Hackers Extorting Salesforce After Stealing Data From Dozens of Customers – Securityweek.com
Published on: 2025-10-06
Intelligence Report: Hackers Extorting Salesforce After Stealing Data From Dozens of Customers – Securityweek.com
1. BLUF (Bottom Line Up Front)
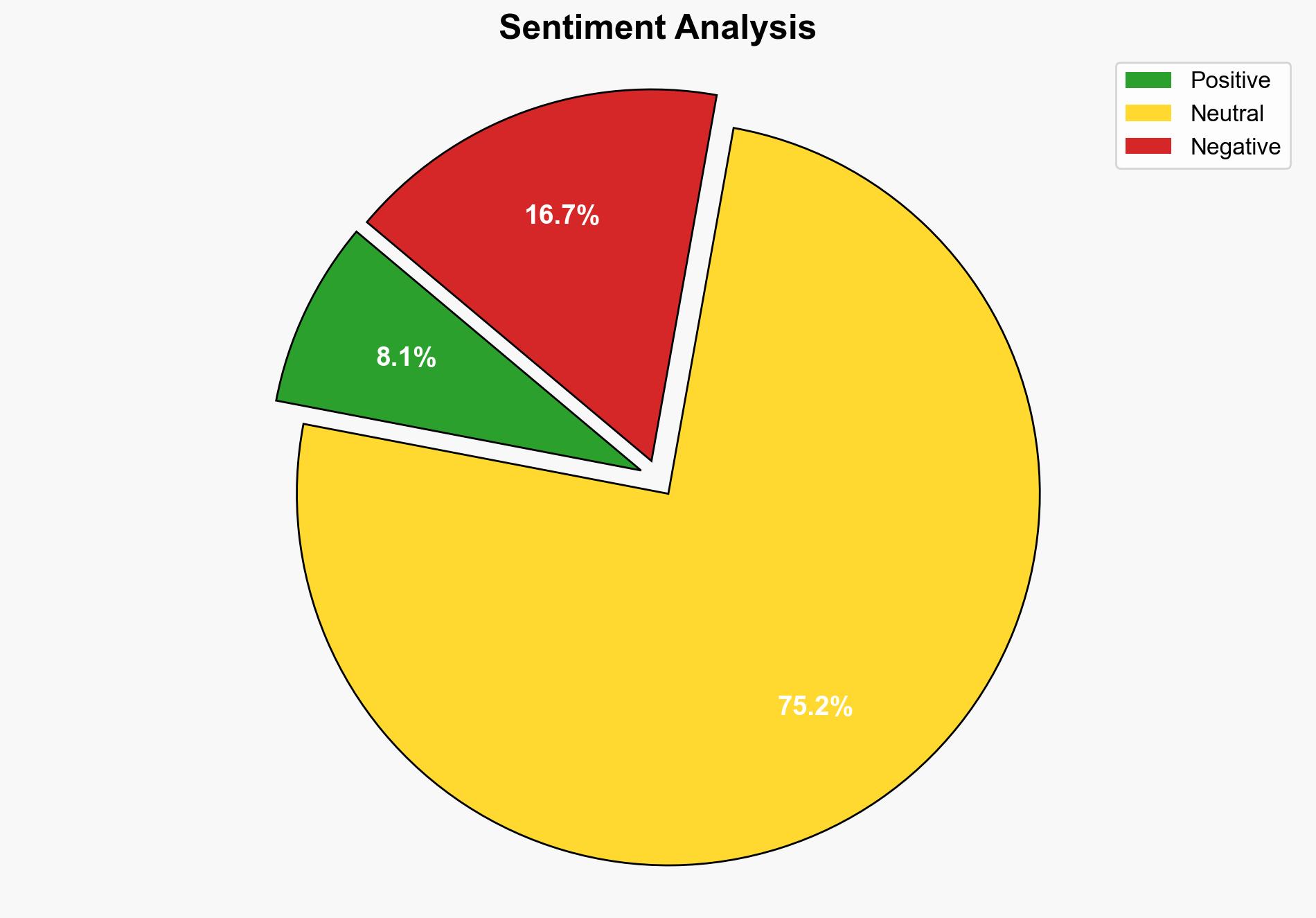
The most supported hypothesis is that the threat actors, potentially a coalition of Scatter Spider and ShinyHunter, are leveraging social engineering tactics to exploit vulnerabilities in Salesforce’s customer instances rather than a direct breach of Salesforce’s platform. Confidence level: Moderate. Recommended action: Enhance security measures focusing on user credential protection and social engineering defenses, while maintaining close collaboration with affected customers and law enforcement.
2. Competing Hypotheses
1. **Hypothesis A**: The hackers have exploited a vulnerability in Salesforce’s platform, leading to the theft of data from multiple customers. This scenario suggests a systemic security flaw within Salesforce.
2. **Hypothesis B**: The hackers have utilized social engineering techniques to gain unauthorized access to Salesforce customer accounts, rather than exploiting a platform vulnerability. This scenario indicates a targeted attack on user credentials rather than Salesforce’s infrastructure itself.
Using ACH 2.0, Hypothesis B is better supported due to the lack of evidence indicating a direct breach of Salesforce’s platform. The emphasis on social engineering and credential theft aligns with known tactics of the involved hacker groups.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Hypothesis A assumes a technical vulnerability in Salesforce, which is not substantiated by current evidence.
– Hypothesis B assumes successful social engineering attacks, which aligns with the group’s known capabilities.
– **Red Flags**:
– The claim of a platform vulnerability lacks corroboration from Salesforce or independent security assessments.
– The rapid emergence of Scatter Spider and ShinyHunter post-retirement raises questions about the continuity and evolution of threat actor tactics.
4. Implications and Strategic Risks
– **Economic Risks**: Potential financial losses for affected companies due to data breaches and ransom payments.
– **Cyber Risks**: Increased likelihood of similar attacks on other CRM platforms if attackers are successful.
– **Geopolitical Risks**: Potential strain on international relations if state actors are suspected of involvement or if major global brands are affected.
– **Psychological Risks**: Erosion of trust in cloud-based CRM solutions, impacting Salesforce’s market position and customer confidence.
5. Recommendations and Outlook
- Enhance user education on social engineering and phishing threats to reduce credential theft risks.
- Implement multi-factor authentication and regular security audits for Salesforce instances.
- Scenario Projections:
- Best Case: Strengthened security measures prevent further breaches, and attackers are apprehended.
- Worst Case: Attackers successfully exploit other CRM platforms, leading to widespread data breaches.
- Most Likely: Continued attempts at social engineering with varying degrees of success, prompting ongoing security enhancements.
6. Key Individuals and Entities
– Scatter Spider
– ShinyHunter
– Brian Soby (AppOmni Founder and CTO)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus