New TEEFail Side-Channel Attack Extracts Secrets from Intel and AMD DDR5 Secure Enclaves – Internet
Published on: 2025-10-28
Intelligence Report: New TEEFail Side-Channel Attack Extracts Secrets from Intel and AMD DDR5 Secure Enclaves – Internet
1. BLUF (Bottom Line Up Front)
The TEEFail side-channel attack represents a significant vulnerability in Intel and AMD’s secure enclave technologies, potentially compromising sensitive data. The most supported hypothesis is that this attack could lead to widespread exploitation if not promptly addressed. Confidence level: High. Recommended action: Immediate development and deployment of software countermeasures, alongside hardware design reviews to mitigate future risks.
2. Competing Hypotheses
1. **Hypothesis A**: The TEEFail attack is a critical vulnerability that can be widely exploited, leading to significant breaches in secure computing environments.
– **Evidence**: The attack allows extraction of cryptographic keys and attestation keys, compromising the trust status of machines.
– **SAT Applied**: Analysis of Competing Hypotheses (ACH) 2.0 shows strong alignment with known vulnerabilities in deterministic encryption and physical memory interposition.
2. **Hypothesis B**: The TEEFail attack is a limited threat, primarily affecting systems with specific configurations or under certain conditions.
– **Evidence**: The attack requires physical access and custom equipment, which may limit its applicability.
– **SAT Applied**: Bayesian Scenario Modeling suggests a lower probability of widespread impact due to these constraints.
Hypothesis A is better supported due to the fundamental nature of the vulnerability affecting core security mechanisms in widely used technologies.
3. Key Assumptions and Red Flags
– **Assumptions**:
– The attack can be replicated outside controlled environments.
– Current encryption methods are insufficient against physical interposition.
– **Red Flags**:
– Lack of detailed mitigation strategies from Intel and AMD.
– Potential underestimation of the attack’s scope due to reliance on physical access constraints.
4. Implications and Strategic Risks
The TEEFail attack could undermine trust in secure computing environments, affecting sectors reliant on confidential computing, such as finance and defense. Economic impacts could arise from increased costs for enhanced security measures. Geopolitically, adversaries could exploit these vulnerabilities for espionage or cyber warfare, escalating tensions.
5. Recommendations and Outlook
- **Immediate Actions**: Develop and deploy software patches to mitigate deterministic encryption vulnerabilities.
- **Long-term Strategies**: Invest in hardware redesigns to prevent physical interposition attacks.
- **Scenario Projections**:
– **Best Case**: Rapid mitigation limits exploitation, maintaining trust in secure computing.
– **Worst Case**: Delayed response leads to widespread breaches and loss of sensitive data.
– **Most Likely**: Partial mitigation with ongoing vulnerabilities requiring continuous monitoring and updates.
6. Key Individuals and Entities
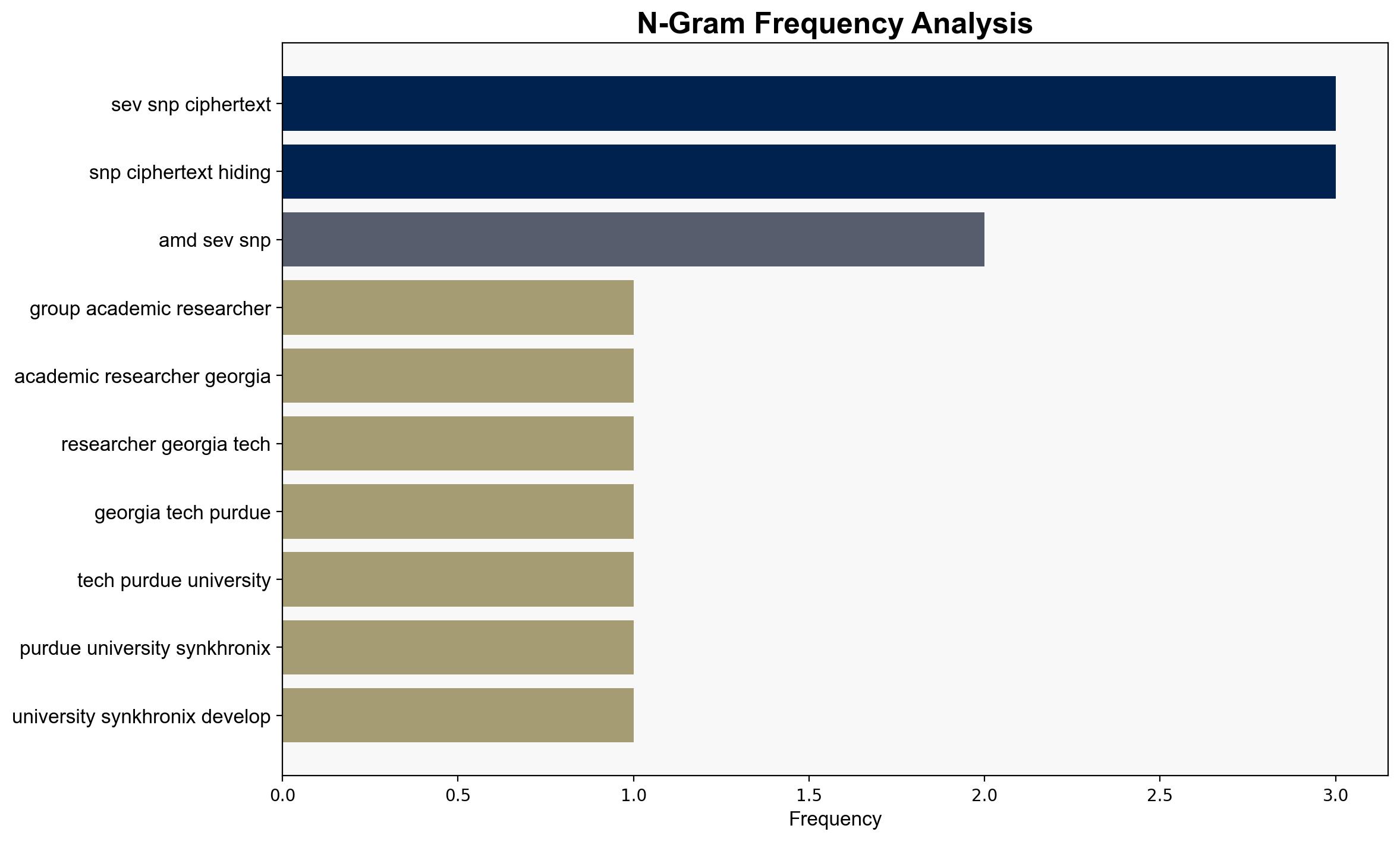
– **Georgia Tech and Purdue University Researchers**: Developers of the TEEFail attack.
– **Synkhronix**: Involved in the development of the attack.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus