SonicWall confirms all of its cloud backup customers were affected by data breach – TechRadar
Published on: 2025-10-10
Intelligence Report: SonicWall confirms all of its cloud backup customers were affected by data breach – TechRadar
1. BLUF (Bottom Line Up Front)
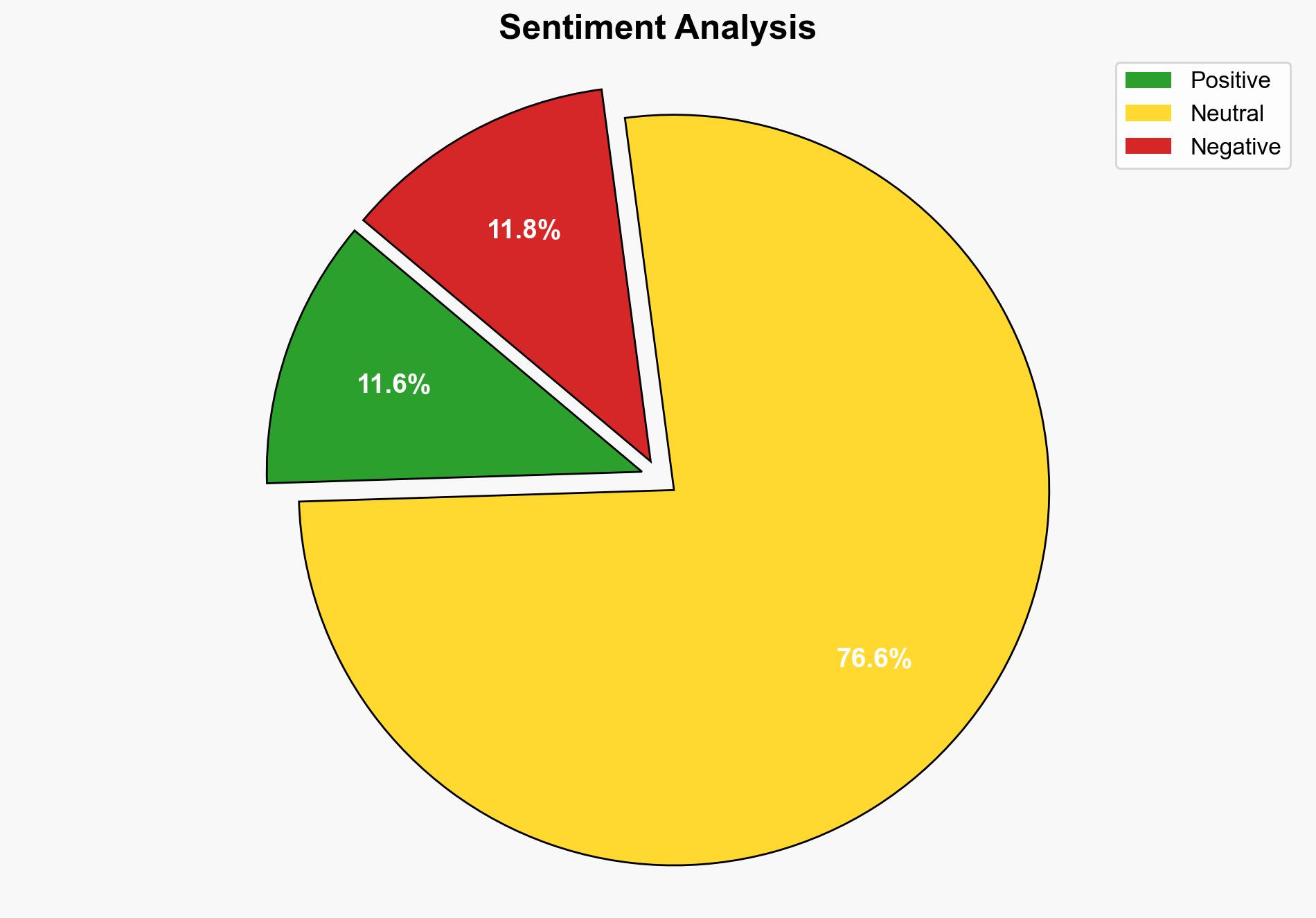
The most supported hypothesis is that the data breach at SonicWall was the result of a sophisticated cyberattack exploiting vulnerabilities in the company’s cloud backup services. Confidence level: Moderate. Recommended action: SonicWall should enhance its cybersecurity measures, including stronger encryption and user authentication protocols, and conduct a comprehensive audit of its systems to identify and rectify vulnerabilities.
2. Competing Hypotheses
1. **Hypothesis A**: The breach was a targeted attack by a sophisticated threat actor exploiting specific vulnerabilities in SonicWall’s cloud backup services.
2. **Hypothesis B**: The breach resulted from a systemic failure in SonicWall’s cybersecurity infrastructure, leading to an accidental exposure of customer data.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the nature of the breach involving brute force attacks and the need for insider knowledge to exploit firewall configurations effectively.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Hypothesis A assumes the attackers had advanced capabilities and possibly insider knowledge.
– Hypothesis B assumes a lack of adequate cybersecurity measures and oversight by SonicWall.
– **Red Flags**:
– Initial underreporting of the breach’s scale by SonicWall.
– Lack of detailed information on the threat actor’s identity and methods.
– **Blind Spots**:
– Potential for additional undisclosed vulnerabilities in SonicWall’s systems.
4. Implications and Strategic Risks
The breach exposes SonicWall to reputational damage and potential financial losses due to customer distrust. There is a risk of further exploitation if vulnerabilities remain unaddressed. The incident highlights the broader vulnerability of cloud services to cyberattacks, potentially affecting other companies and sectors reliant on similar technologies.
5. Recommendations and Outlook
- Conduct a thorough security audit and patch identified vulnerabilities.
- Implement stronger encryption and multi-factor authentication for all services.
- Enhance monitoring and incident response capabilities to detect and mitigate future breaches.
- Scenario Projections:
- Best: SonicWall successfully mitigates vulnerabilities, restoring customer trust.
- Worst: Continued breaches lead to significant financial and reputational damage.
- Most Likely: Incremental improvements in security reduce but do not eliminate risk.
6. Key Individuals and Entities
– SonicWall (Company)
– TechRadar (Source)
– Sead (Journalist)
7. Thematic Tags
national security threats, cybersecurity, data breach, cloud services