Chinese Hackers Weaponize Open-Source Nezha Tool in New Attack Wave – Internet
Published on: 2025-10-08
Intelligence Report: Chinese Hackers Weaponize Open-Source Nezha Tool in New Attack Wave – Internet
1. BLUF (Bottom Line Up Front)
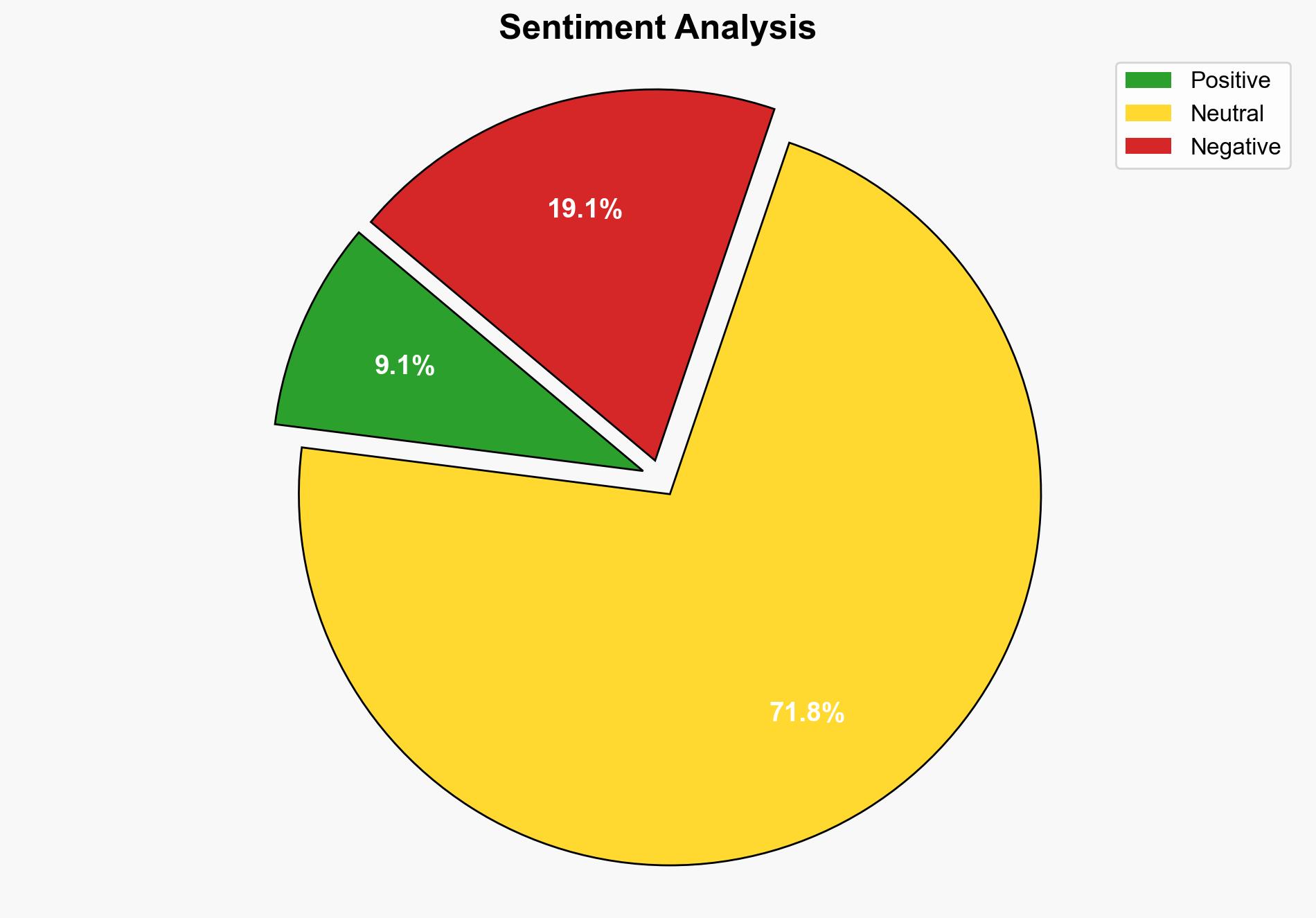
The most supported hypothesis is that Chinese threat actors are leveraging the Nezha tool to conduct cyber-espionage operations primarily targeting East Asian countries, with a moderate confidence level. The strategic recommendation is to enhance monitoring of open-source tool usage and bolster regional cybersecurity collaboration to mitigate these threats.
2. Competing Hypotheses
Hypothesis 1: Chinese threat actors are using the Nezha tool as part of a coordinated cyber-espionage campaign targeting East Asian countries to gather intelligence and disrupt regional stability.
Hypothesis 2: The use of the Nezha tool is opportunistic, with Chinese hackers exploiting publicly available tools to conduct financially motivated cyber-attacks globally, with no specific geopolitical agenda.
Using Analysis of Competing Hypotheses (ACH), Hypothesis 1 is better supported due to the concentration of attacks in Taiwan, Japan, South Korea, and Hong Kong, aligning with known geopolitical tensions. Hypothesis 2 lacks strong evidence of financial motivation or a broader global impact.
3. Key Assumptions and Red Flags
– Assumption: The concentration of attacks in East Asia indicates a geopolitical motive.
– Red Flag: The presence of victims in diverse countries could suggest a broader operational scope.
– Potential Bias: Attribution to Chinese actors may be influenced by historical patterns rather than concrete evidence.
– Missing Data: Lack of detailed information on the specific data targeted or stolen.
4. Implications and Strategic Risks
The pattern of attacks suggests a potential escalation in cyber-espionage activities, which could destabilize regional relations and impact economic activities. The use of open-source tools like Nezha lowers the barrier for entry, increasing the risk of similar attacks by other actors. This could lead to a proliferation of cyber threats globally, challenging existing cybersecurity defenses.
5. Recommendations and Outlook
- Enhance monitoring and detection capabilities for open-source tool misuse.
- Strengthen regional cybersecurity collaboration and information sharing.
- Scenario Projections:
- Best Case: Improved defenses lead to a significant reduction in successful attacks.
- Worst Case: Escalation of cyber-attacks disrupts regional stability and economic activities.
- Most Likely: Continued low-level cyber-espionage with periodic spikes in activity.
6. Key Individuals and Entities
Jai Minton, James Northey, Alden Schmidt (Researchers from Huntress)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus