PoC code drops for remotely exploitable BIND 9 DNS flaw CVE-2025-40778 – Help Net Security
Published on: 2025-10-28
Intelligence Report: PoC code drops for remotely exploitable BIND 9 DNS flaw CVE-2025-40778 – Help Net Security
1. BLUF (Bottom Line Up Front)
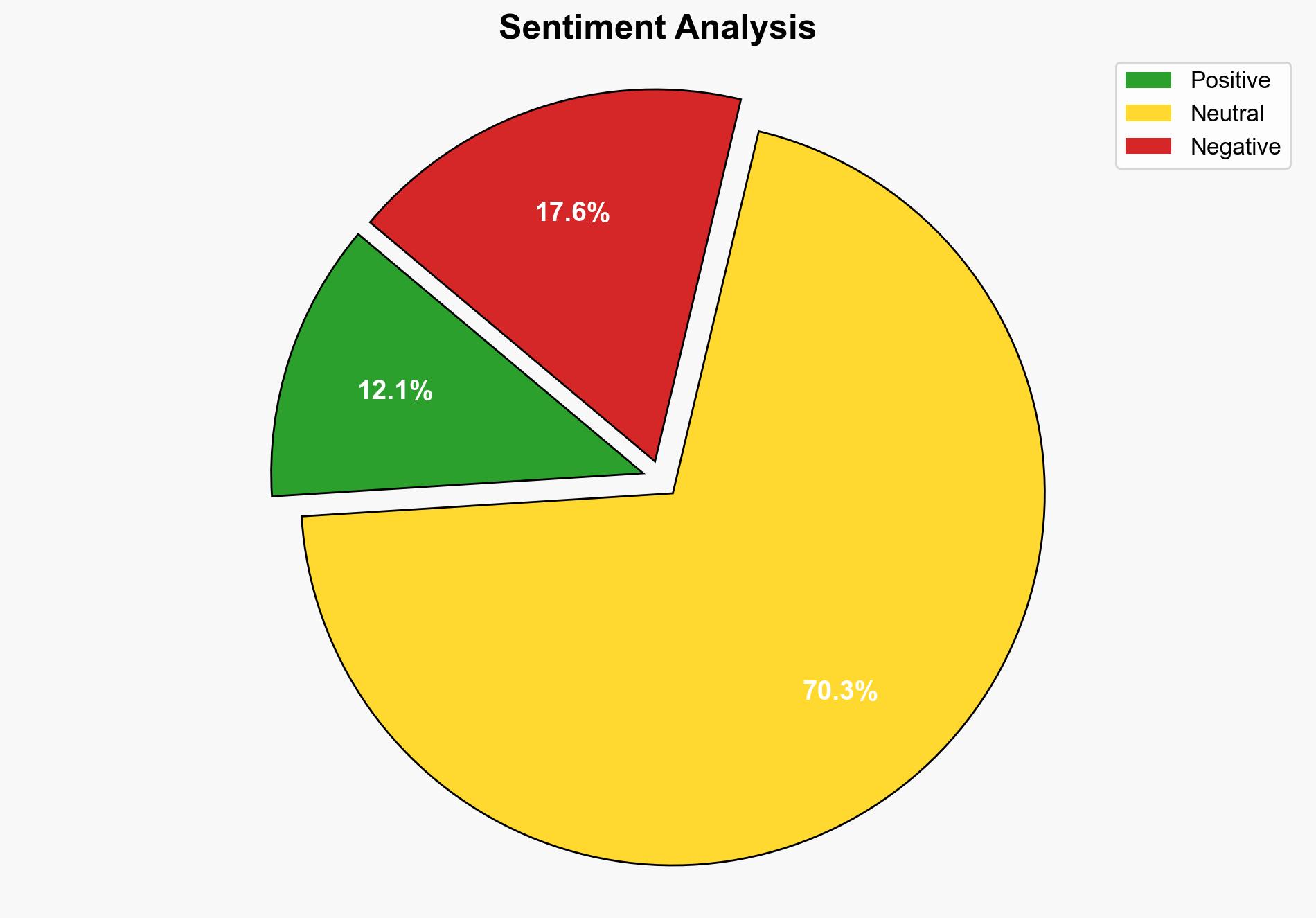
There is a high-confidence assessment that the release of proof-of-concept (PoC) code for the BIND 9 DNS flaw (CVE-2025-40778) poses a significant cybersecurity threat, primarily due to its potential for cache poisoning and traffic redirection. The most supported hypothesis is that malicious actors will exploit this vulnerability to conduct widespread attacks. Immediate patching and enhanced monitoring are recommended to mitigate risks.
2. Competing Hypotheses
Hypothesis 1: Malicious actors will exploit the BIND 9 DNS flaw to conduct targeted attacks on specific organizations or sectors, leveraging the vulnerability for espionage or financial gain.
Hypothesis 2: The BIND 9 DNS flaw will primarily be exploited in opportunistic attacks, affecting a broad range of targets indiscriminately, leading to widespread disruptions and potential collateral damage.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported by the specificity of the vulnerability and the potential for high-value targets. However, Hypothesis 2 cannot be ruled out due to the nature of DNS infrastructure being a common target for widespread attacks.
3. Key Assumptions and Red Flags
Assumptions include the belief that all administrators will promptly patch their systems, which may not be the case due to resource constraints. A red flag is the lack of detailed information on the exploit’s complexity, which could affect the rate of exploitation. Additionally, there is a potential blind spot regarding the coordination among malicious actors to exploit this flaw.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant disruptions in internet services, economic losses, and erosion of trust in digital infrastructure. There is a risk of cascading effects if critical infrastructure is targeted, potentially escalating to geopolitical tensions if state actors are involved. The psychological impact on users and organizations could lead to increased demand for cybersecurity solutions and policy interventions.
5. Recommendations and Outlook
- Immediate patching of affected systems is crucial. Organizations should prioritize updates to BIND 9 DNS servers.
- Implement enhanced monitoring of DNS traffic and cache activities to detect and mitigate potential attacks quickly.
- Scenario-based projections:
- Best Case: Rapid patch deployment minimizes impact, with no significant exploitation observed.
- Worst Case: Widespread exploitation leads to major service disruptions and economic losses.
- Most Likely: Targeted attacks on vulnerable sectors, with moderate disruptions and increased cybersecurity measures.
6. Key Individuals and Entities
The Internet Systems Consortium (ISC) is a key entity responsible for the development and maintenance of BIND 9. No specific individuals are named in the source text.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus