Palo Alto systems warning issued among huge surge in scanning attacks – but it says everything is fine – TechRadar
Published on: 2025-10-06
Intelligence Report: Palo Alto systems warning issued among huge surge in scanning attacks – but it says everything is fine – TechRadar
1. BLUF (Bottom Line Up Front)
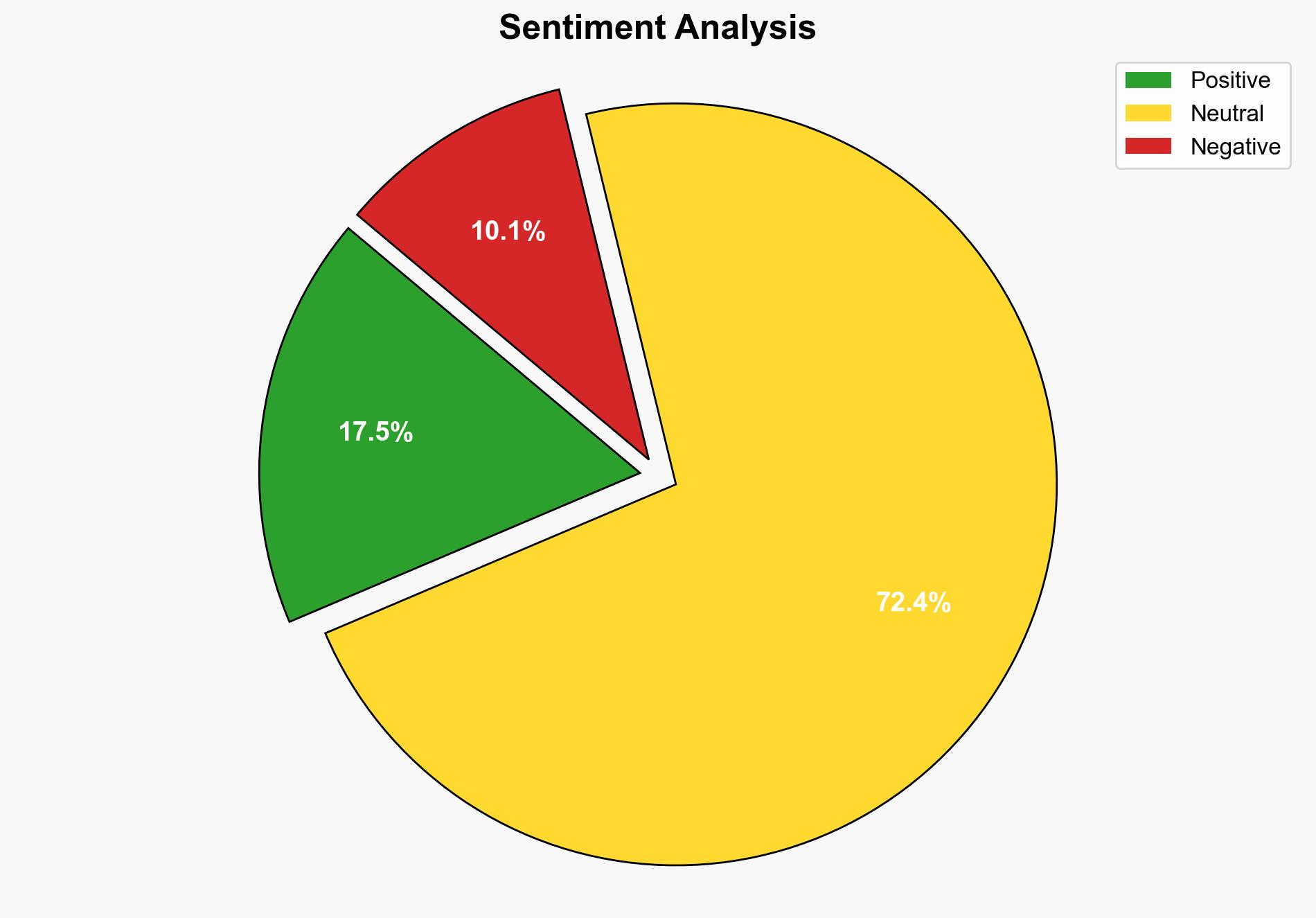
The analysis suggests that the surge in scanning attacks targeting Palo Alto systems may either be a routine reconnaissance activity or an indication of a potential vulnerability being exploited. The most supported hypothesis is that this is a reconnaissance effort, given the lack of evidence of compromise and the company’s confidence in their security measures. Confidence level: Moderate. Recommended action: Enhance monitoring and threat intelligence sharing to preemptively address any emerging threats.
2. Competing Hypotheses
1. **Routine Reconnaissance Activity**: The surge in scanning attacks is part of regular reconnaissance efforts by threat actors to map potential targets without any immediate intent to exploit vulnerabilities. This is supported by the lack of evidence of compromise and the confidence expressed by Palo Alto in their security systems.
2. **Emerging Exploitation Attempt**: The scanning surge indicates an emerging threat where actors are actively seeking to exploit a newly discovered vulnerability in Palo Alto systems. This hypothesis considers the unusual spike in scanning activity and the geographic distribution of the IP addresses involved.
3. Key Assumptions and Red Flags
– **Assumptions**: The assumption that Palo Alto’s security measures are robust enough to prevent any exploitation attempts is critical. Another assumption is that the scanning activity is not yet linked to any known exploit.
– **Red Flags**: The geographic concentration of scanning activity in Pakistan and the presence of IP addresses from countries like Russia and the Netherlands could indicate coordinated efforts. The absence of detailed technical analysis on the nature of the scans is a blind spot.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: If the scanning is a precursor to an exploitation attempt, it could lead to significant breaches affecting global networks relying on Palo Alto systems.
– **Geopolitical Risks**: The involvement of IP addresses from multiple countries could complicate diplomatic relations and lead to increased scrutiny of international cyber activities.
– **Economic Risks**: Successful exploitation could result in financial losses for affected organizations and damage to Palo Alto’s reputation.
5. Recommendations and Outlook
- Enhance real-time monitoring and analysis of network traffic to detect any anomalies that may indicate exploitation attempts.
- Strengthen collaboration with international cybersecurity agencies to share intelligence and coordinate responses.
- Scenario Projections:
- Best Case: The activity is purely reconnaissance, and no vulnerabilities are exploited.
- Worst Case: A vulnerability is exploited, leading to widespread breaches.
- Most Likely: Continued reconnaissance with no immediate exploitation.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Entities involved include Palo Alto Networks and GreyNoise.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus