Wake Up Do Not Lie There Thinking – Stevenpressfield.com
Published on: 2025-10-08
Intelligence Report: Wake Up Do Not Lie There Thinking – Stevenpressfield.com
1. BLUF (Bottom Line Up Front)
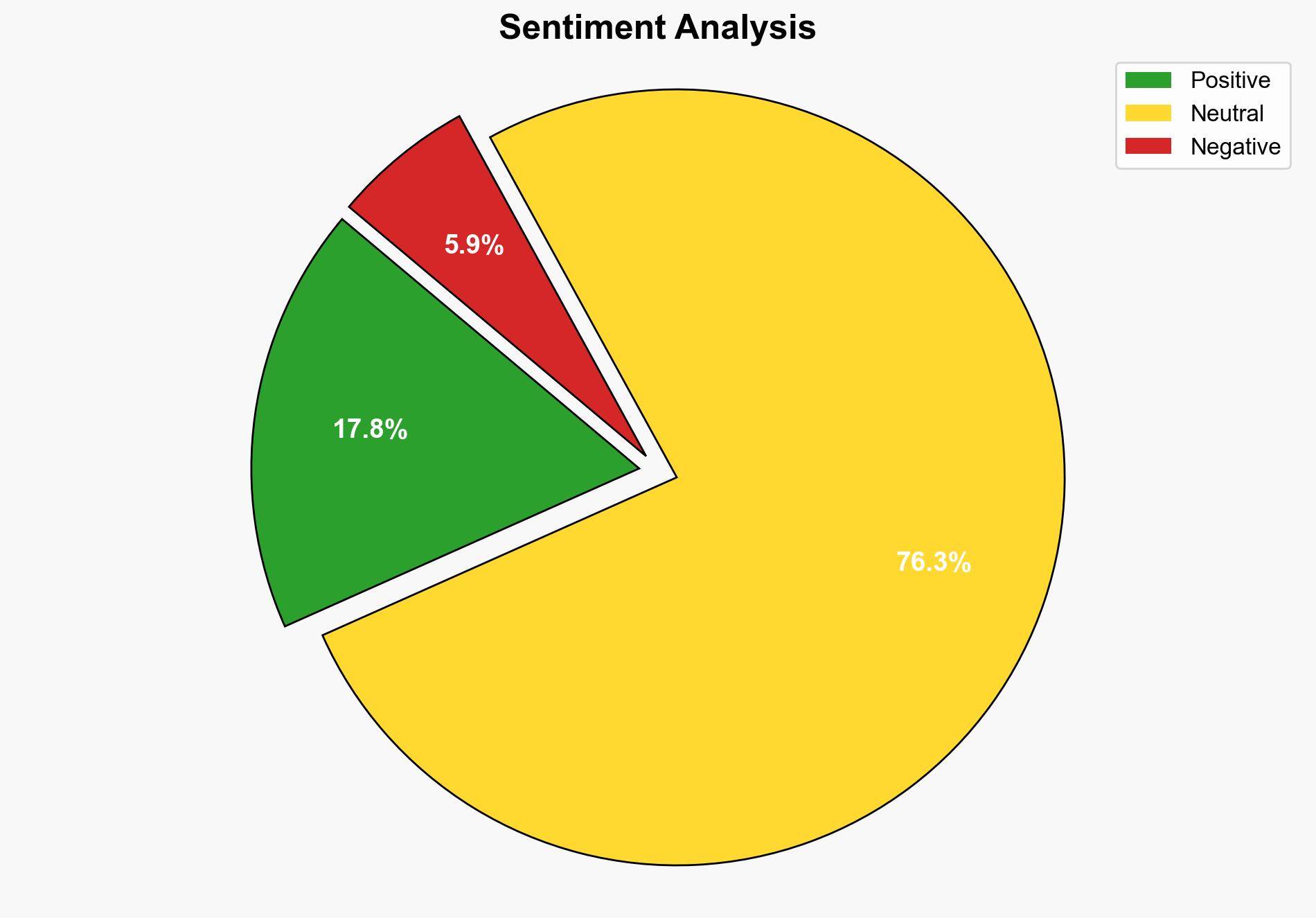
The primary hypothesis suggests that the text is a motivational piece by Steven Pressfield, emphasizing overcoming resistance in creative work. An alternative hypothesis is that the text has been corrupted or manipulated, potentially indicating a cybersecurity breach or data integrity issue. The first hypothesis is better supported by the coherent sections of the text. Confidence level: Moderate. Recommended action: Verify the integrity of the source and monitor for potential cybersecurity threats.
2. Competing Hypotheses
1. **Motivational Content Hypothesis**: The text is intended as a motivational narrative by Steven Pressfield, focusing on overcoming internal resistance to achieve creative success.
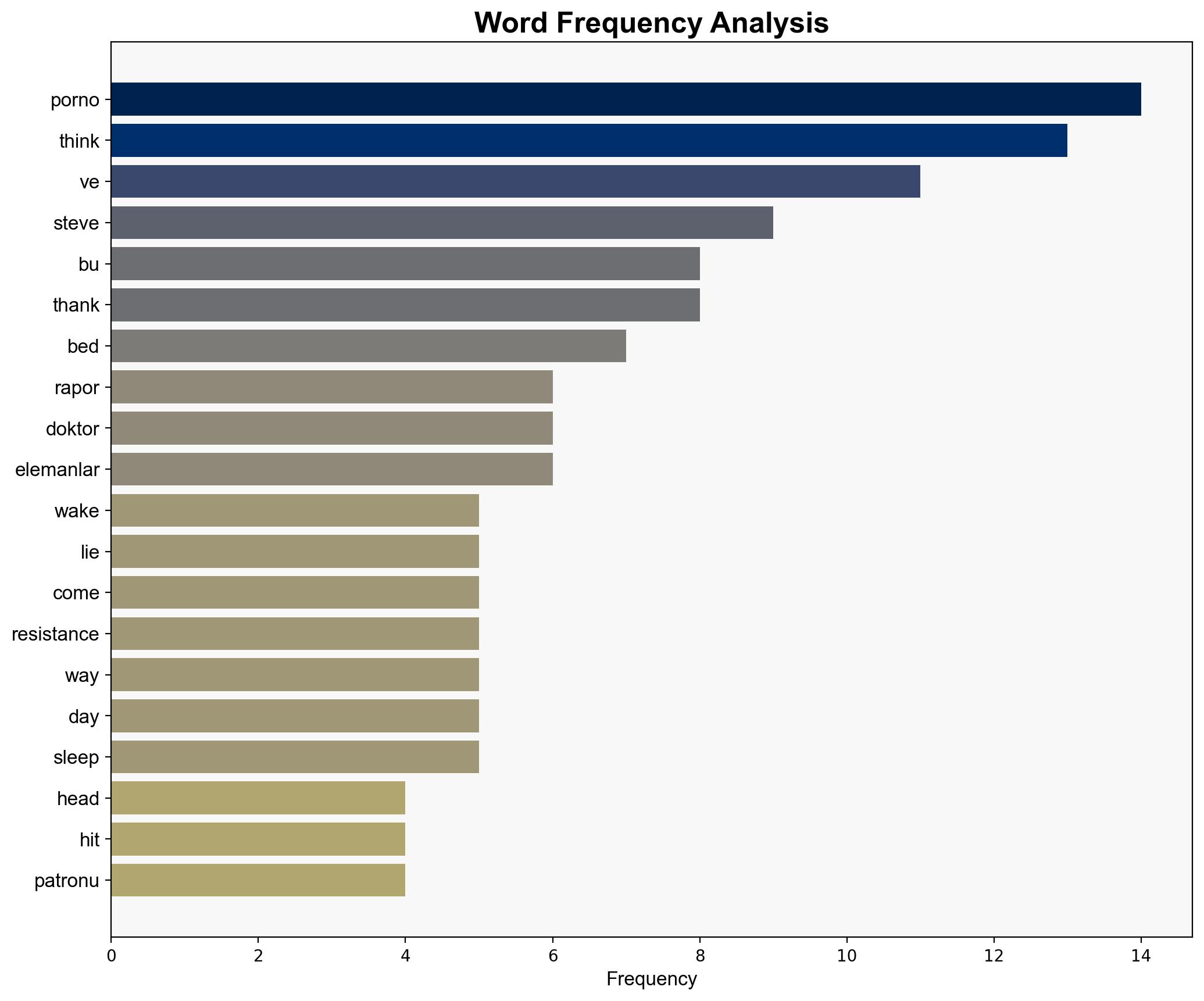
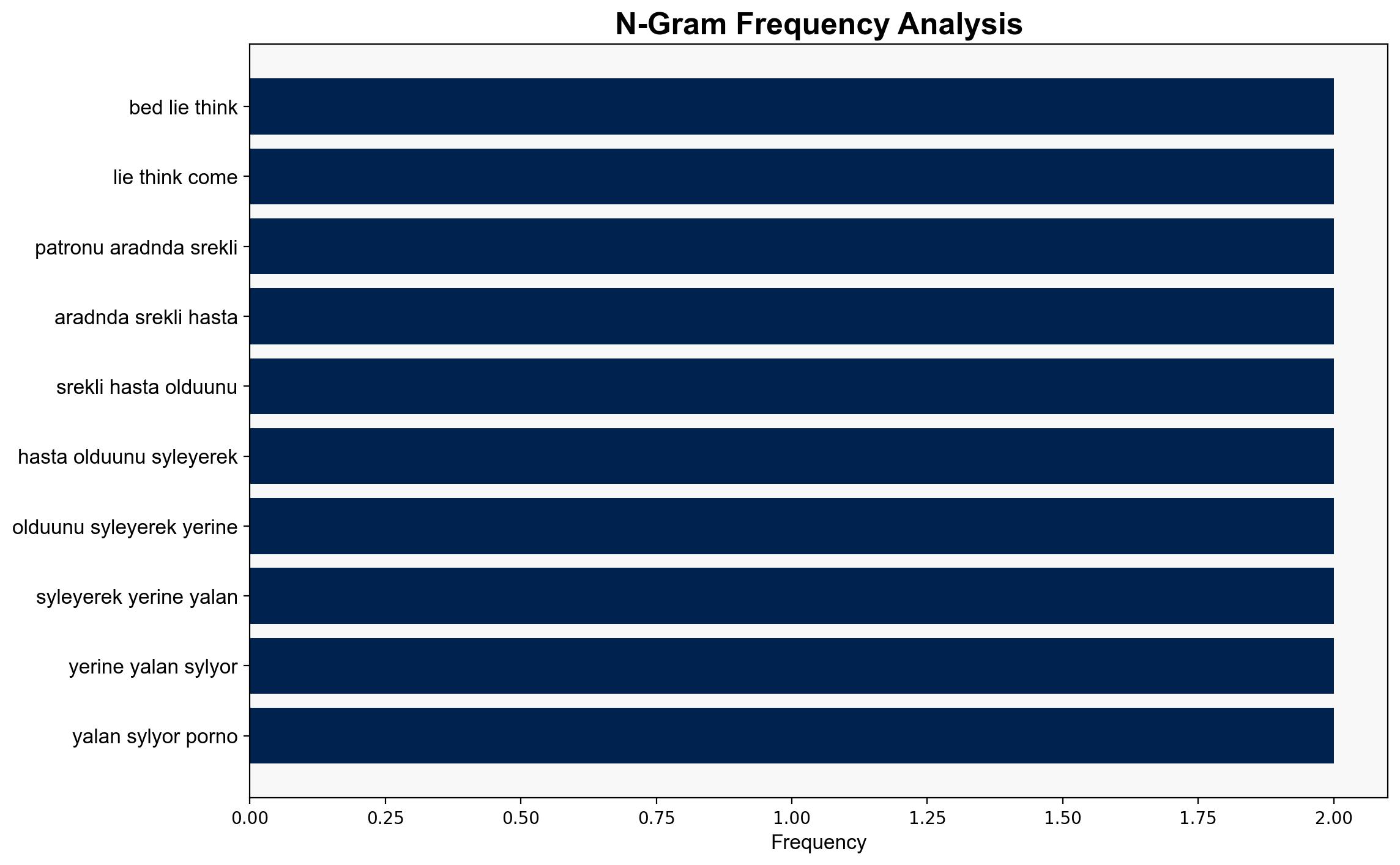
2. **Data Corruption Hypothesis**: The text has been corrupted or manipulated, possibly due to a cybersecurity breach, leading to the inclusion of irrelevant and inappropriate content.
3. Key Assumptions and Red Flags
– **Motivational Content Hypothesis Assumptions**: Assumes the coherent parts of the text are representative of Pressfield’s typical style and content.
– **Data Corruption Hypothesis Assumptions**: Assumes the presence of inappropriate content is not intentional and indicates data manipulation.
– **Red Flags**: The presence of irrelevant and inappropriate content is a significant red flag, suggesting potential data integrity issues.
4. Implications and Strategic Risks
– **Implications**: If the text is motivational, it aligns with Pressfield’s known work, with minimal strategic risk. If corrupted, it suggests vulnerabilities in data security, potentially impacting the credibility of the source.
– **Strategic Risks**: Data integrity issues could lead to misinformation and damage to reputational trust. Cybersecurity vulnerabilities may expose sensitive information.
5. Recommendations and Outlook
- Conduct a thorough review of the website’s cybersecurity measures to prevent future data breaches.
- Verify the integrity of the text with the original author or publisher to confirm authenticity.
- Scenario Projections:
- Best Case: The text is verified as authentic, and cybersecurity measures are enhanced.
- Worst Case: Data breach leads to widespread misinformation and reputational damage.
- Most Likely: The text is partially authentic, with some data corruption, prompting a review of security protocols.
6. Key Individuals and Entities
– Steven Pressfield
7. Thematic Tags
national security threats, cybersecurity, data integrity, motivational content