Redis patches critical RediShell RCE vulnerability update ASAP CVE-2025-49844 – Help Net Security
Published on: 2025-10-07
Intelligence Report: Redis patches critical RediShell RCE vulnerability update ASAP CVE-2025-49844 – Help Net Security
1. BLUF (Bottom Line Up Front)
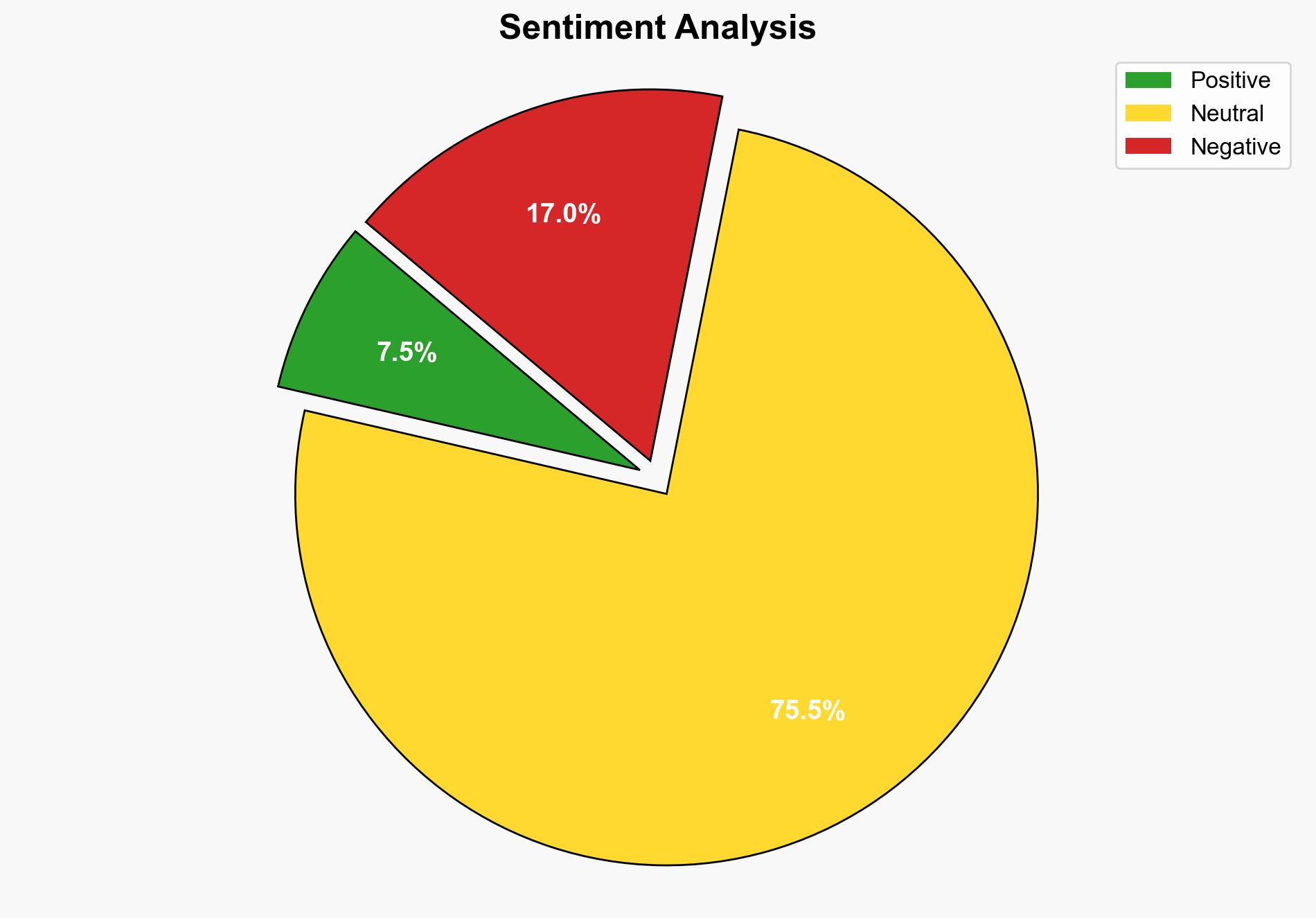
The most supported hypothesis is that the Redis vulnerability (CVE-2025-49844) poses an immediate and severe risk to systems using Redis, particularly those with default configurations and exposed to the internet. The strategic recommendation is to urgently apply the patch, enable authentication, and restrict Lua scripting. Confidence level: High.
2. Competing Hypotheses
1. **Hypothesis A**: The Redis vulnerability will lead to widespread exploitation, resulting in significant data breaches and system compromises, particularly in cloud environments with default settings.
2. **Hypothesis B**: The vulnerability will be contained quickly due to rapid patch deployment and heightened awareness, limiting the potential for large-scale exploitation.
Using ACH 2.0, Hypothesis A is better supported due to the high number of Redis instances with default configurations and the critical nature of the vulnerability allowing remote code execution.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that many Redis instances are exposed to the internet with default settings. It is also assumed that attackers will rapidly exploit the vulnerability.
– **Red Flags**: Lack of detailed technical information from the researchers may delay defensive measures. The assumption that all administrators will promptly patch their systems could be overly optimistic.
4. Implications and Strategic Risks
The vulnerability could lead to cascading threats, including data theft, unauthorized access to cloud services, and potential deployment of cryptominers. The economic impact could be significant for organizations relying on Redis for critical operations. Geopolitically, this could increase tensions if state-sponsored actors exploit the vulnerability.
5. Recommendations and Outlook
- **Immediate Actions**: Apply the Redis patch and enable authentication on all instances. Disable Lua scripting where possible.
- **Medium-term Actions**: Conduct a comprehensive security audit of systems using Redis. Implement network-level access controls.
- **Scenario Projections**:
– **Best Case**: Rapid patch adoption leads to minimal exploitation.
– **Worst Case**: Widespread exploitation results in significant data breaches and financial losses.
– **Most Likely**: Moderate exploitation occurs, primarily affecting systems with default configurations.
6. Key Individuals and Entities
– Redis Company
– Wiz Researchers
– German Federal Office for Information Security (BSI)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus