Disable Windows Defender 10 – Majorgeeks.com
Published on: 2025-10-09
Intelligence Report: Disable Windows Defender 10 – Majorgeeks.com
1. BLUF (Bottom Line Up Front)
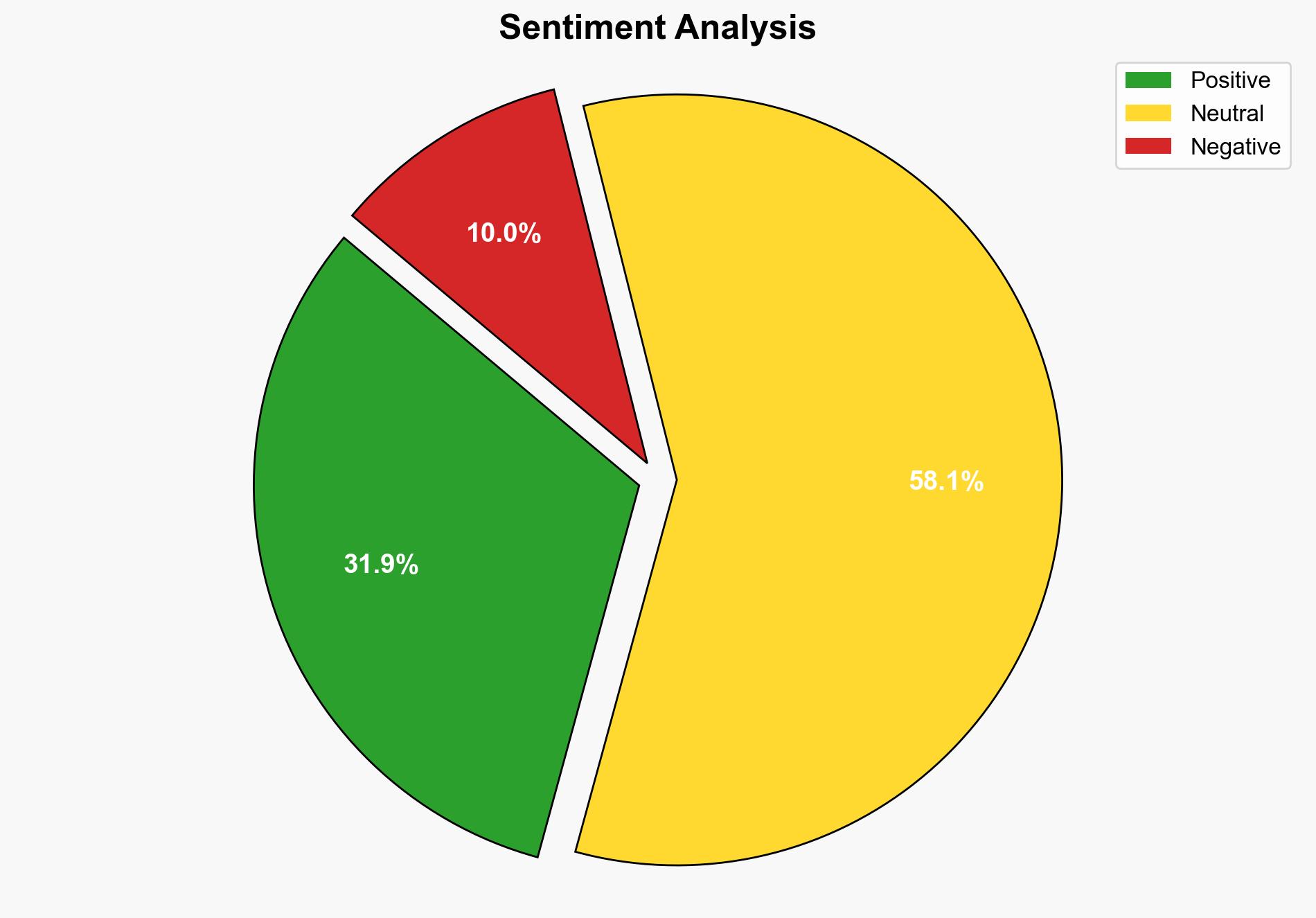
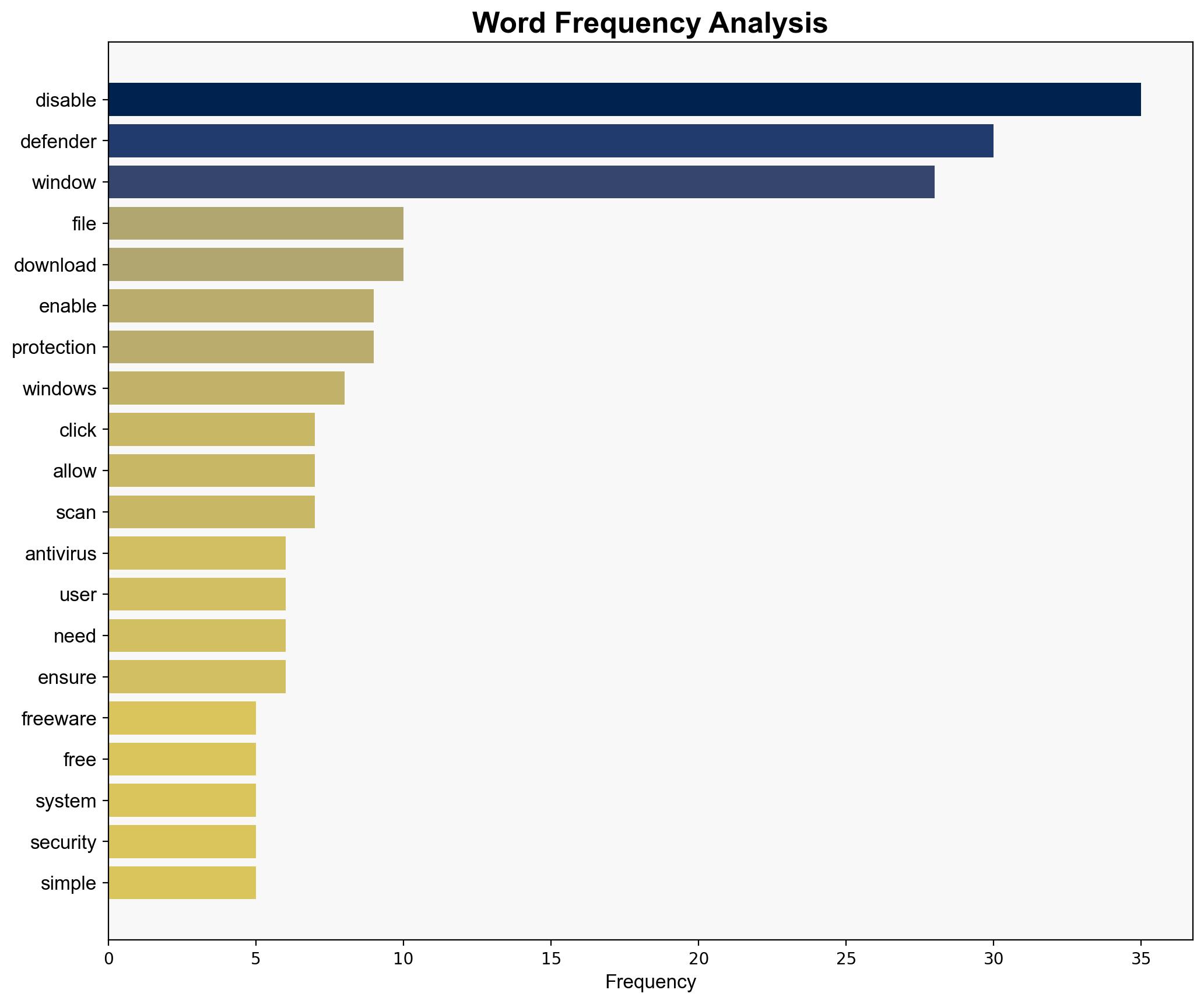
The analysis suggests that the tool to disable Windows Defender is primarily designed for users seeking greater control over their security settings, potentially to improve system performance or avoid false positives. However, there is a moderate risk that such tools could be exploited for malicious purposes. The most supported hypothesis is that the tool is benign but could be misused. It is recommended to monitor the distribution and use of such tools to prevent exploitation. Confidence level: Moderate.
2. Competing Hypotheses
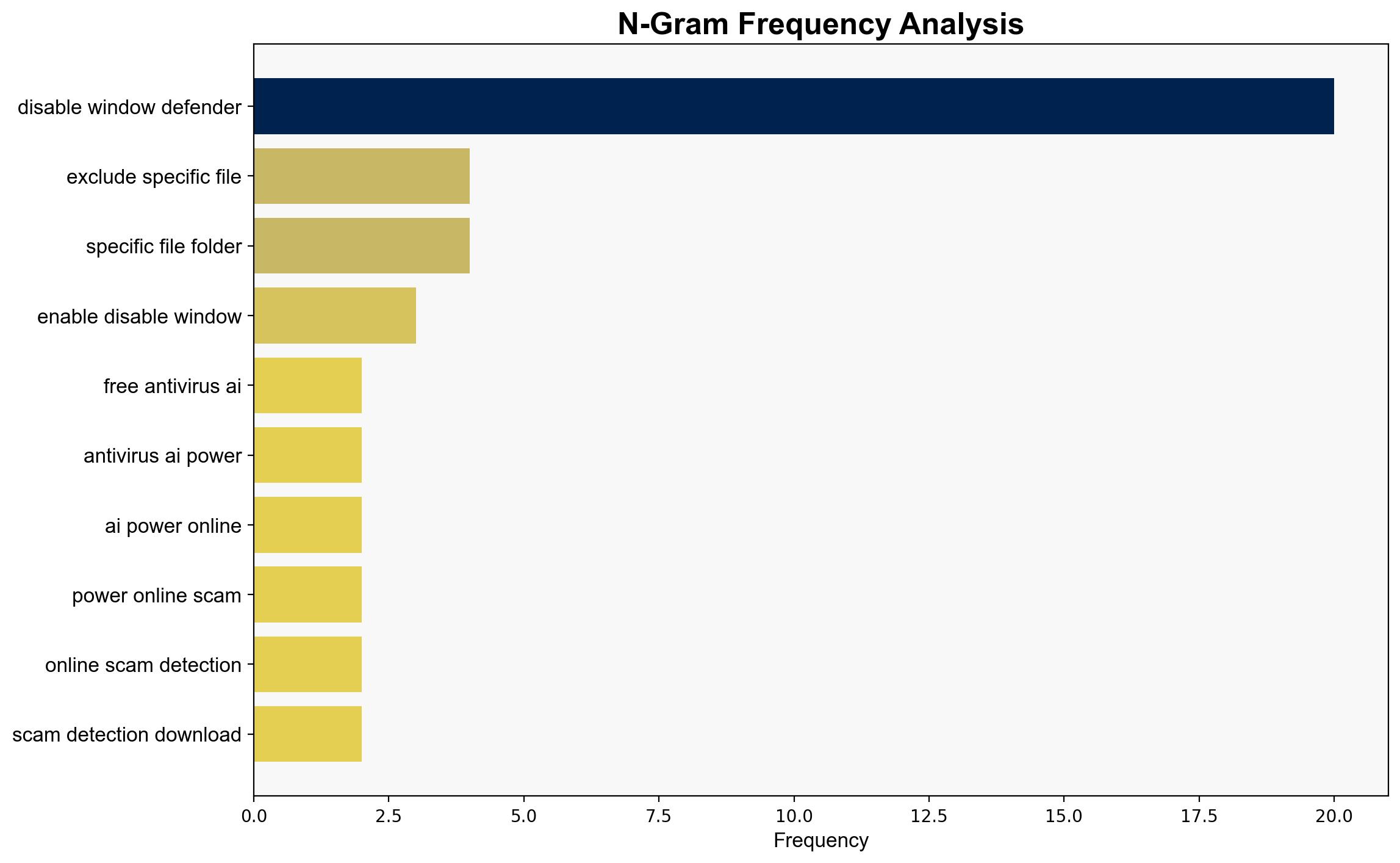
1. **Hypothesis A**: The tool is a legitimate utility aimed at advanced users who need to manage their security settings more flexibly, primarily to avoid false positives and improve performance.
2. **Hypothesis B**: The tool is potentially a vector for malicious actors to disable security features on a target system, facilitating unauthorized access or malware deployment.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported by the context and language of the source, which emphasizes user control and flexibility. However, Hypothesis B cannot be entirely dismissed due to the inherent risks of disabling security features.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that users are aware of the risks associated with disabling security features and that the tool is used responsibly.
– **Red Flags**: The ease of disabling critical security features without a system restart could be exploited by malicious entities. The lack of detailed information on security measures within the tool itself is concerning.
– **Blind Spots**: The source does not provide information on the developer’s reputation or any security audits conducted on the tool.
4. Implications and Strategic Risks
The widespread use of such tools could lead to increased vulnerability to cyber threats if users disable essential security features without understanding the risks. This could result in economic losses from data breaches or malware attacks. There is also a psychological risk in undermining trust in built-in security solutions.
5. Recommendations and Outlook
- **Mitigation**: Encourage users to understand the risks of disabling security features and provide education on safe usage practices.
- **Monitoring**: Track the distribution and usage patterns of such tools to identify potential misuse.
- **Scenario Projections**:
– **Best Case**: Users gain improved system performance without compromising security.
– **Worst Case**: The tool is widely used by malicious actors, leading to a surge in cyber attacks.
– **Most Likely**: The tool remains niche, used by a small group of advanced users, with occasional misuse.
6. Key Individuals and Entities
– **SecurityXploded**: The author of the tool, whose intentions and reputation are crucial to understanding the tool’s legitimacy.
– **Majorgeeks.com**: The distribution platform, which plays a role in the tool’s reach and perceived legitimacy.
7. Thematic Tags
national security threats, cybersecurity, software vulnerabilities, user education