F5 breach exposes 262000 BIG-IP systems worldwide – Securityaffairs.com
Published on: 2025-10-20
Intelligence Report: F5 breach exposes 262000 BIG-IP systems worldwide – Securityaffairs.com
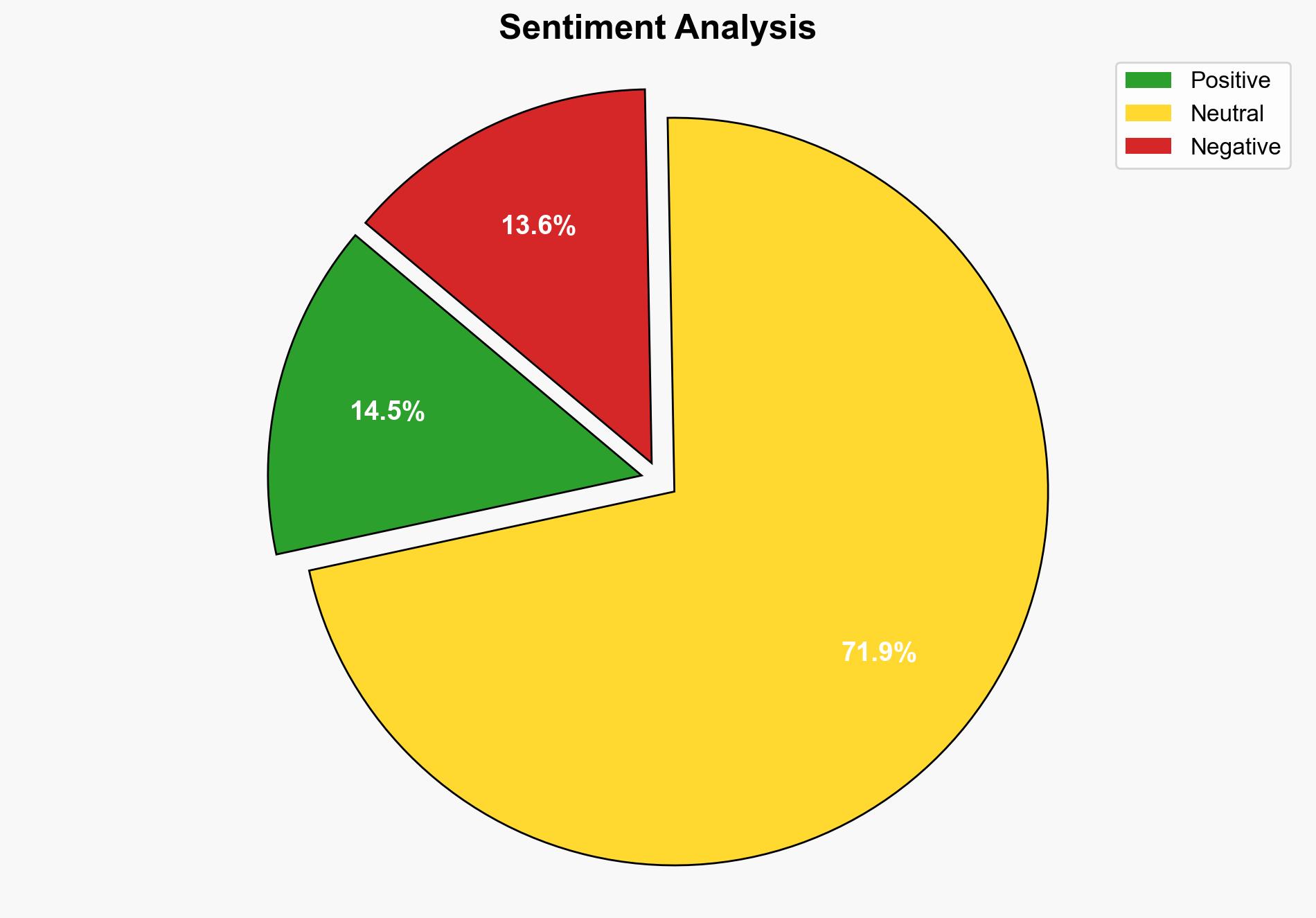
1. BLUF (Bottom Line Up Front)
The breach of F5’s BIG-IP systems is likely orchestrated by a sophisticated nation-state actor, potentially linked to China. The primary hypothesis is supported by the involvement of advanced persistent threat (APT) tactics and the strategic value of the stolen source code. Confidence level: Moderate. Immediate action is recommended to enhance cybersecurity measures and collaborate with international partners to mitigate further risks.
2. Competing Hypotheses
1. **Hypothesis A**: The breach was conducted by a nation-state actor, possibly linked to China, aiming to exploit vulnerabilities for strategic advantage.
– **Supporting Evidence**: The breach involved sophisticated techniques and targeted source code, aligning with known APT behaviors. Historical patterns of Chinese cyber operations support this hypothesis.
2. **Hypothesis B**: The breach was executed by a financially motivated cybercriminal group seeking to sell the stolen data on the black market.
– **Supporting Evidence**: The theft of source code and customer data could be monetized in underground markets. However, the lack of immediate financial exploitation weakens this hypothesis.
Using ACH 2.0, Hypothesis A is better supported due to the alignment of tactics with known nation-state operations and the strategic implications of the breach.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the breach’s sophistication indicates nation-state involvement. The assumption that China is involved is based on historical patterns rather than direct evidence.
– **Red Flags**: The delay in disclosure and the lack of specific attribution raise questions about the completeness of the intelligence.
– **Blind Spots**: Potential involvement of other nation-states or non-state actors remains unexplored. The full extent of data compromise is unclear.
4. Implications and Strategic Risks
The breach poses significant risks to global cybersecurity infrastructure, potentially enabling further exploitation of vulnerabilities in critical systems. Economically, it could lead to increased costs for cybersecurity measures and damage to F5’s reputation. Geopolitically, it may escalate tensions between China and affected nations, particularly if attribution is confirmed. The psychological impact includes eroded trust in cybersecurity measures and increased fear of cyber threats.
5. Recommendations and Outlook
- Enhance international collaboration to trace and attribute the breach, leveraging intelligence-sharing frameworks.
- Implement immediate cybersecurity measures, including patching vulnerabilities and enhancing monitoring systems.
- Scenario Projections:
- **Best Case**: Rapid containment and attribution lead to strengthened cybersecurity alliances.
- **Worst Case**: Continued exploitation of vulnerabilities results in widespread disruption of critical infrastructure.
- **Most Likely**: Incremental improvements in cybersecurity posture with ongoing risks of similar breaches.
6. Key Individuals and Entities
– F5 Networks
– Shadowserver Foundation
– NCC Group
– CrowdStrike
– UK NCSC
– CISA
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus