Hackers are exploiting OAuth loophole for persistent access – and resetting your password won’t save you – TechRadar
Published on: 2025-10-22
Intelligence Report: Hackers are exploiting OAuth loophole for persistent access – and resetting your password won’t save you – TechRadar
1. BLUF (Bottom Line Up Front)
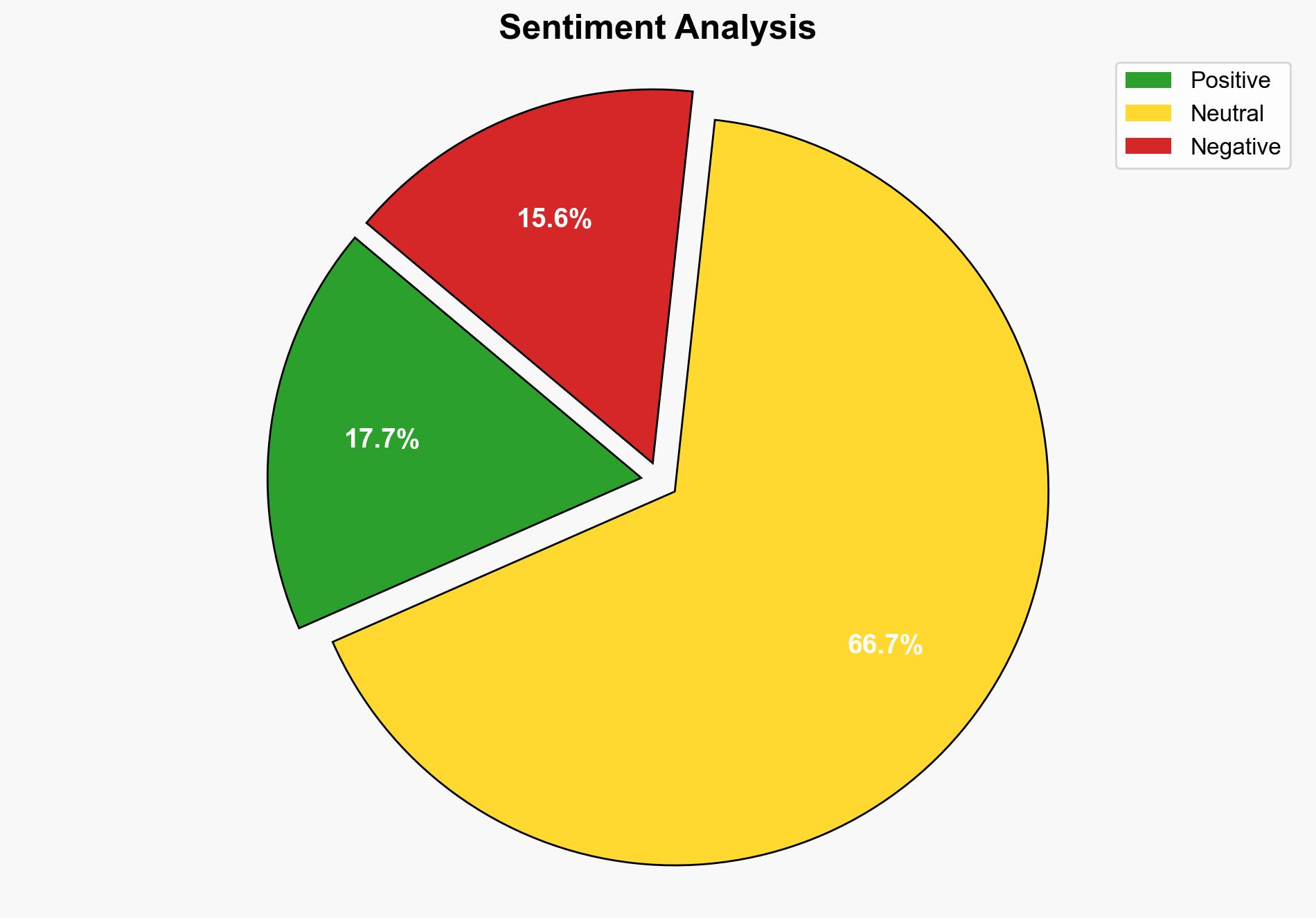
The most supported hypothesis is that cybercriminals are leveraging OAuth application vulnerabilities to maintain persistent access to cloud accounts, bypassing traditional security measures like password resets and multi-factor authentication (MFA). This tactic poses a significant threat to cybersecurity, necessitating immediate strategic actions to enhance monitoring and access control measures. Confidence level: High.
2. Competing Hypotheses
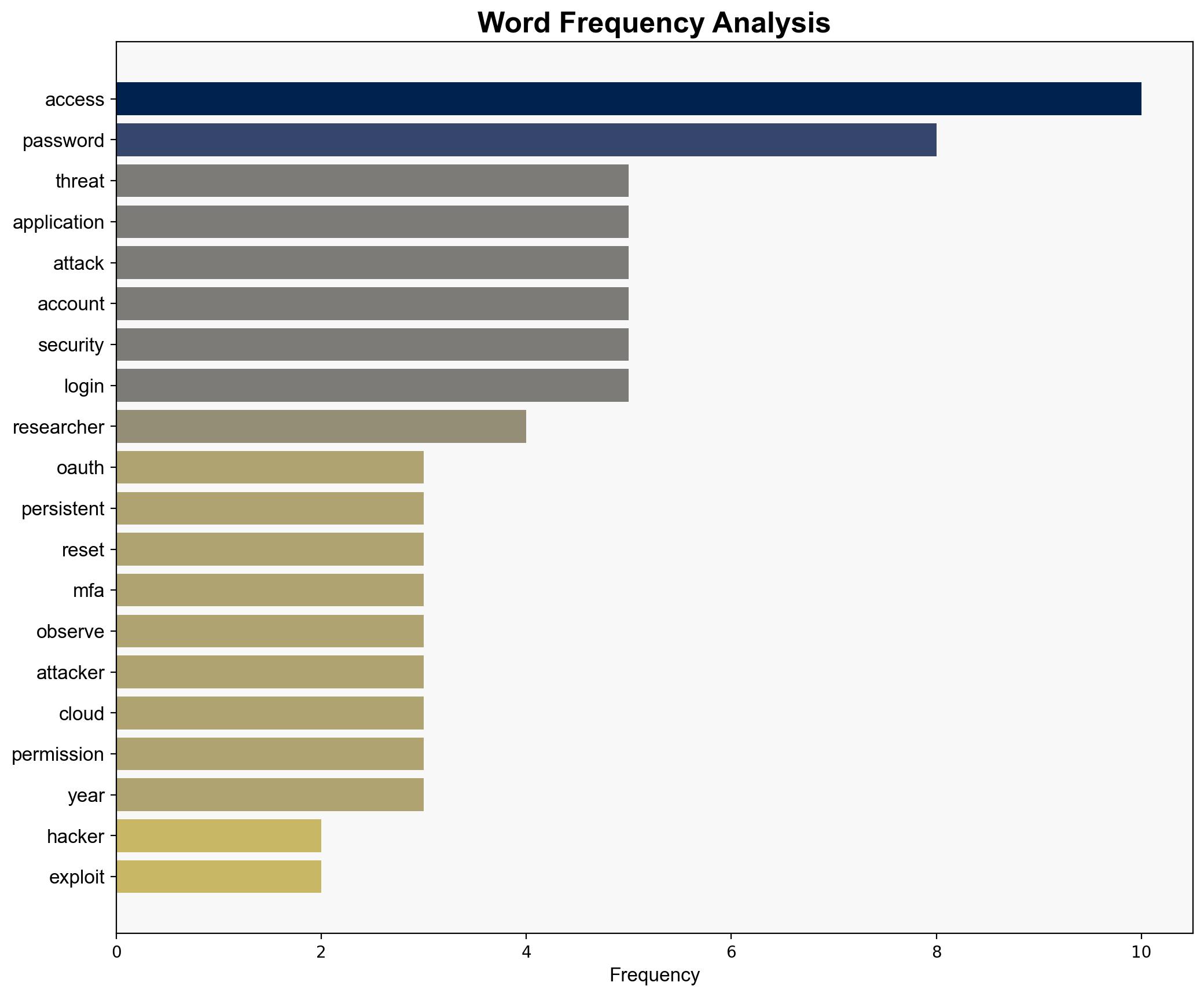
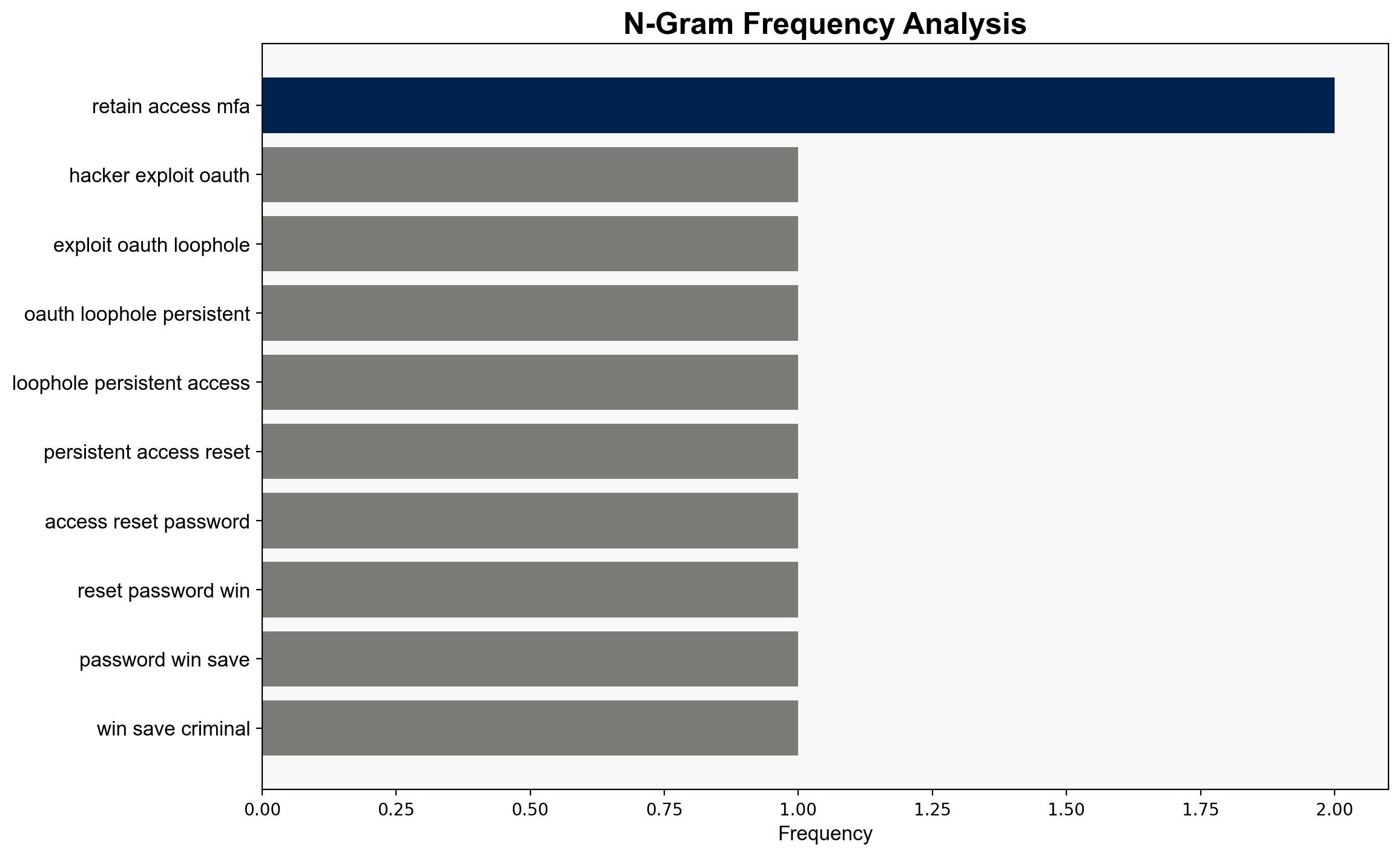
Hypothesis 1: Cybercriminals are exploiting OAuth loopholes to gain and maintain unauthorized access to cloud accounts, circumventing password resets and MFA. This approach allows them to execute prolonged attacks without detection.
Hypothesis 2: The observed OAuth loophole exploitation is primarily a proof-of-concept by security researchers, with limited real-world application by threat actors. The threat is currently more theoretical than operational.
3. Key Assumptions and Red Flags
Assumptions:
– Hypothesis 1 assumes that threat actors have the technical capability and motivation to exploit OAuth vulnerabilities at scale.
– Hypothesis 2 assumes that the lack of widespread reports of such attacks indicates limited adoption by cybercriminals.
Red Flags:
– The reliance on a single source for threat actor behavior may introduce confirmation bias.
– Lack of detailed case studies or examples of successful OAuth exploitation in the wild.
4. Implications and Strategic Risks
The exploitation of OAuth vulnerabilities could lead to increased frequency and severity of cloud account takeovers, potentially resulting in data breaches, financial losses, and reputational damage. The evolving nature of these tactics suggests a need for continuous adaptation of cybersecurity strategies. Geopolitically, this could escalate tensions if state-sponsored actors are implicated, leading to potential retaliatory measures.
5. Recommendations and Outlook
- Enhance monitoring of OAuth applications and regularly review permissions to detect and revoke unauthorized access.
- Implement robust security protocols, including anomaly detection systems, to identify suspicious activities.
- Scenario Projections:
- Best Case: Improved security measures successfully mitigate OAuth exploitation, reducing attack frequency.
- Worst Case: Widespread adoption of OAuth exploitation leads to significant data breaches and financial losses.
- Most Likely: Incremental improvements in security measures lead to a gradual decrease in successful OAuth-based attacks.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The report references researchers and threat actors in general terms.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus