Threat actors steal firewall configs impacting all SonicWall Cloud Backup users – Securityaffairs.com
Published on: 2025-10-09
Intelligence Report: Threat actors steal firewall configs impacting all SonicWall Cloud Backup users – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
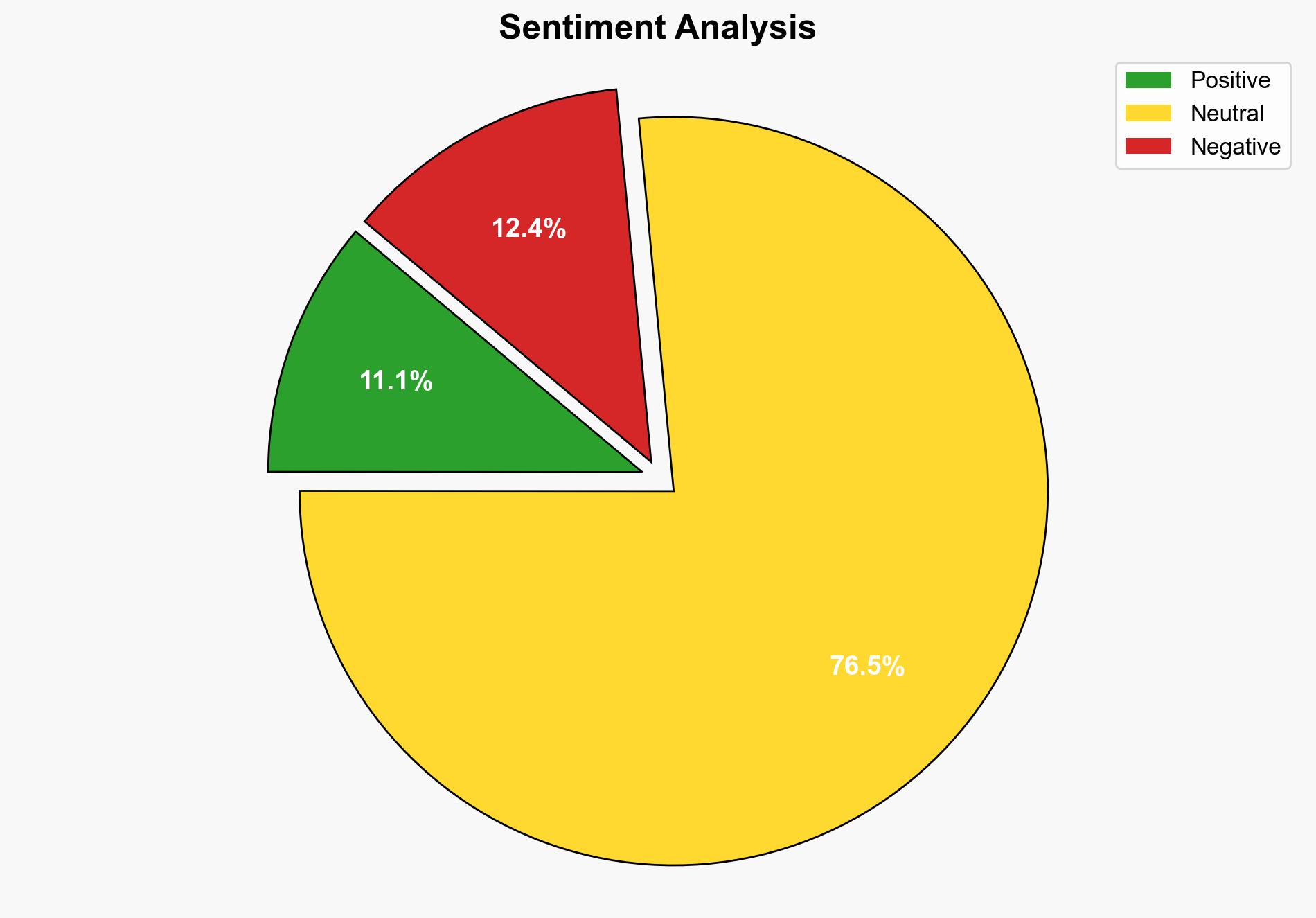
The breach of SonicWall’s Cloud Backup service, involving the theft of firewall configuration files, poses a significant cybersecurity risk to affected users. The most supported hypothesis is that the breach was conducted by a sophisticated threat actor aiming to exploit vulnerabilities in SonicWall’s infrastructure for targeted attacks. Confidence level: Moderate. Recommended action includes immediate credential resets, enhanced monitoring, and collaboration with cybersecurity experts to mitigate potential exploitation.
2. Competing Hypotheses
Hypothesis 1: A sophisticated cybercriminal group targeted SonicWall to exploit vulnerabilities in their cloud infrastructure, aiming to access sensitive data for financial gain or espionage.
Hypothesis 2: The breach was an opportunistic attack by less organized threat actors who stumbled upon a vulnerability, with no specific target or strategic intent beyond immediate data theft.
3. Key Assumptions and Red Flags
Assumptions:
– Hypothesis 1 assumes a high level of planning and capability by the threat actors.
– Hypothesis 2 assumes the breach was not premeditated but rather a chance exploitation.
Red Flags:
– Lack of detailed information on how the breach was executed.
– No clear attribution to a known threat group, raising questions about the attack’s origin.
– Potential underreporting of the breach’s impact by SonicWall.
4. Implications and Strategic Risks
The breach could lead to targeted attacks on affected users, leveraging stolen configuration data to bypass security measures. This incident may also damage SonicWall’s reputation, affecting customer trust and market position. Geopolitically, if linked to state-sponsored actors, it could escalate tensions and lead to retaliatory cyber operations.
5. Recommendations and Outlook
- Immediate actions: Reset credentials, apply patches, and conduct a thorough security audit.
- Medium-term: Enhance monitoring and threat detection capabilities, and engage with cybersecurity firms for advanced threat intelligence.
- Scenario Projections:
- Best Case: Quick containment and mitigation prevent further exploitation, with minimal impact on users.
- Worst Case: Exploited data leads to widespread attacks, causing significant financial and reputational damage.
- Most Likely: Some targeted attacks occur, but effective mitigation limits broader impact.
6. Key Individuals and Entities
– SonicWall
– Mandiant (collaborating on investigation)
7. Thematic Tags
national security threats, cybersecurity, data breach, cybercrime, threat intelligence