Fake VPN checker tool lets hackers bypass antivirus protections – TechRadar
Published on: 2025-10-09
Intelligence Report: Fake VPN checker tool lets hackers bypass antivirus protections – TechRadar
1. BLUF (Bottom Line Up Front)
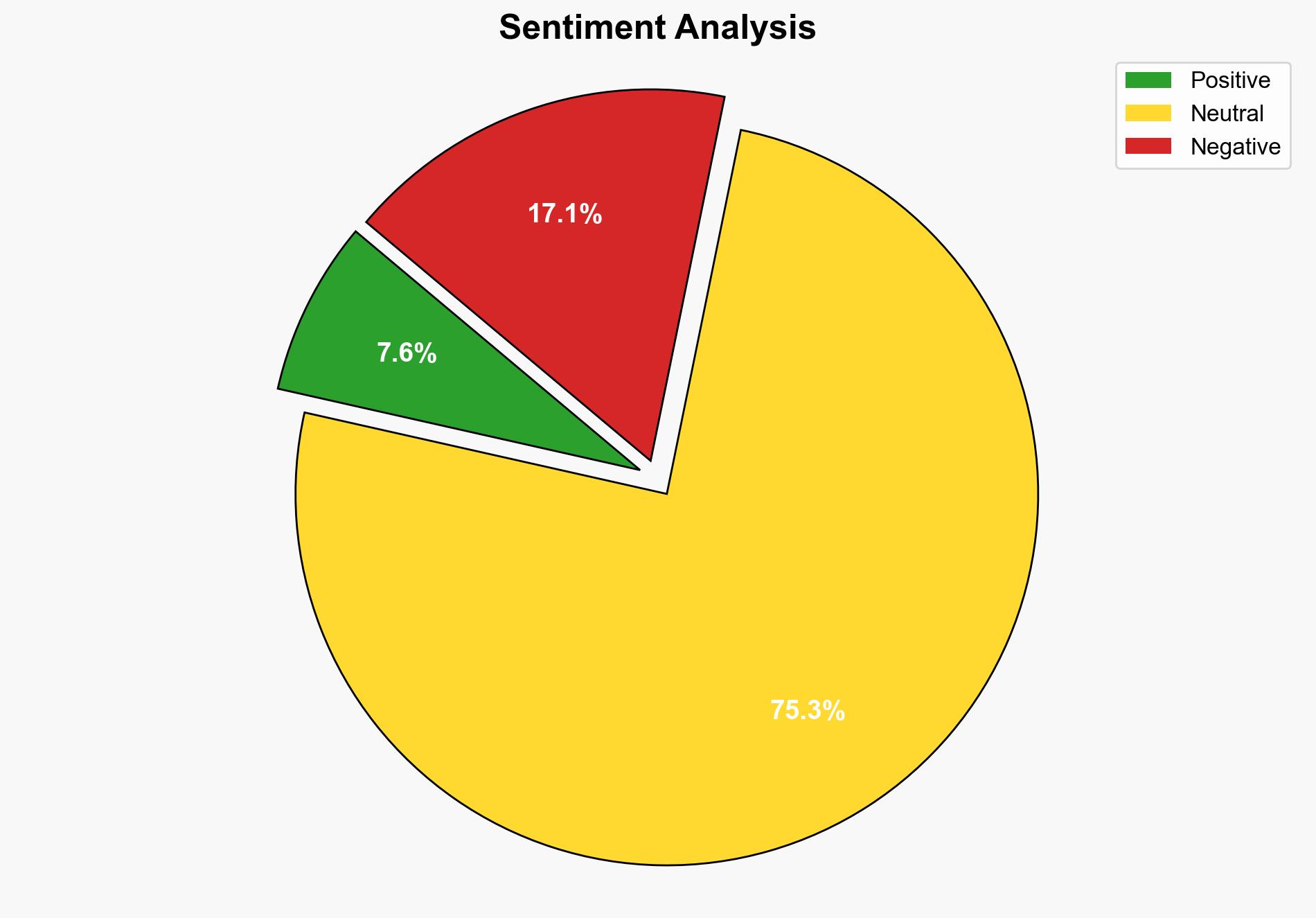
The most supported hypothesis is that the fake VPN checker tool is a sophisticated social engineering tactic combined with technical exploitation to bypass antivirus protections. Confidence level: Moderate. Recommended action: Enhance public awareness campaigns on social engineering tactics and improve detection capabilities for cache smuggling techniques.
2. Competing Hypotheses
1. **Hypothesis A**: The fake VPN checker tool is primarily a social engineering tactic that leverages user trust in Fortinet to execute malware on victim systems.
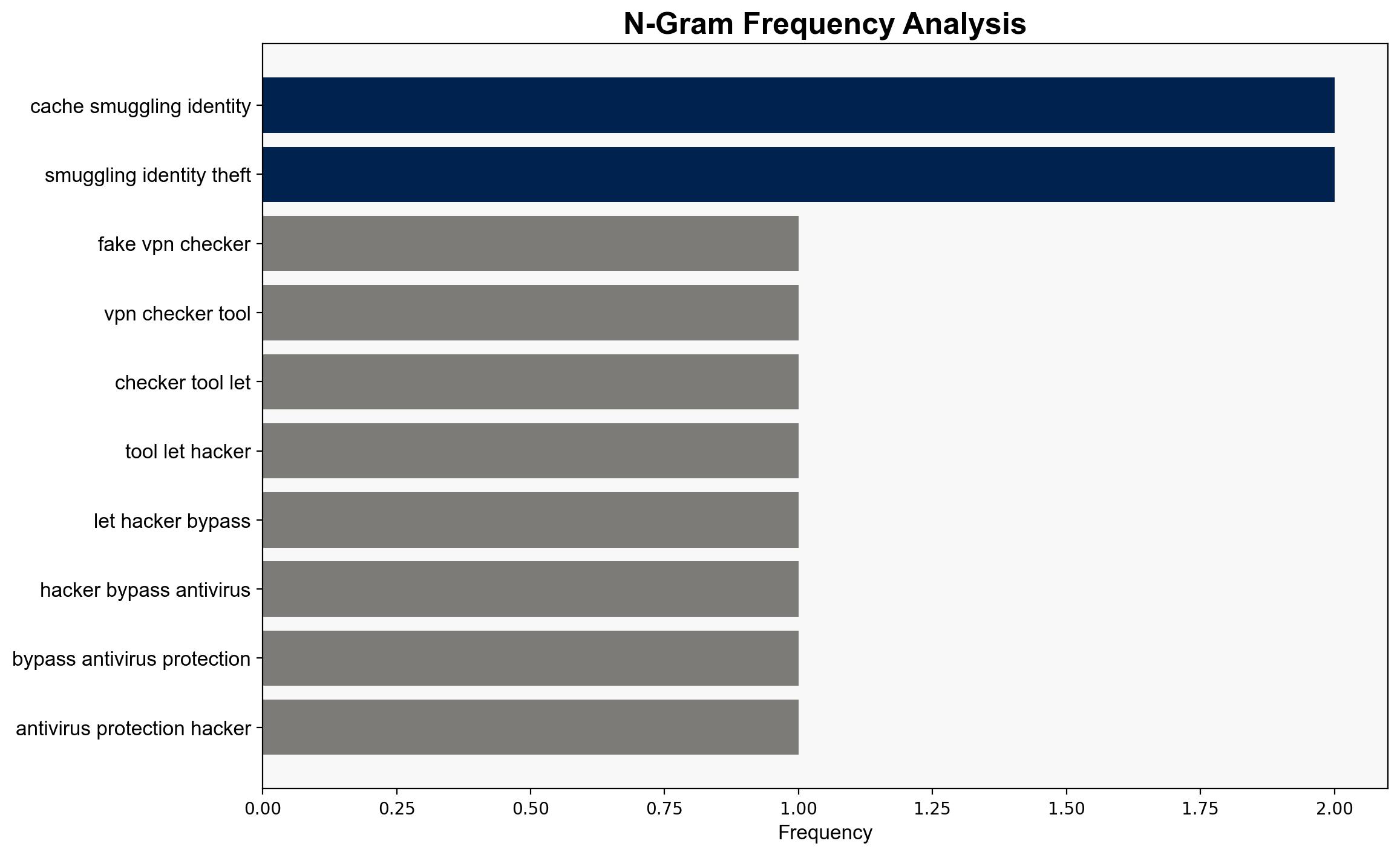
2. **Hypothesis B**: The tool represents a technical advancement in malware deployment, utilizing cache smuggling to bypass antivirus protections without significant reliance on social engineering.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the explicit mention of social engineering tactics and the use of fake dialogs mimicking Fortinet. Hypothesis B is less supported as the technical details, while advanced, still rely heavily on user interaction.
3. Key Assumptions and Red Flags
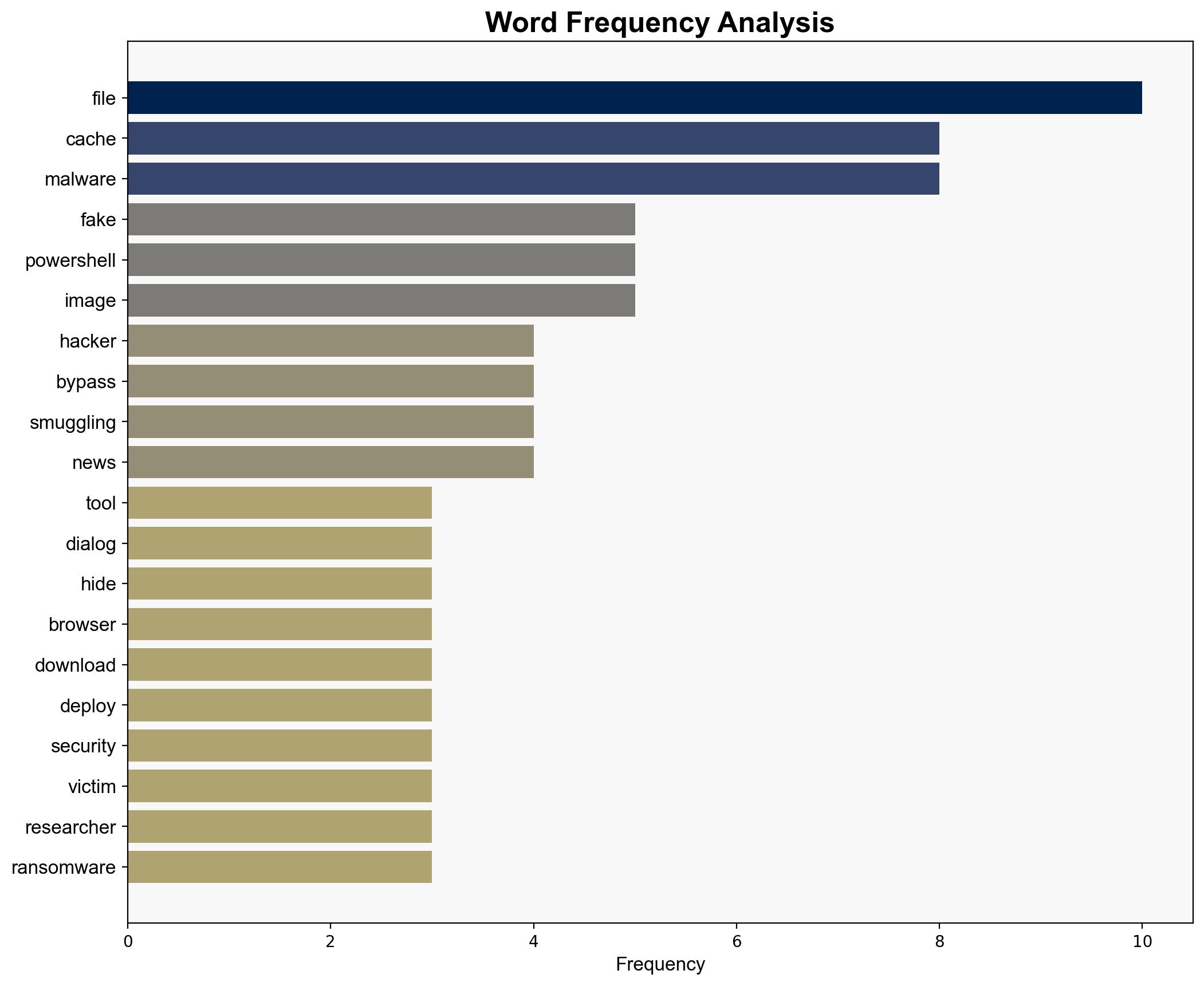
– **Assumptions**: It is assumed that users will trust the fake Fortinet dialogs and follow instructions without verification. Another assumption is that antivirus software cannot detect cache smuggling techniques.
– **Red Flags**: The lack of detailed technical analysis on how cache smuggling specifically bypasses antivirus protections is a potential blind spot. The reliance on user interaction suggests a possible overestimation of the tool’s technical sophistication.
4. Implications and Strategic Risks
This tactic could lead to increased ransomware incidents, impacting economic sectors reliant on VPNs for secure communication. The psychological impact on users’ trust in cybersecurity solutions could be significant, leading to broader adoption of alternative security measures. Geopolitically, this could strain relations between cybersecurity firms and their clients if perceived as a failure to protect against evolving threats.
5. Recommendations and Outlook
- Conduct public awareness campaigns to educate users about social engineering tactics and the importance of verifying software authenticity.
- Encourage cybersecurity firms to develop and deploy enhanced detection mechanisms for cache smuggling techniques.
- Scenario-based projections:
- Best: Rapid adaptation by cybersecurity firms leads to effective countermeasures, reducing incidents.
- Worst: Widespread adoption of the technique by various threat actors, leading to significant economic and data losses.
- Most Likely: Gradual improvement in detection and prevention, with intermittent successful attacks.
6. Key Individuals and Entities
– Sead, a freelance journalist based in Sarajevo, Bosnia and Herzegovina, reported on the issue.
– The alias “pndmcby” is noted as an independent researcher observing the tactic.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus