Cyberattacks on Federal Workers Double Following Shutdown – pymnts.com
Published on: 2025-10-27
Intelligence Report: Cyberattacks on Federal Workers Double Following Shutdown – pymnts.com
1. BLUF (Bottom Line Up Front)
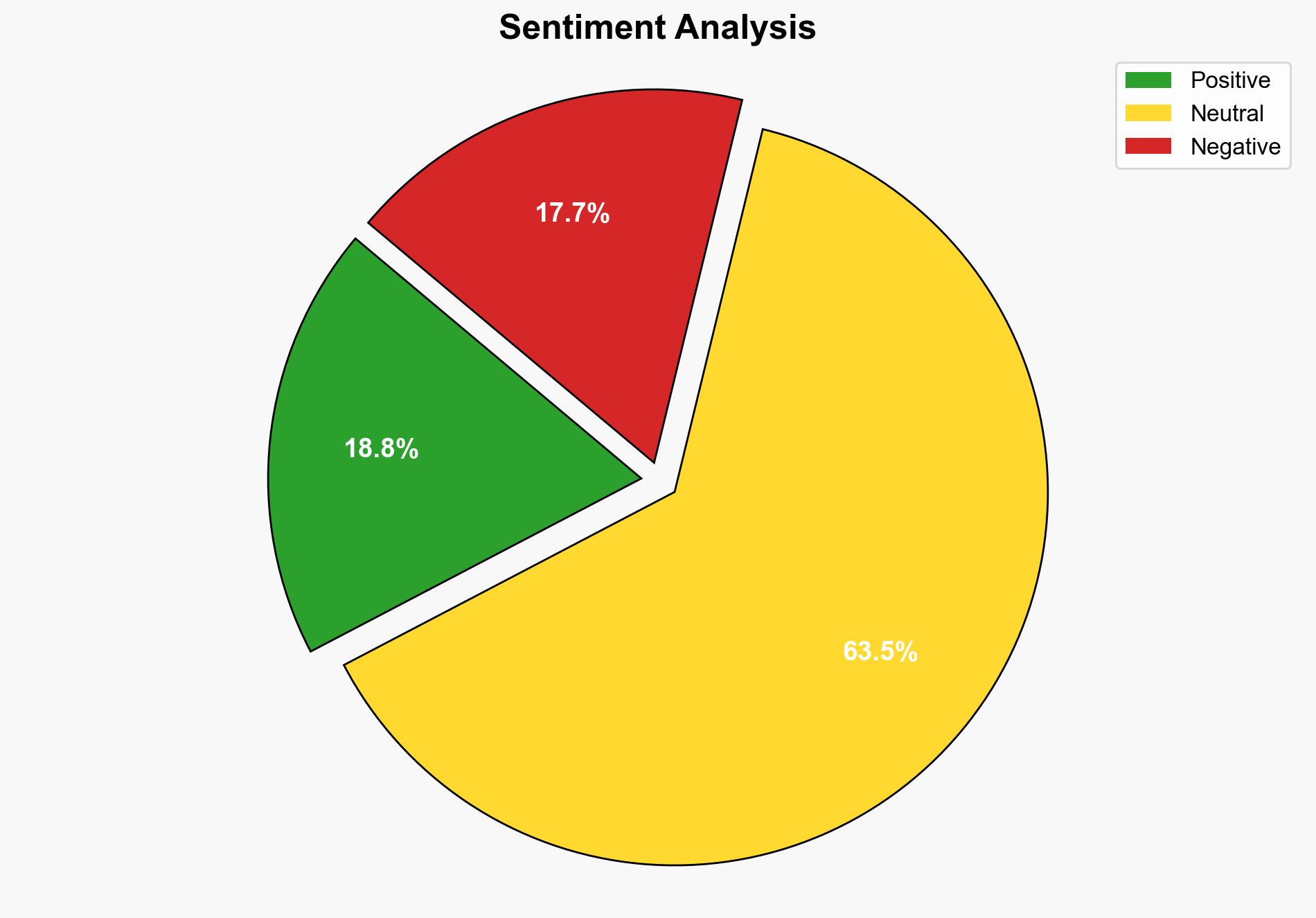
The surge in cyberattacks on federal workers following the government shutdown is likely driven by increased vulnerability due to furloughs and financial stress. The most supported hypothesis is that cybercriminals are exploiting these vulnerabilities. Confidence level: Moderate. Recommended action includes enhancing cybersecurity awareness and resilience among federal employees, particularly during periods of financial instability.
2. Competing Hypotheses
1. **Hypothesis A**: The increase in cyberattacks is primarily due to cybercriminals exploiting the vulnerabilities created by the government shutdown, such as furloughed workers and financial stress.
2. **Hypothesis B**: The rise in cyberattacks is coincidental and part of a broader trend of increasing cyber threats targeting government entities, unrelated to the shutdown.
Using Analysis of Competing Hypotheses (ACH), Hypothesis A is better supported due to the timing of the attacks coinciding with the shutdown and the specific targeting of financially stressed employees.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that cybercriminals have the capability and intent to exploit specific vulnerabilities related to the shutdown. Another assumption is that the reported increase in attacks is accurately measured and reported.
– **Red Flags**: Lack of detailed attribution of the cyberattacks raises questions about the source and intent. The potential for confirmation bias exists if analysts focus solely on shutdown-related factors without considering broader trends.
4. Implications and Strategic Risks
The increase in cyberattacks poses significant risks to national security, particularly if sensitive information is compromised. The psychological impact on federal employees, combined with financial stress, could lead to decreased morale and productivity. If not addressed, these vulnerabilities could be exploited further, leading to more sophisticated attacks.
5. Recommendations and Outlook
- Enhance cybersecurity training and awareness for federal employees, focusing on phishing and social engineering threats.
- Implement robust monitoring and incident response protocols to detect and mitigate attacks swiftly.
- Scenario Projections:
- Best Case: Increased awareness and improved defenses lead to a reduction in successful attacks.
- Worst Case: Continued exploitation of vulnerabilities results in significant data breaches and operational disruptions.
- Most Likely: A moderate reduction in attacks as immediate vulnerabilities are addressed, but ongoing threats persist.
6. Key Individuals and Entities
– Chris Olson
– Justin Miller
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus