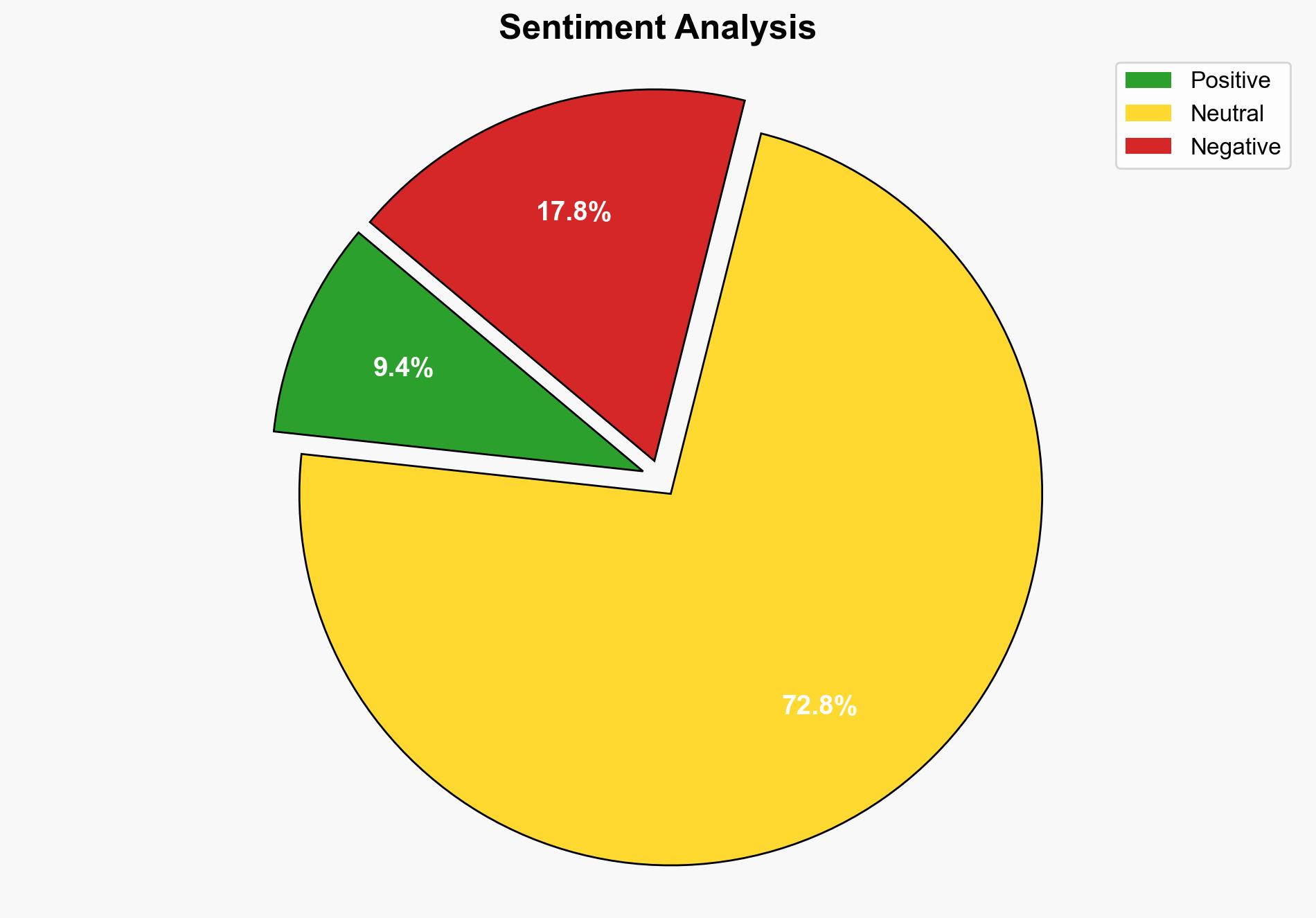
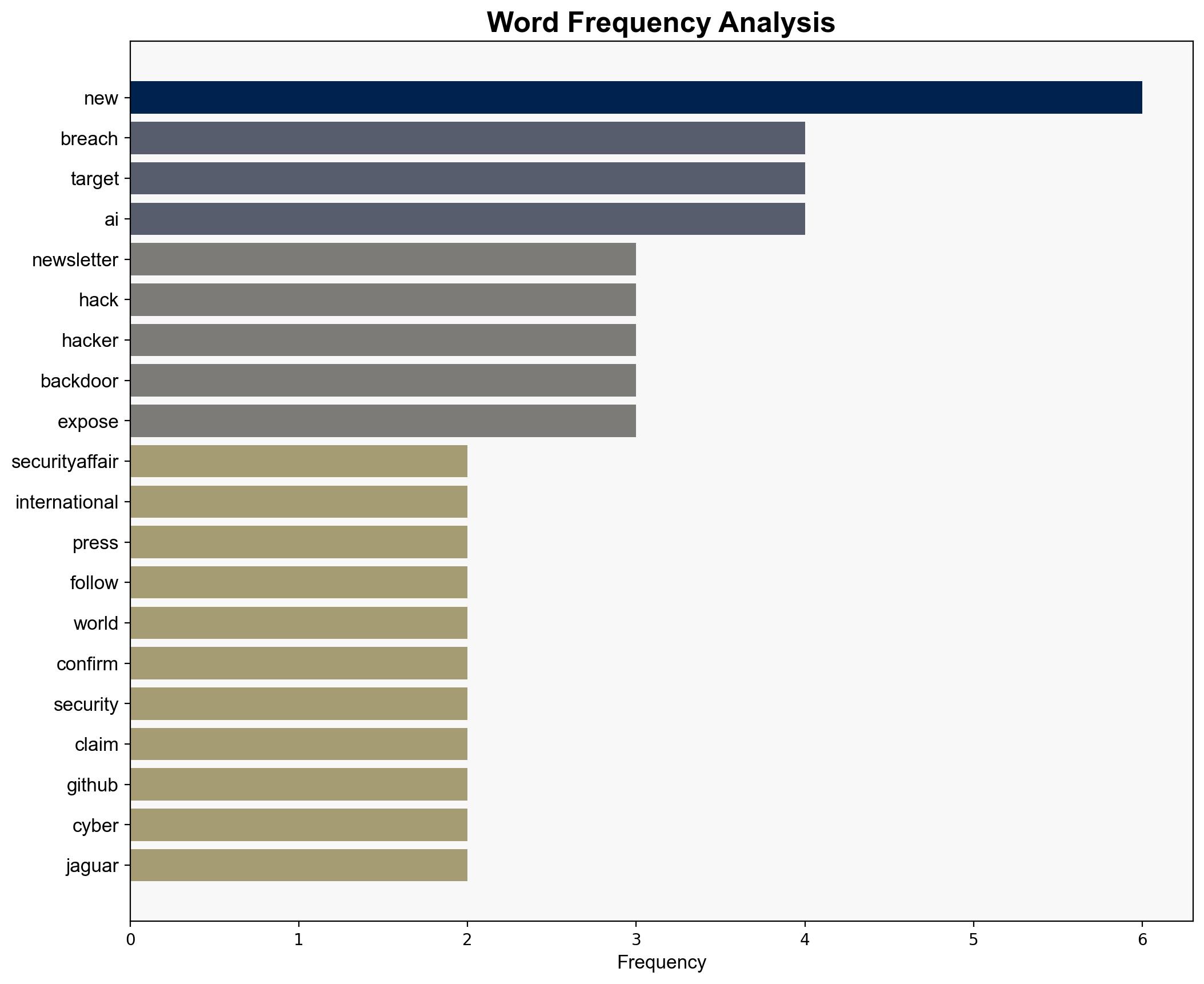
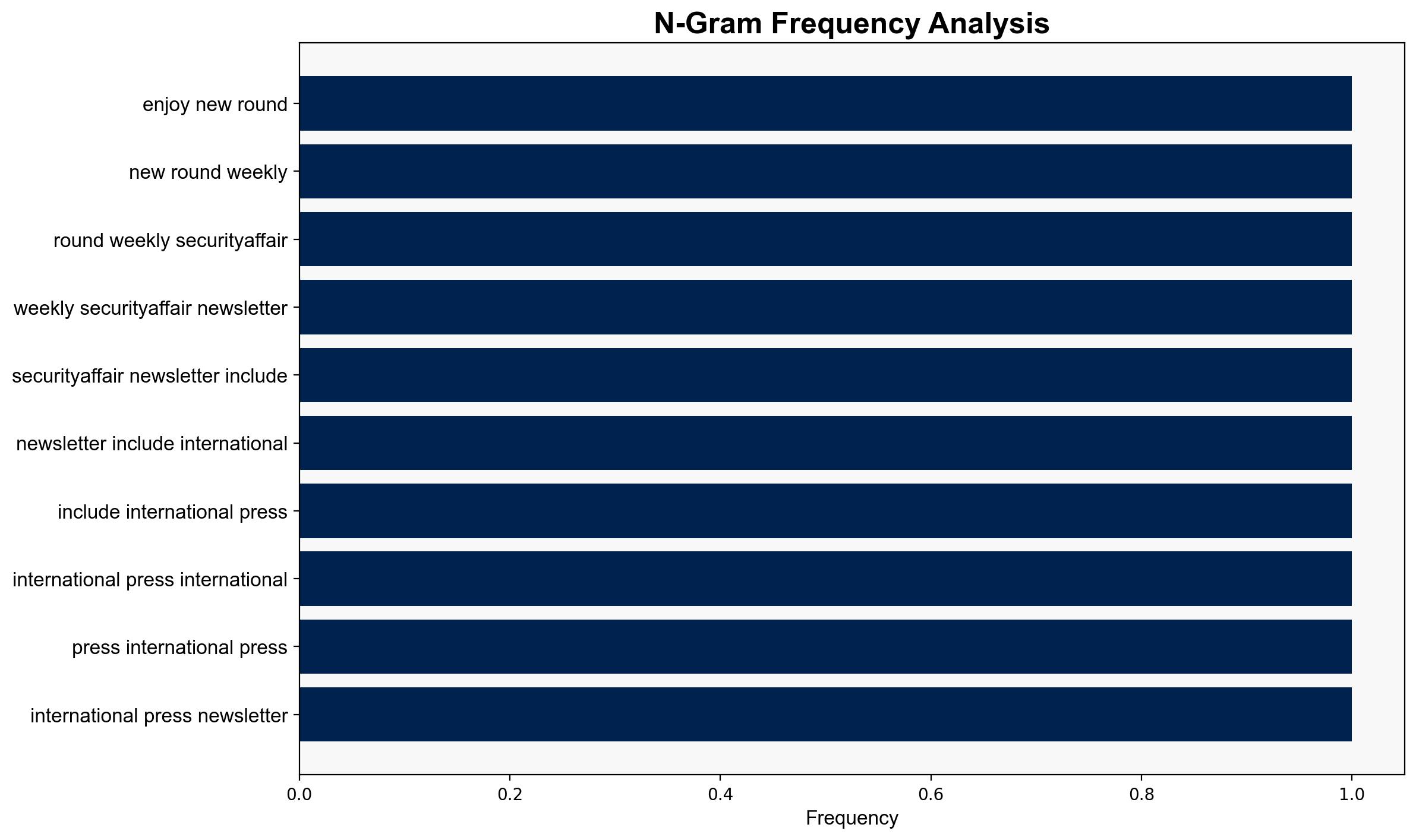
Security Affairs newsletter Round 544 by Pierluigi Paganini INTERNATIONAL EDITION – Securityaffairs.com
Published on: 2025-10-05
Intelligence Report: Security Affairs newsletter Round 544 by Pierluigi Paganini INTERNATIONAL EDITION – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that there is an increasing trend of sophisticated cyber threats targeting both governmental and private sectors globally, with a particular focus on exploiting vulnerabilities in emerging technologies such as AI and confidential computing. Confidence level: Moderate. Recommended action: Enhance international collaboration on cybersecurity measures and invest in advanced threat detection and mitigation technologies.
2. Competing Hypotheses
1. **Hypothesis A**: The surge in cyber incidents is primarily driven by state-sponsored actors aiming to destabilize geopolitical adversaries and gain strategic advantages.
2. **Hypothesis B**: The increase in cyber threats is largely due to non-state actors, including organized crime groups, exploiting technological vulnerabilities for financial gain.
Using ACH 2.0, Hypothesis A is better supported due to the presence of state-level espionage activities, such as the rare Russian espionage case and the Confucius espionage operation, indicating strategic intent beyond financial motives.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that state-sponsored actors have the capability and intent to conduct complex cyber operations. Non-state actors are assumed to prioritize financial over strategic objectives.
– **Red Flags**: The lack of detailed attribution in some reported incidents raises questions about the true origin of the threats. The potential for misattribution or underestimation of non-state actor capabilities is a concern.
4. Implications and Strategic Risks
The patterns suggest a potential escalation in cyber warfare, with significant risks to critical infrastructure and economic stability. The exploitation of AI vulnerabilities could lead to cascading failures in automated systems, while geopolitical tensions may be exacerbated by cyber espionage and interference in democratic processes.
5. Recommendations and Outlook
- Enhance international cybersecurity cooperation and intelligence sharing to address state-sponsored threats.
- Invest in AI and confidential computing security to mitigate emerging vulnerabilities.
- Scenario Projections:
- Best Case: Strengthened global cybersecurity frameworks reduce the incidence of major cyber incidents.
- Worst Case: Escalation of cyber warfare leads to significant geopolitical instability and economic disruption.
- Most Likely: Continued increase in cyber threats with gradual improvements in defensive measures.
6. Key Individuals and Entities
– Pierluigi Paganini (source)
– Confucius (espionage group)
– Russian espionage case (unnamed individuals)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus