Perfect Adobe Experience Manager vulnerability is being exploited CVE-2025-54253 – Help Net Security
Published on: 2025-10-16
Intelligence Report: Perfect Adobe Experience Manager vulnerability is being exploited CVE-2025-54253 – Help Net Security
1. BLUF (Bottom Line Up Front)
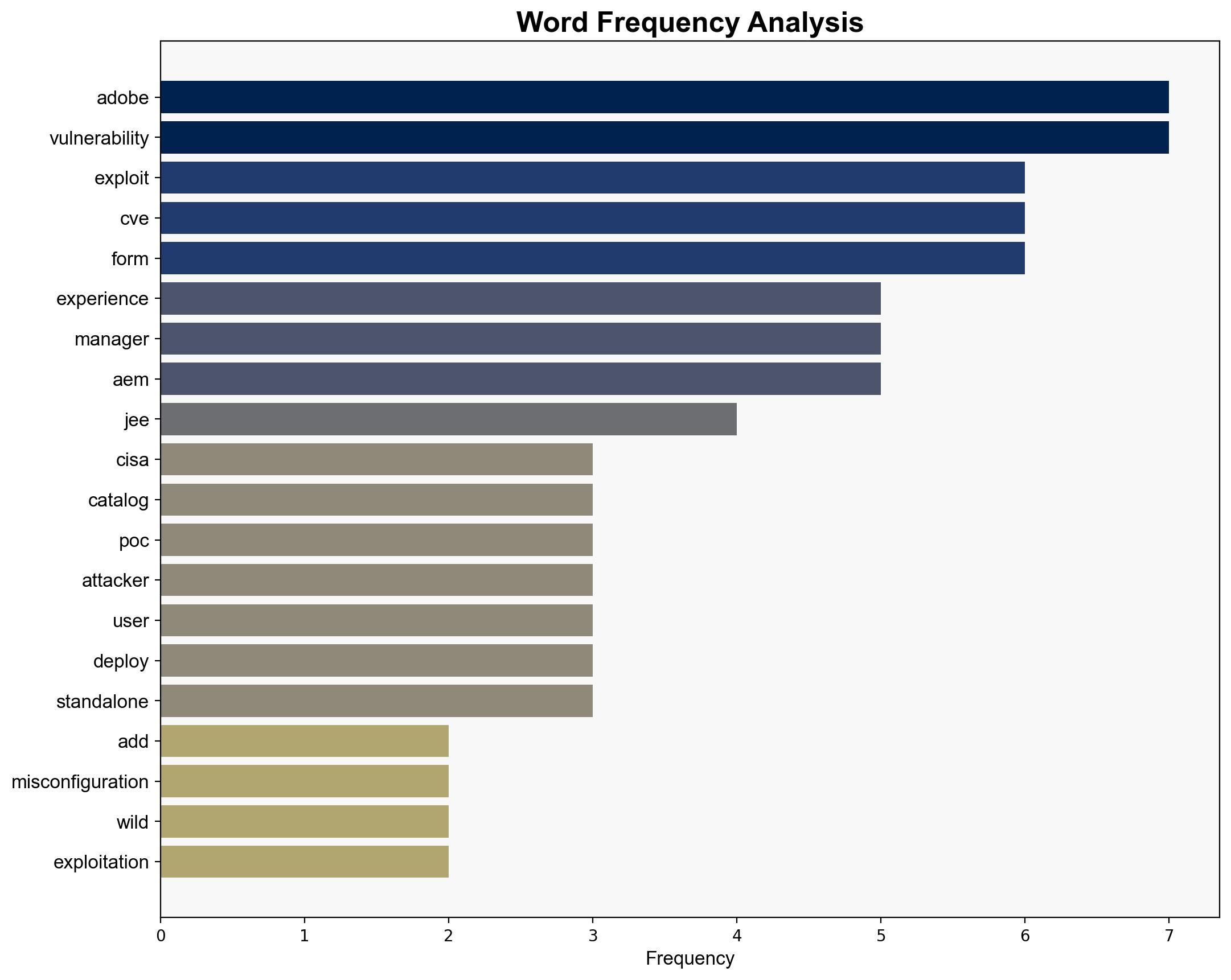
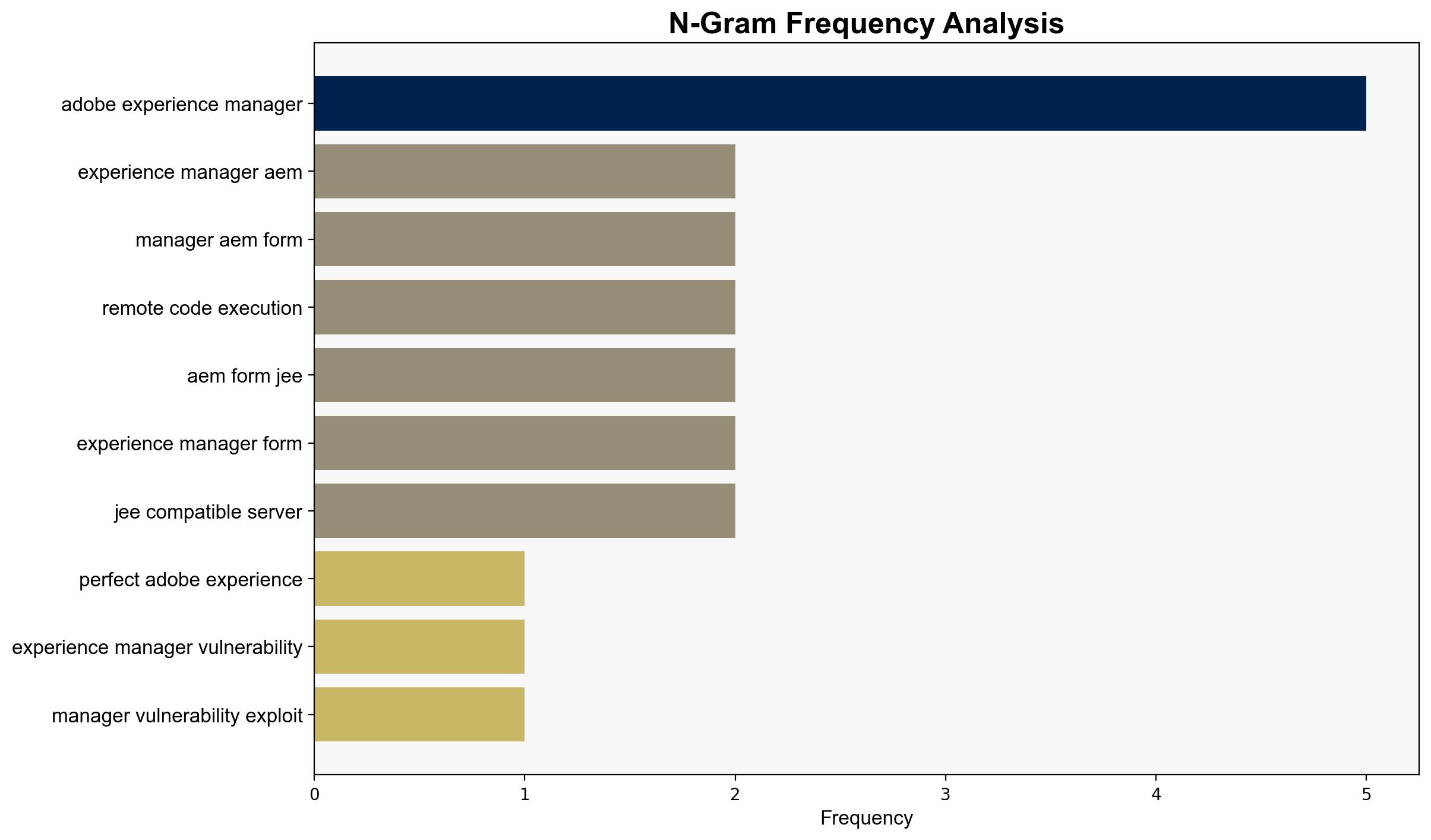
The most supported hypothesis is that the CVE-2025-54253 vulnerability in Adobe Experience Manager (AEM) is being actively exploited due to its low complexity and high impact, posing significant risks to organizations using AEM. Confidence level: High. Recommended action: Immediate patching and restricting access to AEM forms on standalone JEE servers.
2. Competing Hypotheses
1. **Hypothesis A**: The CVE-2025-54253 vulnerability is being actively exploited in the wild due to its ease of exploitation and the availability of a proof-of-concept (PoC) exploit.
2. **Hypothesis B**: The vulnerability is not yet widely exploited, and current reports are isolated incidents or misinterpretations of related vulnerabilities.
Using ACH 2.0, Hypothesis A is better supported due to the presence of a public PoC, the vulnerability’s inclusion in CISA’s Known Exploited Vulnerabilities (KEV) catalog, and reports of active exploitation. Hypothesis B lacks substantial evidence and contradicts the observed pattern of exploitation.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the PoC exploit is effective and accessible to potential attackers. Another assumption is that organizations have not yet fully patched or mitigated the vulnerability.
– **Red Flags**: The lack of detailed incident reports or confirmation from affected organizations could indicate underreporting or misattribution. The absence of a timely patch from Adobe raises questions about the company’s response strategy.
4. Implications and Strategic Risks
The active exploitation of this vulnerability could lead to significant data breaches, unauthorized access, and potential disruption of services. Organizations using AEM are at risk of remote code execution attacks, which could escalate to broader cyber threats. The economic impact could be substantial, especially for industries heavily reliant on AEM for content management.
5. Recommendations and Outlook
- Immediate patching of AEM systems and restricting access to standalone JEE deployments.
- Enhanced monitoring for signs of exploitation and unauthorized access attempts.
- Scenario-based projections:
- **Best Case**: Rapid patching and mitigation efforts prevent widespread exploitation.
- **Worst Case**: Delayed response leads to significant breaches and financial losses.
- **Most Likely**: Continued exploitation until comprehensive patching is achieved.
6. Key Individuals and Entities
– Shubham Shah
– Adam Kues
– Adobe Systems
– CISA (as a reference point for the KEV catalog)
7. Thematic Tags
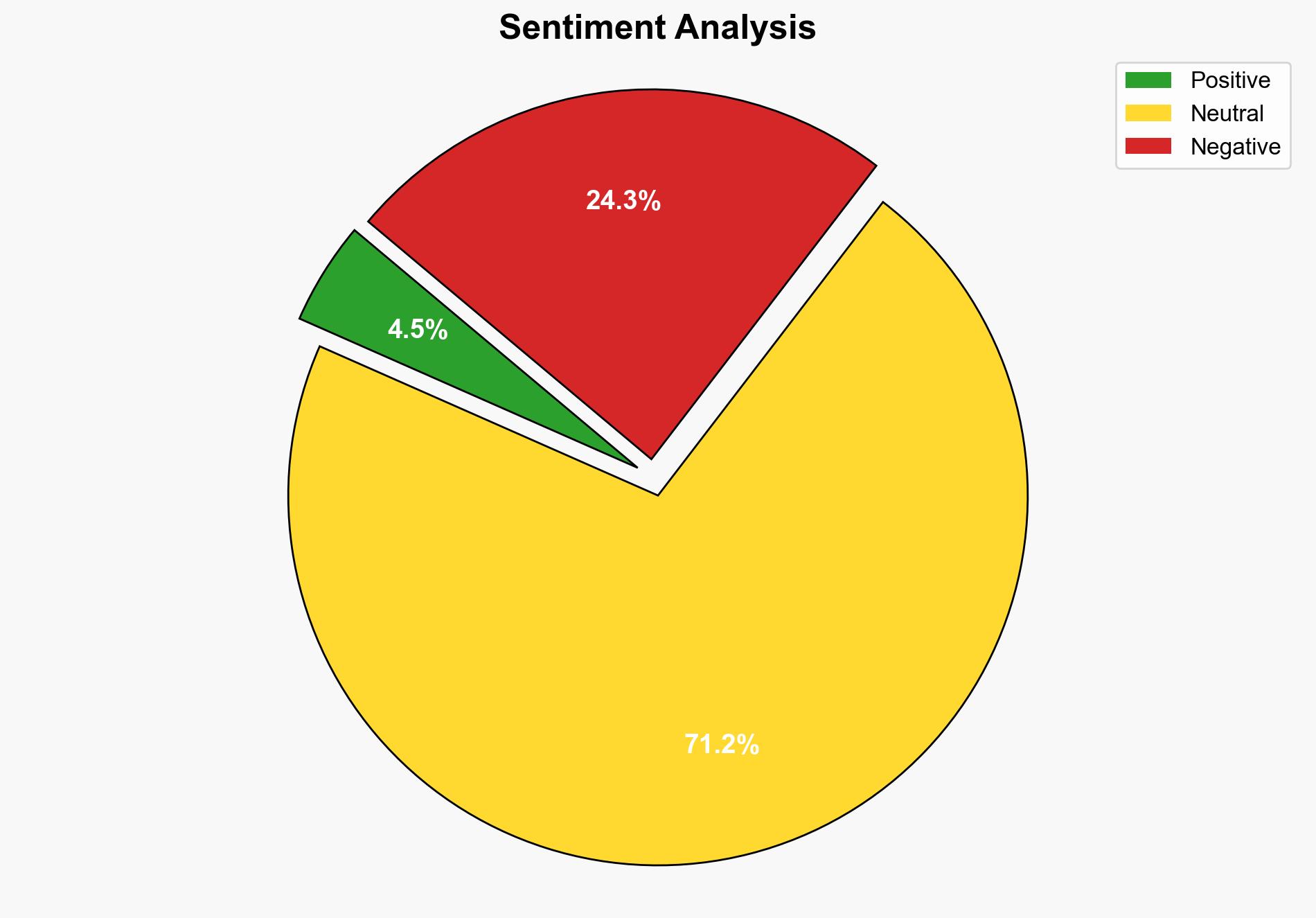
national security threats, cybersecurity, counter-terrorism, regional focus