Bitter APT Exploiting Old WinRAR Vulnerability in New Backdoor Attacks – HackRead
Published on: 2025-10-22
Intelligence Report: Bitter APT Exploiting Old WinRAR Vulnerability in New Backdoor Attacks – HackRead
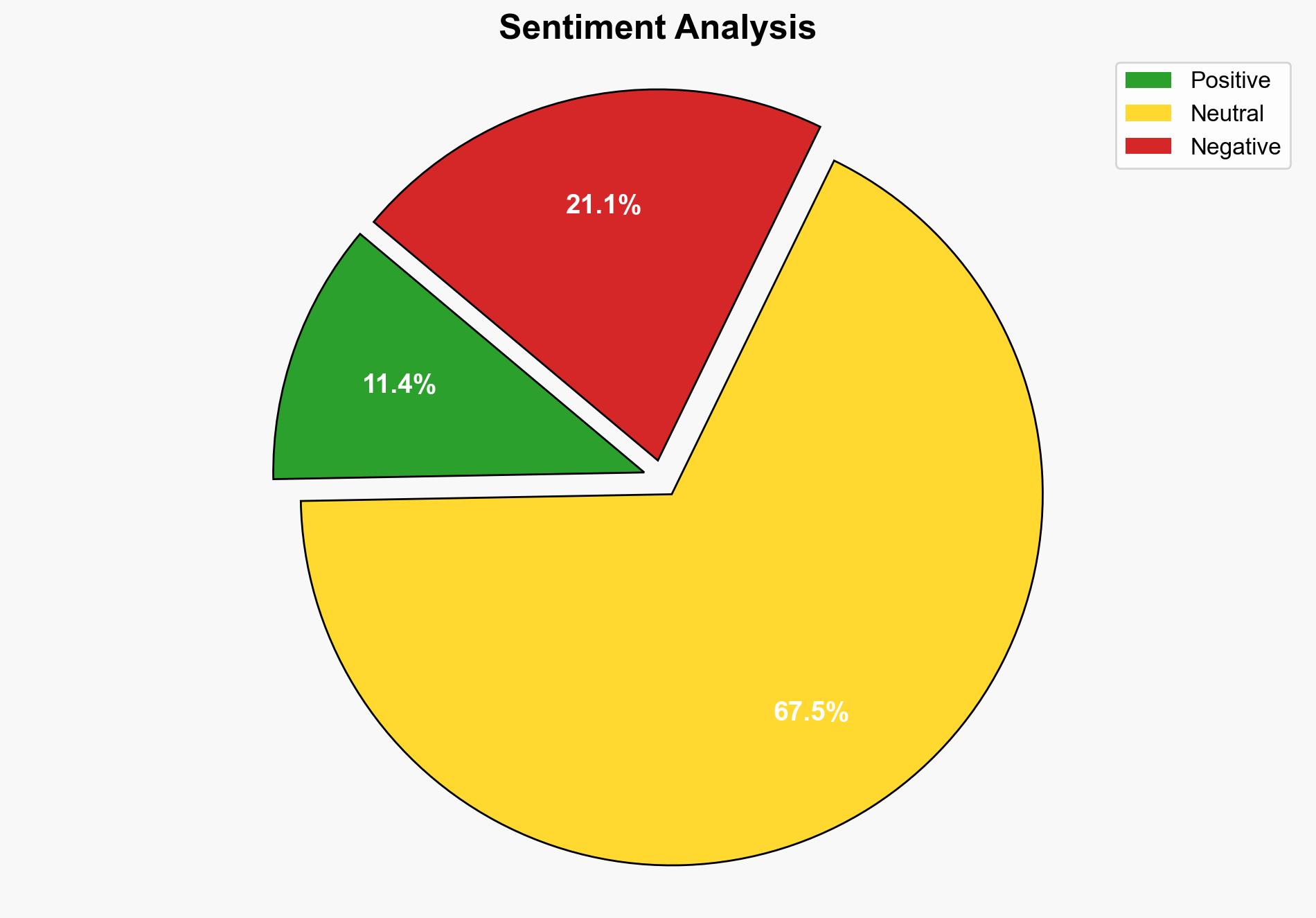
1. BLUF (Bottom Line Up Front)
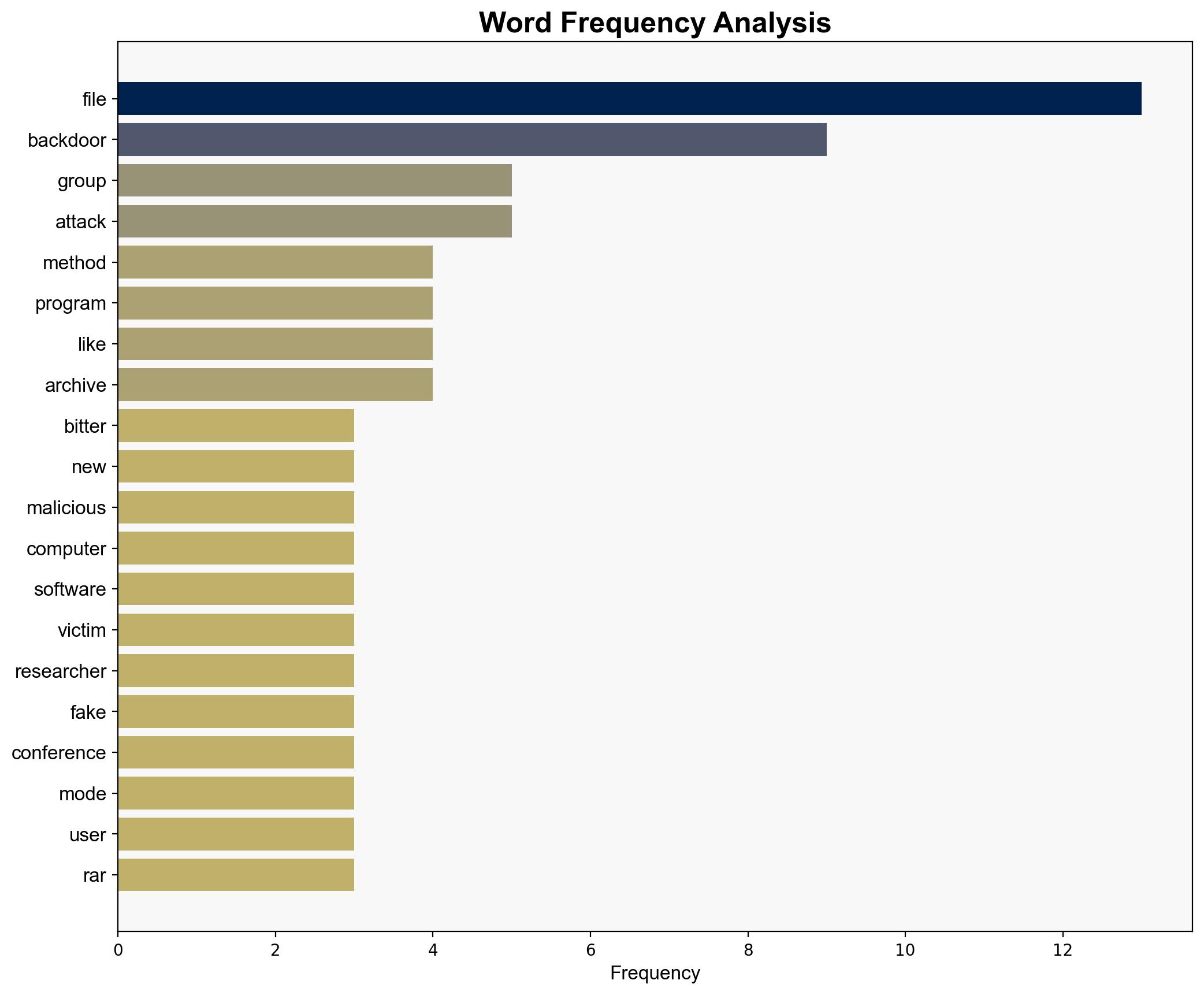
The Bitter APT group is leveraging an old WinRAR vulnerability to deploy backdoor attacks on high-value targets, primarily in South Asia. The most supported hypothesis is that Bitter APT is focusing on espionage activities against government and critical infrastructure sectors. Confidence level is moderate due to limited clarity on the exact vulnerability exploited. Recommended action includes immediate patching of WinRAR vulnerabilities, enhanced monitoring of network traffic, and user education on phishing tactics.
2. Competing Hypotheses
1. **Hypothesis A**: Bitter APT is exploiting the WinRAR vulnerability primarily for espionage purposes, targeting government and critical infrastructure sectors to gather sensitive information.
2. **Hypothesis B**: Bitter APT is using the WinRAR vulnerability as a diversionary tactic, with the primary objective being financial gain through ransomware or other cybercriminal activities.
Using ACH 2.0, Hypothesis A is better supported due to the historical focus of Bitter APT on espionage and the nature of the targets (government, military, and electric power sectors). Hypothesis B lacks evidence of financial motives or ransomware deployment in the current attacks.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Bitter APT’s primary motivation remains espionage, consistent with past behavior. Another assumption is that the vulnerability exploited is indeed an old WinRAR flaw, though specifics are unclear.
– **Red Flags**: The exact vulnerability in WinRAR is not specified, raising questions about the accuracy of the threat assessment. The lack of financial motive evidence could indicate a potential blind spot in understanding the group’s full objectives.
4. Implications and Strategic Risks
The continued exploitation of software vulnerabilities by Bitter APT poses significant risks to national security, particularly in South Asia. The potential for data breaches in government and critical infrastructure sectors could lead to geopolitical tensions. There is also a risk of cascading cyber threats if the backdoor is used to launch further attacks or exfiltrate sensitive data.
5. Recommendations and Outlook
- **Mitigation Actions**: Patch all known vulnerabilities in WinRAR and other software promptly. Implement strict email filtering and user education programs to prevent phishing attacks.
- **Scenario Projections**:
– **Best Case**: Vulnerabilities are patched, and attacks are thwarted with minimal data loss.
– **Worst Case**: Successful data exfiltration leads to significant geopolitical fallout and further cyberattacks.
– **Most Likely**: Continued attempts by Bitter APT to exploit vulnerabilities, requiring ongoing vigilance and cybersecurity enhancements.
6. Key Individuals and Entities
No specific individuals are named in the intelligence. Entities involved include Bitter APT and the Qianxin Threat Intelligence Centre.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus