Microsoft releases urgent fix for actively exploited WSUS vulnerability CVE-2025-59287 – Help Net Security
Published on: 2025-10-24
Intelligence Report: Microsoft releases urgent fix for actively exploited WSUS vulnerability CVE-2025-59287 – Help Net Security
1. BLUF (Bottom Line Up Front)
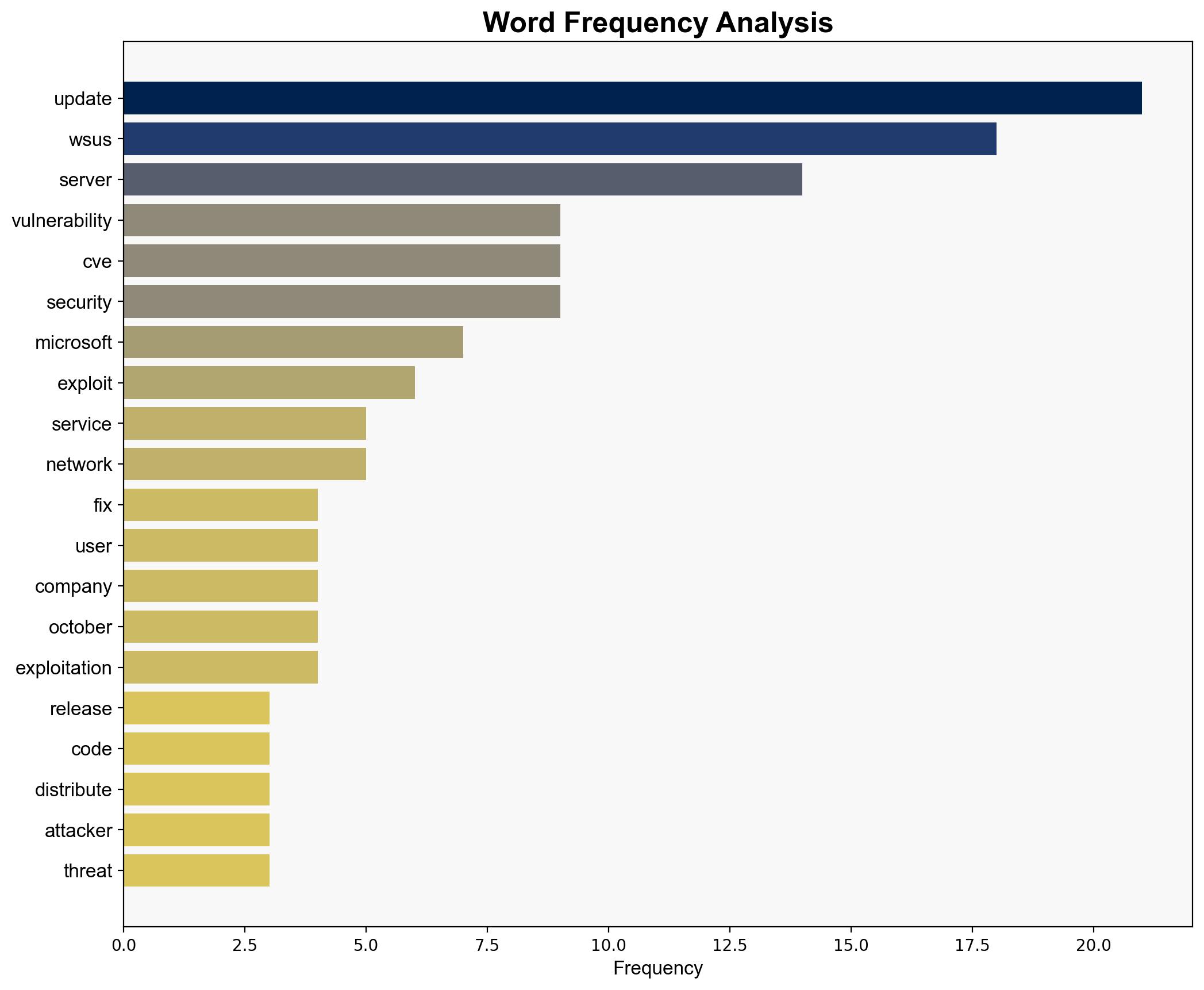
The most supported hypothesis is that the CVE-2025-59287 vulnerability is being actively exploited by sophisticated threat actors, potentially state-sponsored or advanced ransomware groups, to gain control over WSUS servers and distribute malicious updates. Confidence level is moderate due to the presence of proof-of-concept exploit code and observed exploitation attempts. Immediate implementation of Microsoft’s patch is recommended to mitigate the risk.
2. Competing Hypotheses
1. **Hypothesis A**: The vulnerability is primarily being exploited by state-sponsored actors or advanced ransomware gangs to target critical infrastructure and large enterprises, leveraging the WSUS server’s role in distributing updates to propagate malware.
2. **Hypothesis B**: The vulnerability is being exploited by less sophisticated actors, such as script kiddies, who are using publicly available proof-of-concept exploit code to opportunistically target vulnerable systems without a strategic focus.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the complexity of the exploit and the strategic value of compromising WSUS servers, which aligns with the capabilities and objectives of advanced threat actors.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the presence of proof-of-concept code and observed exploitation attempts indicate active targeting by sophisticated actors. The assumption that WSUS servers are critical targets for state-sponsored actors due to their role in update distribution is central to Hypothesis A.
– **Red Flags**: The rapid public disclosure of the vulnerability and proof-of-concept code could indicate a deliberate attempt to create panic or misdirection. The lack of detailed attribution to specific threat actors raises questions about the true nature of the threat.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to widespread malware distribution, affecting numerous organizations and potentially critical infrastructure. The risk of cascading effects is high, as compromised WSUS servers can be used to push malicious updates across networks. Geopolitically, this could escalate tensions if state-sponsored involvement is confirmed. Economically, affected organizations may face significant recovery costs and reputational damage.
5. Recommendations and Outlook
- Organizations should immediately apply Microsoft’s patch to mitigate the vulnerability.
- Conduct a thorough review of WSUS server configurations to ensure proper firewall settings and network segmentation.
- Monitor for indicators of compromise and unusual network activity.
- Scenario Projections:
- **Best Case**: Rapid patch deployment prevents further exploitation, and no significant incidents occur.
- **Worst Case**: Widespread exploitation leads to significant disruptions in critical infrastructure and enterprise operations.
- **Most Likely**: Mixed outcomes with some organizations successfully mitigating the threat while others suffer localized impacts.
6. Key Individuals and Entities
– Dustin Childs
– Piet Kerkhof
– Bas van den Berg
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus