What to do when you click on a suspicious link – Talosintelligence.com
Published on: 2025-10-08
Intelligence Report: What to do when you click on a suspicious link – Talosintelligence.com
1. BLUF (Bottom Line Up Front)
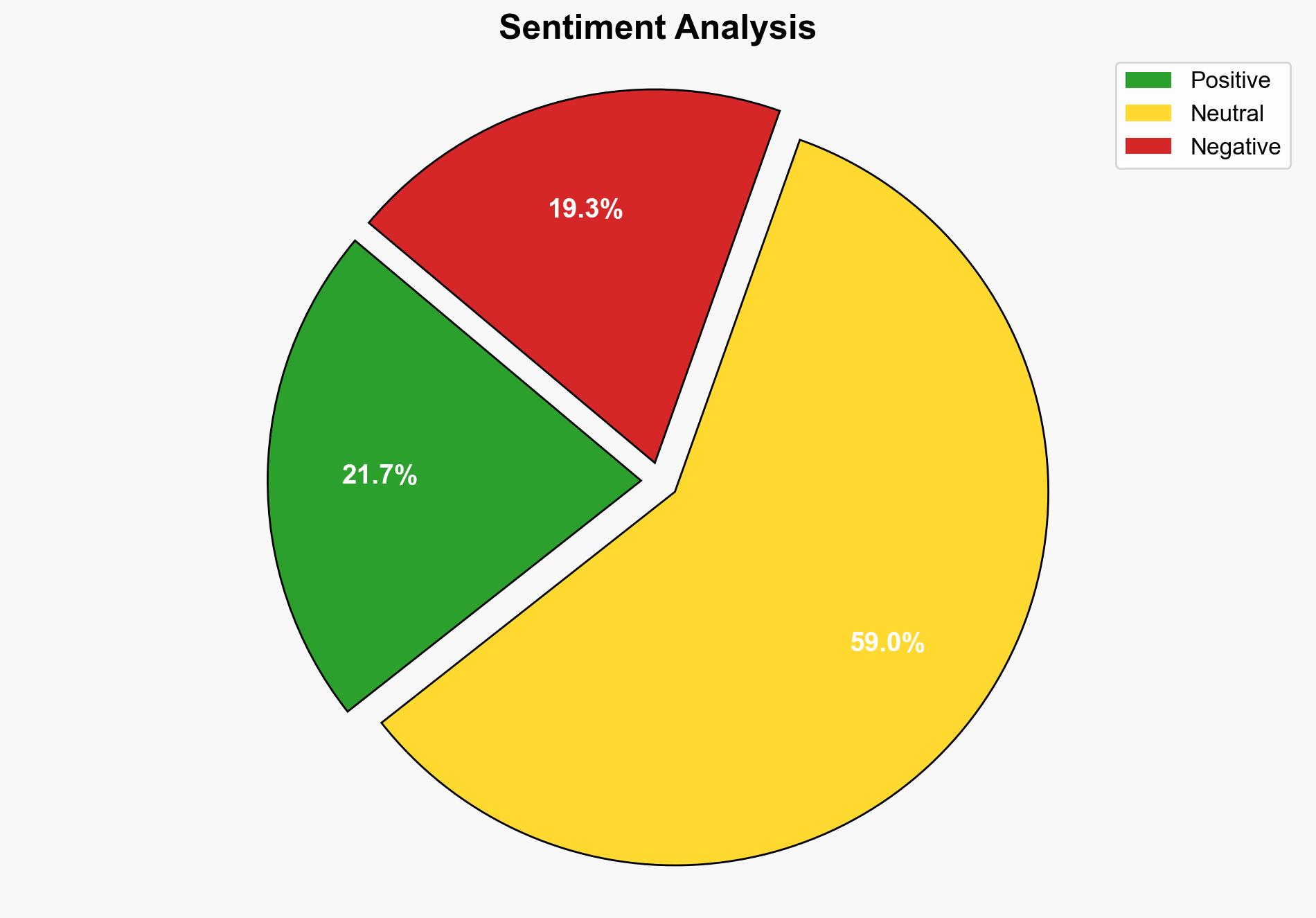
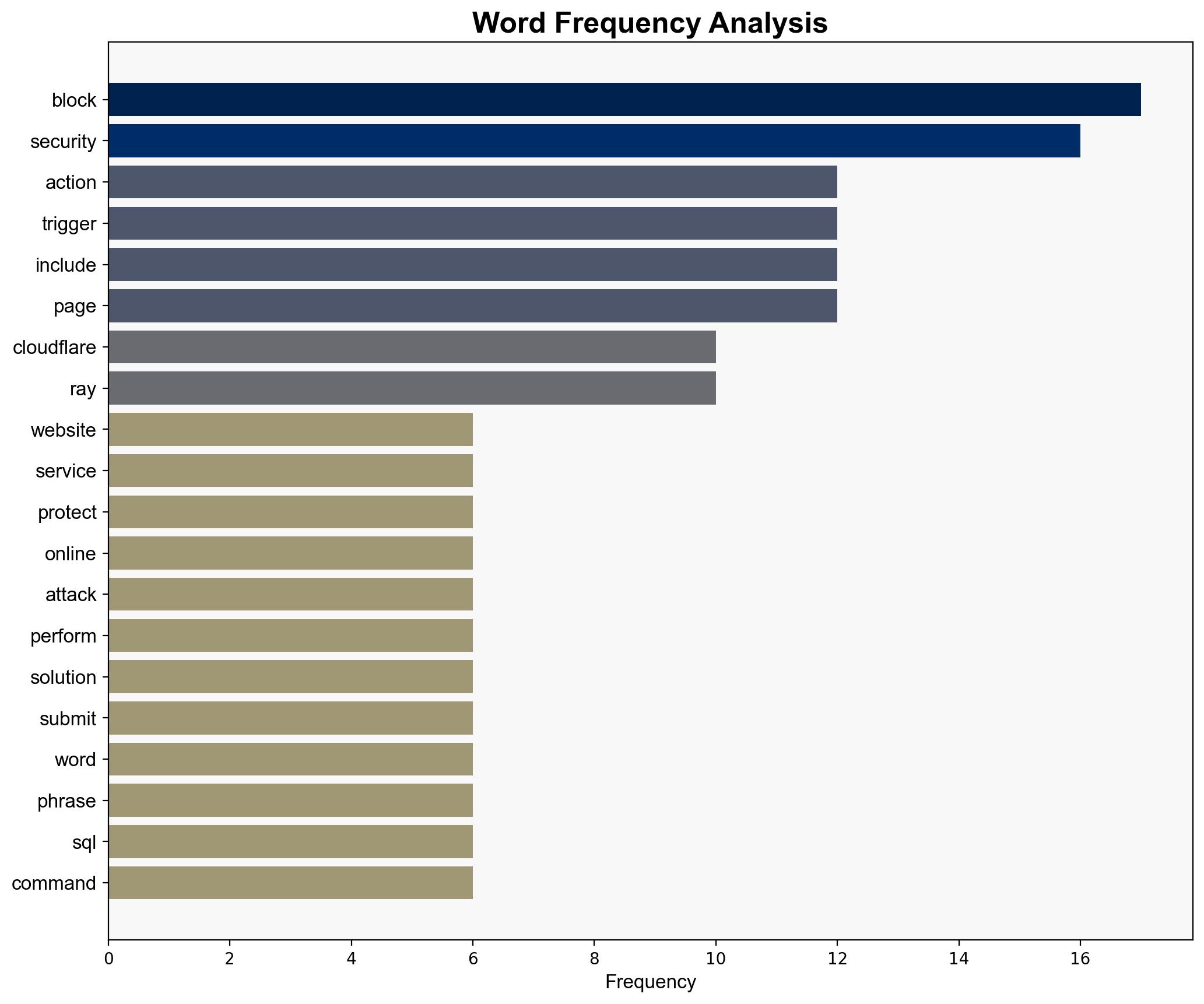
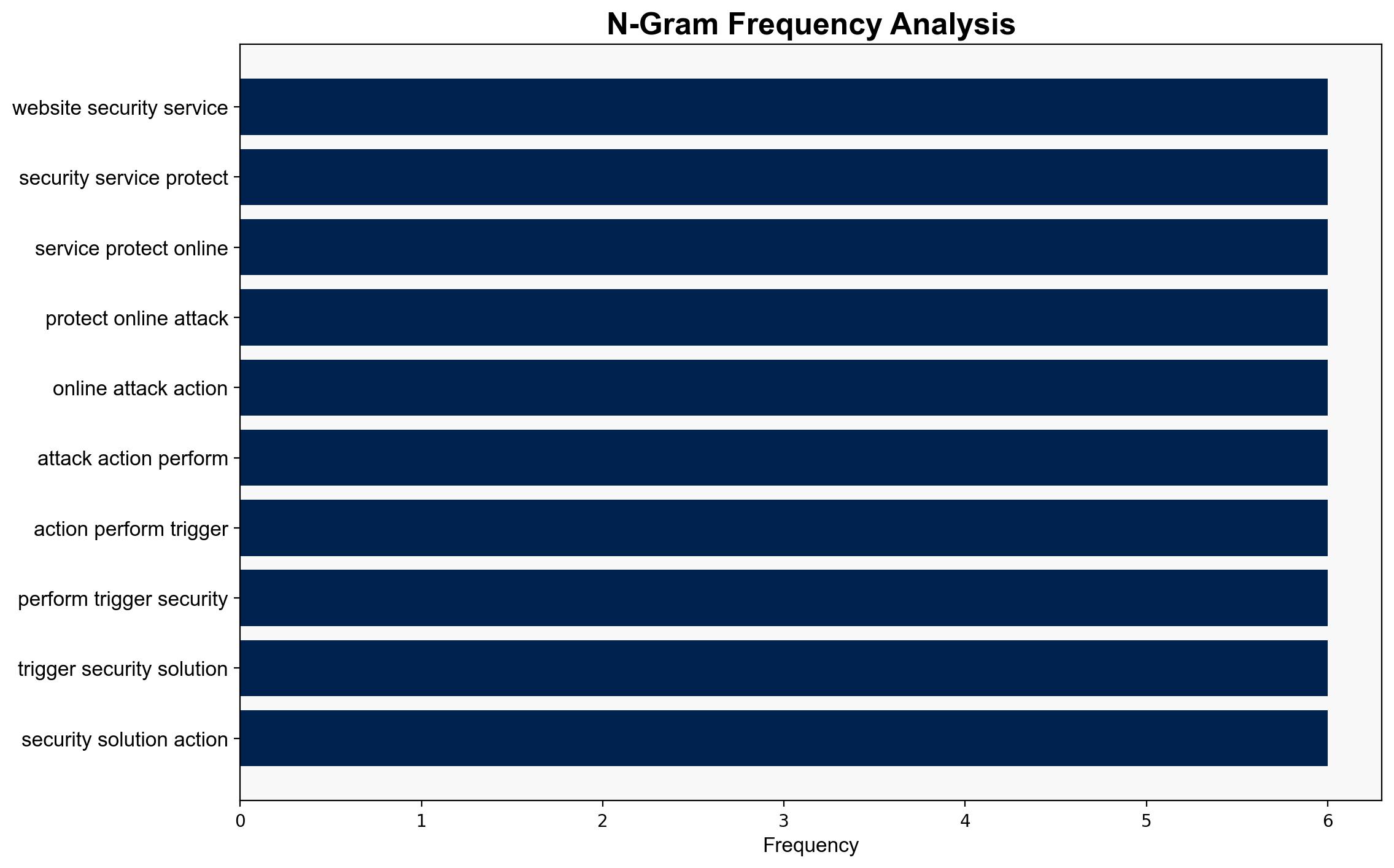
The most supported hypothesis is that the blocked access to Talosintelligence.com is a result of automated security protocols triggered by suspicious activity, such as potential SQL injection attempts. This hypothesis is supported by the repetitive mention of security services and SQL commands in the source text. The confidence level is moderate due to the lack of explicit confirmation from the site owner. Recommended action includes verifying the legitimacy of the block with the site owner and ensuring that security measures are in place to prevent unauthorized access attempts.
2. Competing Hypotheses
1. **Hypothesis A**: The block is a legitimate security measure triggered by automated systems detecting potential malicious activity, such as SQL injection attempts.
2. **Hypothesis B**: The block is a false positive, resulting from overly sensitive security settings or misconfigured security protocols on the website.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Hypothesis A assumes that the security systems in place are functioning correctly and are accurately identifying threats.
– Hypothesis B assumes that there may be a misconfiguration or overly aggressive security settings leading to false positives.
– **Red Flags**:
– Repeated phrases and lack of specific details about the nature of the threat raise questions about the accuracy and specificity of the security protocols.
– Absence of direct communication from the site owner confirming the nature of the block.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: If Hypothesis A is correct, there is a risk of ongoing malicious attempts that could compromise user data or site integrity if not properly mitigated.
– **Reputational Risks**: If Hypothesis B is correct, frequent false positives could damage the credibility of the site’s security measures and frustrate legitimate users.
– **Escalation Scenarios**: Persistent security alerts without resolution could lead to increased scrutiny and potential regulatory attention.
5. Recommendations and Outlook
- **Verify Legitimacy**: Contact the site owner to confirm the nature of the block and ensure it is not a false positive.
- **Enhance Security Protocols**: Review and adjust security settings to balance between protection and accessibility.
- **Scenario Projections**:
- **Best Case**: The block is a false positive, quickly resolved with minimal disruption.
- **Worst Case**: The block indicates a sophisticated and ongoing cyber attack requiring extensive mitigation efforts.
- **Most Likely**: The block is a standard security measure, resolved through verification and minor adjustments.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The primary entity involved is Cloudflare, responsible for the security protocols mentioned.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus