How to get better results from bug bounty programs without wasting money – Help Net Security
Published on: 2025-10-07
Intelligence Report: How to get better results from bug bounty programs without wasting money – Help Net Security
1. BLUF (Bottom Line Up Front)
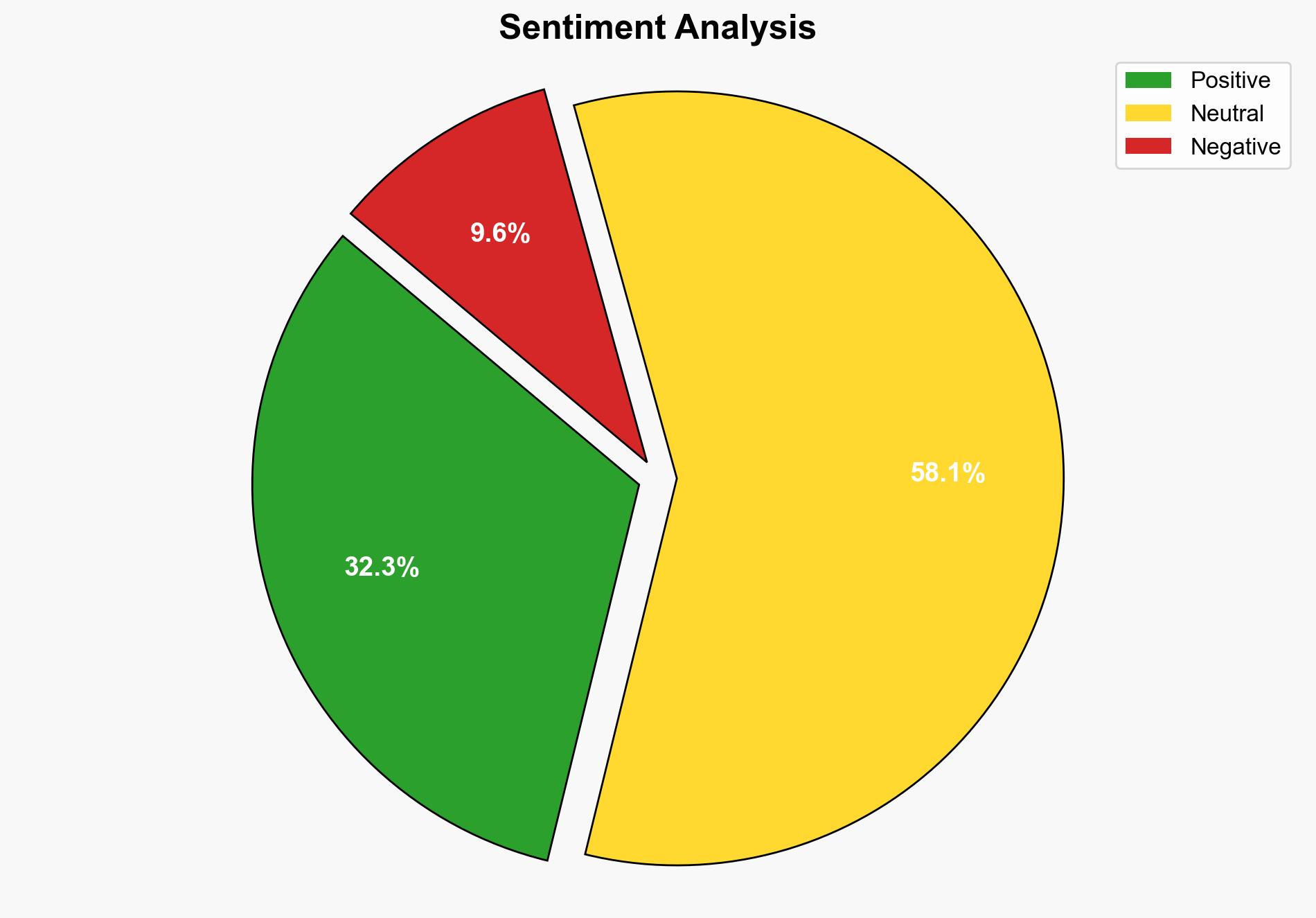
The most supported hypothesis is that increasing payouts in bug bounty programs attracts more skilled researchers and higher-quality submissions, but it also risks overwhelming teams with low-value reports. Confidence level: Moderate. Recommended action: Implement a tiered reward structure focusing on high-impact vulnerabilities and improve triage processes to handle increased submissions effectively.
2. Competing Hypotheses
Hypothesis 1: Increasing payouts in bug bounty programs leads to a higher volume of submissions, including more high-impact vulnerabilities, thereby improving overall program effectiveness.
Hypothesis 2: While increasing payouts attracts more submissions, it primarily results in a flood of low-value reports, straining resources and potentially obscuring critical vulnerabilities.
3. Key Assumptions and Red Flags
Assumptions:
– Higher payouts inherently attract more skilled researchers.
– The volume of submissions correlates with the quality of findings.
– Internal teams can manage increased submission volumes effectively.
Red Flags:
– Lack of data on the long-term retention of skilled researchers.
– Potential bias in assuming that all increased submissions are beneficial.
– Insufficient consideration of the impact on internal resource allocation.
4. Implications and Strategic Risks
– Economic: Increased payouts may lead to unsustainable costs if not managed properly.
– Cyber: A flood of low-value reports could obscure critical vulnerabilities, increasing the risk of breaches.
– Psychological: Researcher trust may erode if submissions are not triaged and rewarded promptly.
– Competitive: Other programs may increase payouts, creating a competitive market for skilled researchers.
5. Recommendations and Outlook
- Implement a tiered reward structure focusing on high-impact vulnerabilities to ensure resources are used effectively.
- Enhance triage processes to manage increased submission volumes and maintain researcher trust.
- Scenario Projections:
- Best Case: Improved triage and reward structures lead to a sustainable increase in high-quality submissions.
- Worst Case: Increased costs with minimal improvement in vulnerability detection, leading to resource strain.
- Most Likely: A moderate increase in high-quality findings with initial strain on resources, requiring process adjustments.
6. Key Individuals and Entities
– Ottilia Westerlund
– Christian Toon
– Jukka Seppänen
7. Thematic Tags
cybersecurity, economic impact, resource management, vulnerability management