45 Million Offered in New Cloud Hacking Competition – Securityweek.com
Published on: 2025-10-06
Intelligence Report: 45 Million Offered in New Cloud Hacking Competition – Securityweek.com
1. BLUF (Bottom Line Up Front)
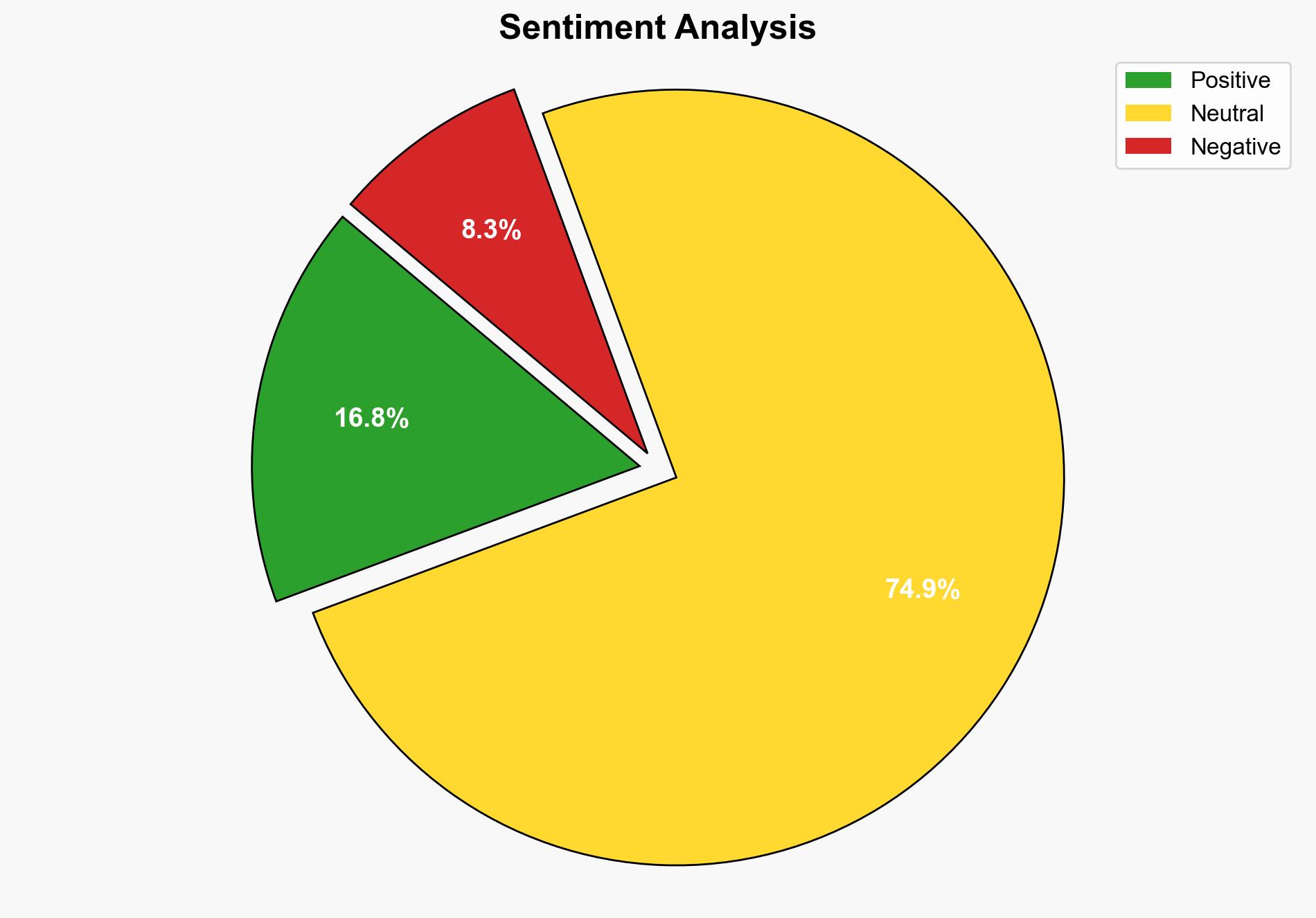
The announcement of the Zeroday Cloud hacking competition by Wiz, with substantial financial incentives, is likely to enhance cloud security by identifying vulnerabilities. However, it may also expose sensitive systems to increased risk if exploits are not responsibly disclosed. The hypothesis that the competition will primarily bolster security is better supported. Confidence level: Moderate. Recommended action: Monitor the competition’s outcomes and ensure responsible disclosure practices are enforced.
2. Competing Hypotheses
Hypothesis 1: The competition will significantly improve cloud security by incentivizing researchers to discover and report vulnerabilities, leading to enhanced defenses and patching of critical systems.
Hypothesis 2: The competition could inadvertently increase security risks by encouraging the discovery of vulnerabilities that may be exploited by malicious actors before they are patched.
3. Key Assumptions and Red Flags
Assumptions:
– Participants will adhere to ethical guidelines and responsibly disclose vulnerabilities.
– Companies will act swiftly to patch identified vulnerabilities.
– The competition will attract skilled researchers rather than malicious actors.
Red Flags:
– Potential for discovered vulnerabilities to be leaked or sold on the black market.
– Similarity in rules to Trend Micro’s Pwn2Own could indicate a lack of originality or potential legal disputes.
– Google’s acquisition of Wiz may influence the competition’s outcomes or objectives.
4. Implications and Strategic Risks
The competition could lead to a rapid identification of vulnerabilities, prompting immediate security improvements. However, if vulnerabilities are not disclosed responsibly, there is a risk of exploitation by cybercriminals. The competition’s high profile may attract both ethical and unethical participants, increasing the complexity of managing discovered vulnerabilities. The involvement of major cloud providers like AWS, Google Cloud, and Microsoft suggests significant industry impact.
5. Recommendations and Outlook
- Ensure robust mechanisms for responsible disclosure and rapid patching of vulnerabilities.
- Monitor for any unauthorized disclosures or sales of vulnerabilities on illicit platforms.
- Scenario Projections:
- Best Case: Significant vulnerabilities are identified and patched, leading to improved cloud security.
- Worst Case: Vulnerabilities are exploited before patching, resulting in major security breaches.
- Most Likely: A mix of responsible disclosures and minor exploitations, with overall net positive impact on security.
6. Key Individuals and Entities
– Nir Ohfeld, Head of Vulnerability Research at Wiz
– Google, AWS, Microsoft (as major cloud providers involved)
7. Thematic Tags
national security threats, cybersecurity, cloud computing, vulnerability disclosure, ethical hacking