security
1. BLUF (Bottom Line Up Front)
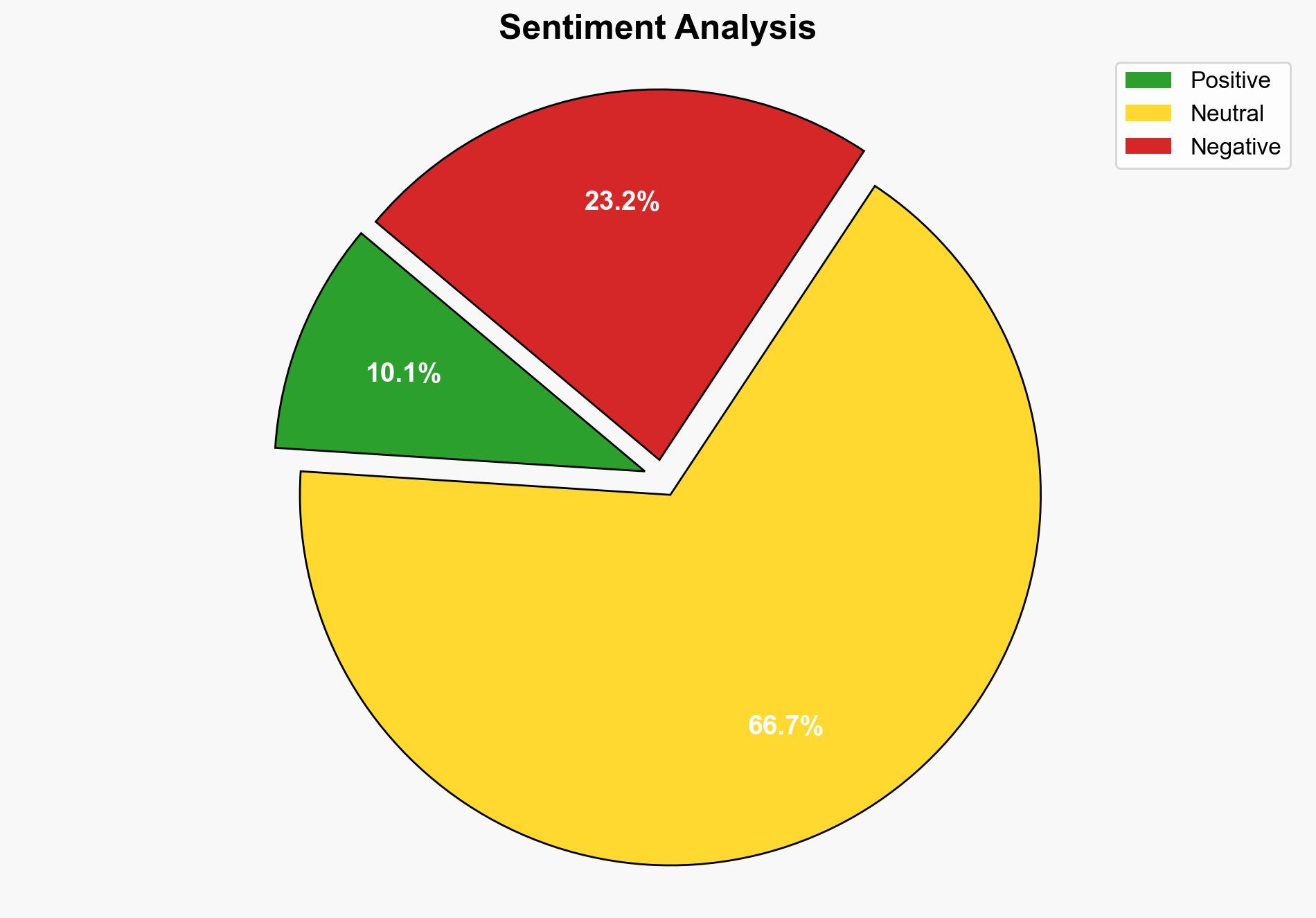
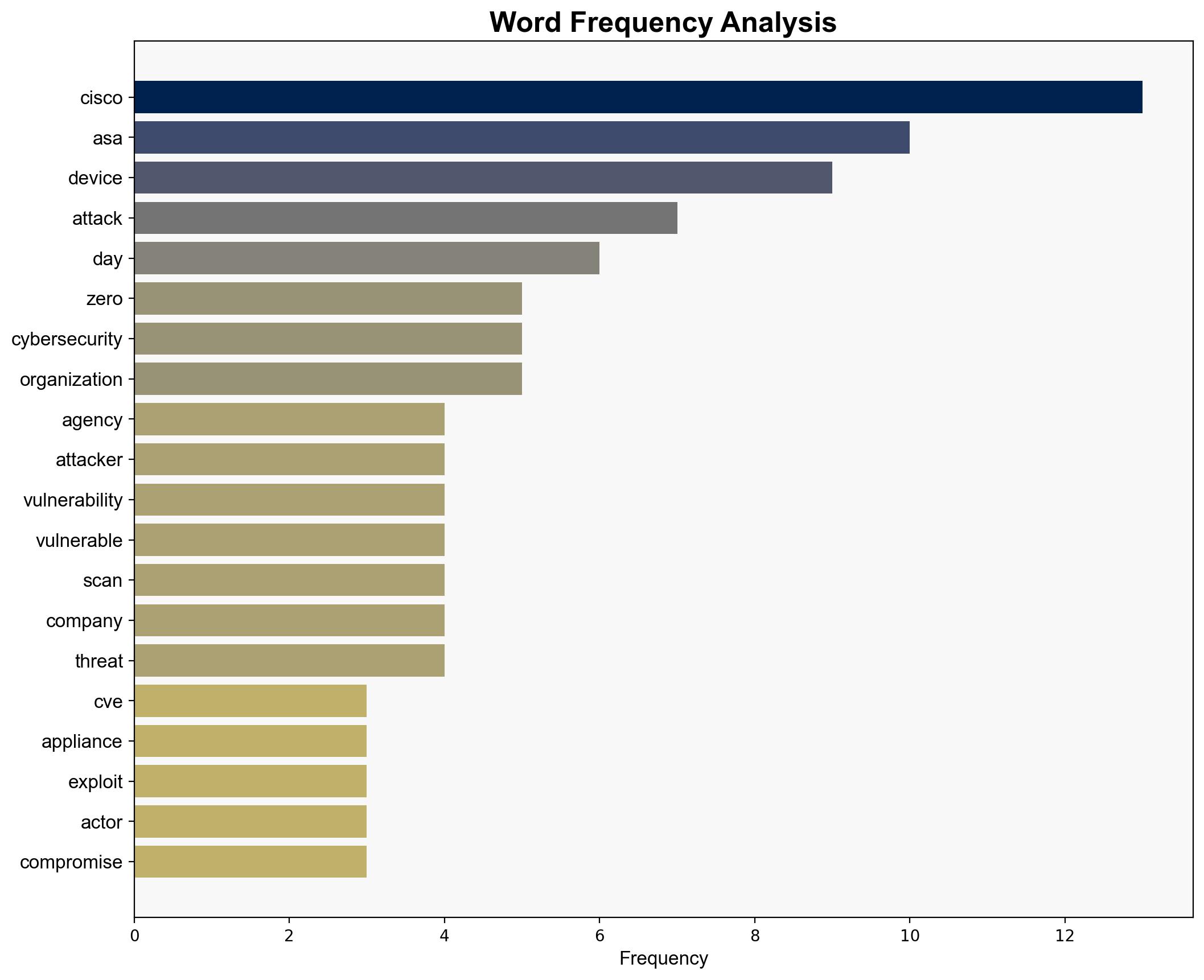
There is a significant cybersecurity threat due to unpatched Cisco ASA firewalls vulnerable to zero-day exploits. The most supported hypothesis is that state-sponsored actors are exploiting these vulnerabilities to target high-value government and private sector organizations. Confidence level: High. Recommended action: Immediate patching and upgrading of vulnerable systems, enhanced monitoring for indicators of compromise, and coordination with cybersecurity agencies for threat intelligence sharing.
2. Competing Hypotheses
Hypothesis 1: State-sponsored actors are exploiting Cisco ASA vulnerabilities to gather intelligence from government and high-value private sector targets. This is supported by the use of advanced evasion techniques and custom malware, which are indicative of well-resourced actors.
Hypothesis 2: Cybercriminal groups are exploiting these vulnerabilities for financial gain, targeting organizations with weaker cybersecurity postures. This is supported by the widespread scanning activity and the potential for ransom or data theft.
3. Key Assumptions and Red Flags
– Assumption: The sophistication of the attack suggests state-sponsored involvement. However, this could be a false flag operation by cybercriminals to mislead investigators.
– Red Flag: The lack of specific attribution to a known threat actor group increases uncertainty about the true nature of the threat.
– Blind Spot: Potential underreporting of compromised systems due to organizations’ reluctance to disclose breaches.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to significant data breaches, loss of sensitive information, and disruption of critical infrastructure. There is a risk of cascading effects if attackers leverage compromised systems to launch further attacks. Geopolitically, this could escalate tensions if state-sponsored involvement is confirmed. Economically, affected organizations may face financial losses and reputational damage.
5. Recommendations and Outlook
- Immediate patching and upgrading of all vulnerable Cisco ASA devices.
- Enhanced network monitoring for indicators of compromise and unusual activity.
- Coordination with national cybersecurity agencies for intelligence sharing and support.
- Scenario Projections:
- Best Case: Rapid patch deployment mitigates the threat with minimal impact.
- Worst Case: Widespread exploitation leads to significant data breaches and geopolitical tensions.
- Most Likely: Continued exploitation by both state-sponsored and criminal actors, with moderate impact on targeted organizations.
6. Key Individuals and Entities
– Cisco Systems (manufacturer of the affected devices)
– Shadowserver Foundation (identified vulnerable instances)
– Greynoise (detected scanning activity)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus