Uncovering Qilin attack methods exposed through multiple cases – Talosintelligence.com
Published on: 2025-10-27
Intelligence Report: Uncovering Qilin attack methods exposed through multiple cases – Talosintelligence.com
1. BLUF (Bottom Line Up Front)
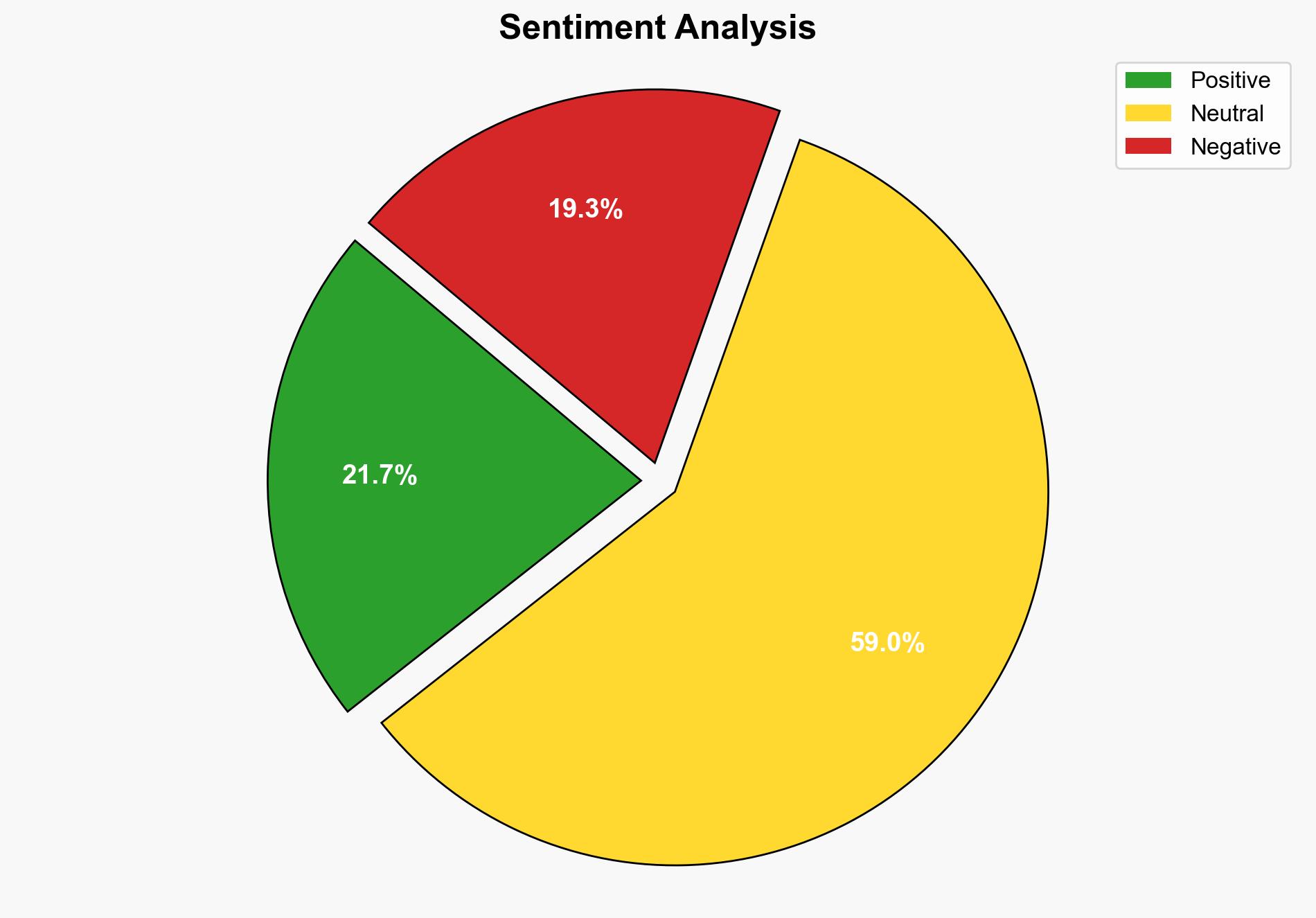
The analysis suggests that the Qilin attack methods may involve sophisticated SQL injection techniques that are triggering security solutions, such as those provided by Cloudflare. The most supported hypothesis is that these methods are part of a broader, coordinated cyber campaign targeting multiple entities. Confidence in this hypothesis is moderate due to the lack of direct evidence linking specific attacks to Qilin. Recommended action includes enhancing SQL injection defenses and increasing monitoring of potential coordinated attack patterns.
2. Competing Hypotheses
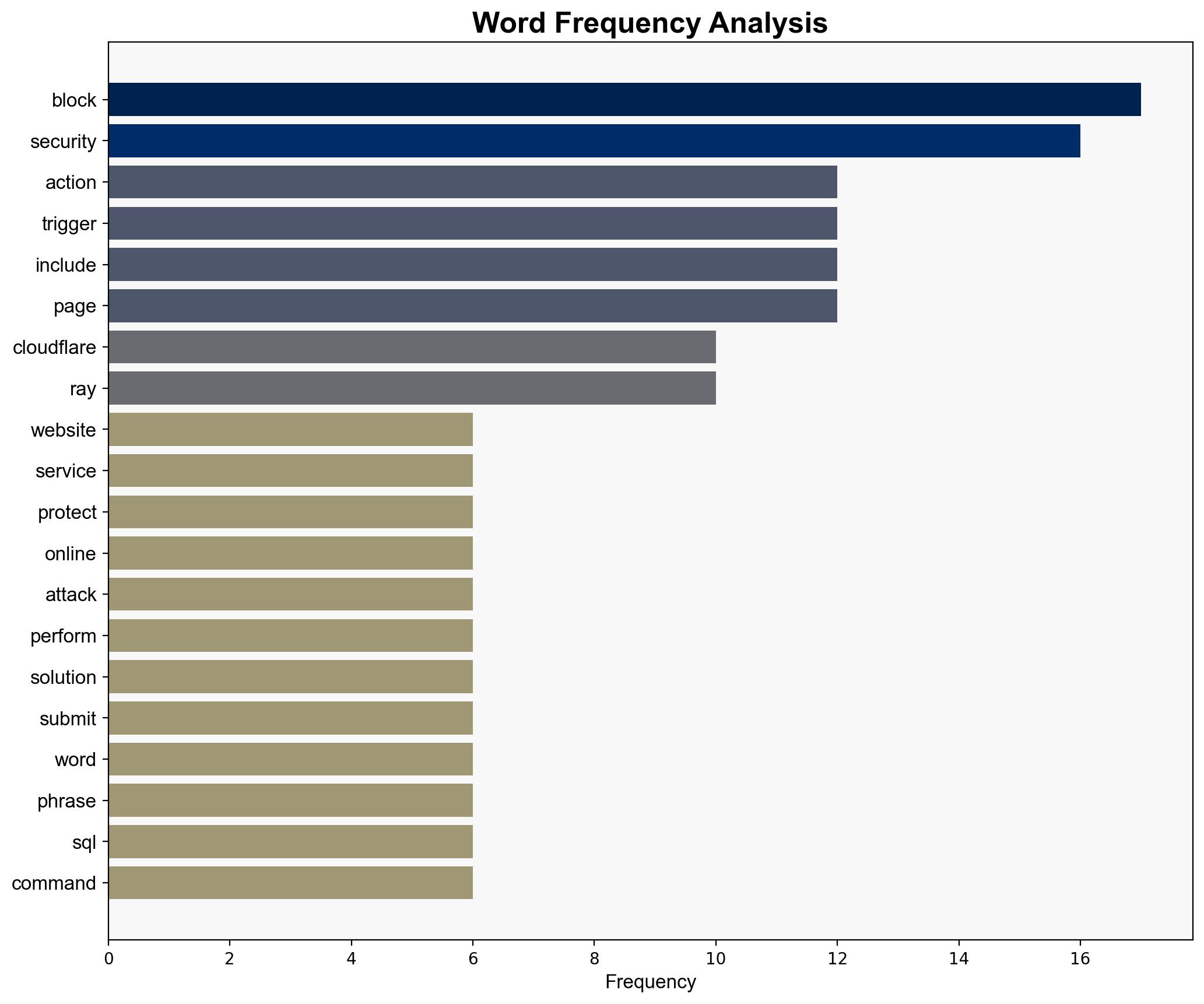
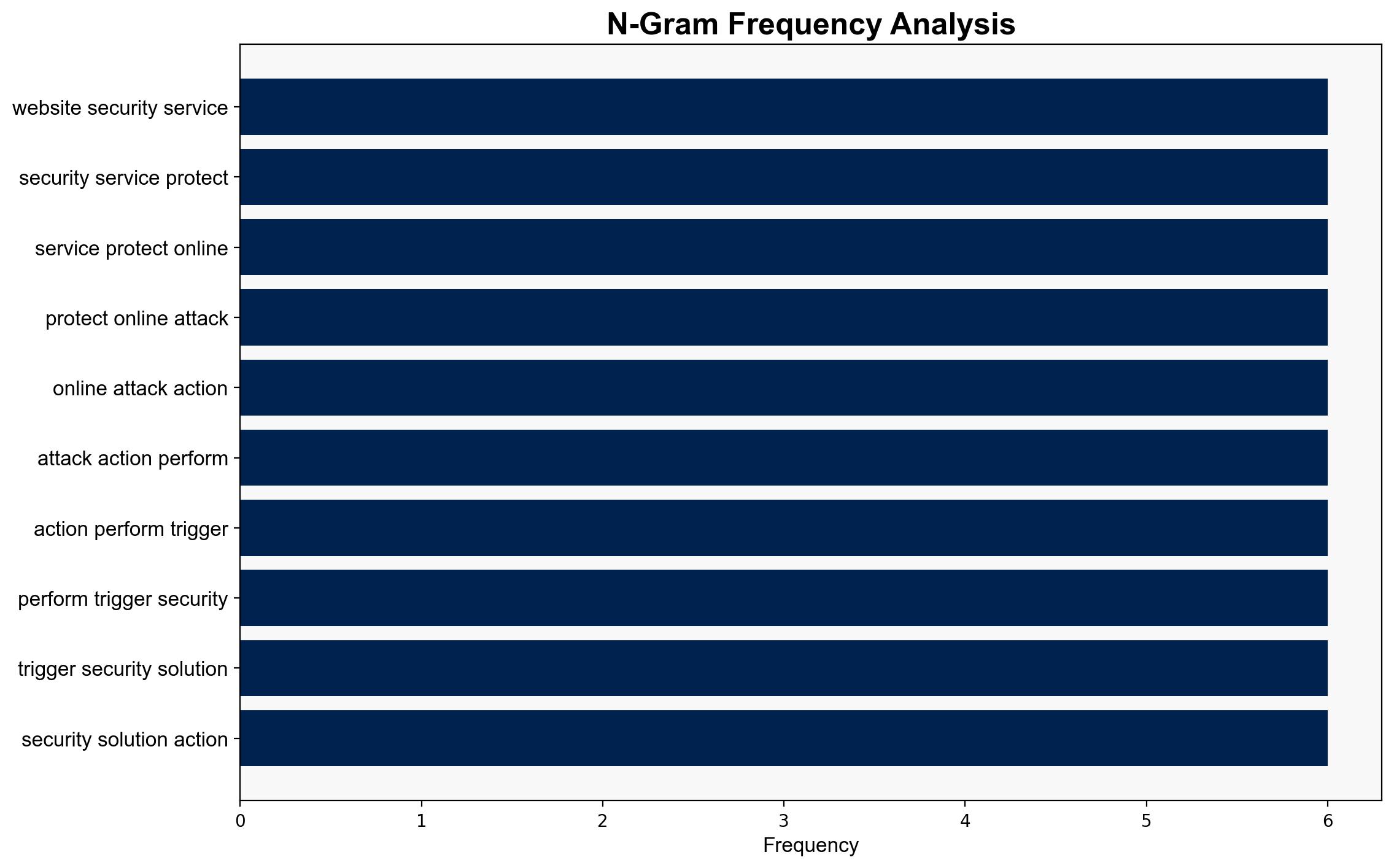
– **Hypothesis 1**: The Qilin attack methods are primarily focused on exploiting SQL injection vulnerabilities to disrupt services and extract data. This hypothesis is supported by the repeated mention of SQL commands and malformed data triggering security solutions.
– **Hypothesis 2**: The Qilin attack methods are a decoy, designed to trigger security responses and gather intelligence on defensive measures. This hypothesis considers the possibility that the attacks are probing for weaknesses in security protocols rather than causing direct harm.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the repeated blocking by security services is indicative of a deliberate attack pattern rather than random or benign activity. The presence of SQL commands suggests a technical focus on database vulnerabilities.
– **Red Flags**: The lack of specific attribution to Qilin raises questions about the true origin of the attacks. The repetitive nature of the blocked actions could indicate either persistent threat actors or automated scripts.
4. Implications and Strategic Risks
The potential for these attacks to escalate into more damaging breaches poses a significant risk to cybersecurity infrastructure. If these methods are part of a coordinated campaign, there could be broader implications for national security and economic stability. The psychological impact of persistent cyber threats may also erode trust in digital services.
5. Recommendations and Outlook
- Enhance SQL injection defenses across critical systems and conduct regular penetration testing to identify vulnerabilities.
- Increase monitoring and logging of security events to detect patterns indicative of coordinated attacks.
- Scenario-based projections:
- Best Case: Improved defenses deter future attacks, reducing the threat level.
- Worst Case: Attacks escalate, leading to significant data breaches and service disruptions.
- Most Likely: Continued probing by attackers with sporadic successful intrusions.
6. Key Individuals and Entities
No specific individuals are identified in the intelligence. The entity Cloudflare is mentioned as a security service provider involved in blocking the attacks.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus